Drill down on event details
After running a search that returns events in the Events tab, click on parts of those events to run different kinds of secondary drilldown searches that use the event detail that you have selected.
In the Events tab you can run a drilldown search when you click on these parts of an event:
- Field value. Fields are extracted from events at index time and search time. See "About fields" in the Knowledge Manager Manual.
- Tag. A tag is associated with one or more field-value pairs. A field-value pair can be associated with multiple tags. See About tags and aliases in the Knowledge Manager Manual.
- Segment (can be a connected string of segments). A segment is a searchable part of an event. See "About event segmentation" in the Getting Data In Manual to learn how segments are configured and created.
- Timestamp. A timestamp is date and time information in an event.
Drilldown search actions
The drilldown searches can perform the following actions for fields, tags, and event segments.
| Drilldown search action | Description | Result |
|---|---|---|
| Add to search | Add a focus on the selected event detail to the original search string and run it. Splunk software discards transforming commands from the search string, as well as anything that follows them. | A dataset similar to the one returned by the original search, filtered to include only events that have the selected field, tag, or segment(s). |
| Exclude from search | Add an exclusion of the selected event detail to the original search and run it. Splunk software discards transforming commands from the search string, as well as anything that follows them. | A dataset similar to the one from the original search, filtered to include only events that do not have the selected field, tag, or segment(s). |
| Remove from search | Run a new search that is identical to the original search, except that it no longer searches for the highlighted field value, tag, or segment. Splunk software discards transforming commands from the search string, as well as anything that follows them. | A new dataset that is not as restrictive as the dataset returned by the original search. It no longer excludes events without the highlighted field value, tag, or segment. |
| New search | Run a new search that focuses exclusively on the selected field, tag, or segment(s). | A new dataset that contains any event which includes the selected field, tag, or segment(s). |
Examples of drilldown search actions
| These examples use the sample data from the Search Tutorial but should work with any format of Apache web access log. To try these examples on your own Splunk instance, you must download the sample data and follow the instructions to get the tutorial data into Splunk. Use the time range Last 7 days when you run the searches. |
Add to search
- Run a search or report that returns an event listing in the Events tab.
If your search includes transforming commands, set the Search Mode to Verbose.
Let's start with a basic search that searches the Apache web access log files and looks for HTTP errors that start with 4, such as 404.sourcetype=access_* status=4* - In the search results, expand the event information for the first event.
- Select the
clientipfield value. In this example the value is182.236.164.11.
Because theclientipfield is not currently in the search, the options are: Add to search, Exclude from search, and New search.
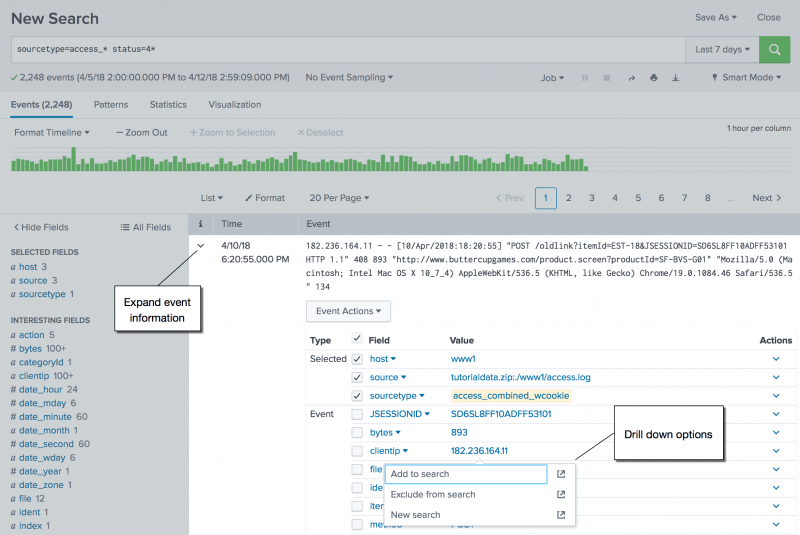
Field values, tags, and segments that are explicitly included in the search string appear with yellow highlighting in the event information. - Click Add to search. The field-value pair is added to the search. The search is run using the same time range.
For example:
sourcetype=access_* status=4* clientip="182.236.164.11"
Remove from search
You can use the Remove from search drilldown option to remove specific criteria. You cannot remove criteria that includes a wildcard.
Continuing with the same search, let's remove the clientip from the search.
- To remove the criteria from the search, expand the event information for the first search result.
- Select the value for the
clientipfield. The drilldown options are Remove from search and New search.
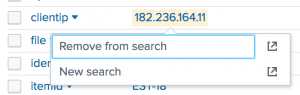
- Click Remove from search. The search is updated and runs using the same time range. For example:
sourcetype=access_* status=4*
Suppose the original search looks like this:
sourcetype=access_* status=404
Expand any event information that contains the status criteria. Click on the value 404 for the status field. From the drilldown options, select Remove from search.
Exclude from search
You can use the Exclude from search drilldown option to exclude a specific criteria from the search.
- Expand the event information for a search result that contains the criteria that you want to exclude.
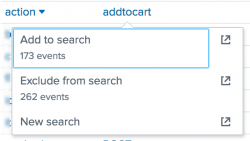
Suppose the original search look like this:sourcetype=access_* status=4*You want to exclude all view actions.
- For the
actionfield, select the view value and click Exclude from search. The field-value pair is added to the search with the not equal to syntax. The search is run using the same time range. For example:sourcetype=access_* status=4* action!=view
Selecting segments
To select event segments or sets of connected segments before you click on them. Splunk software identifies your segment selection with yellow highlighting.
Common values
If the value you select is among the top ten values found for the field, the Add to search and Exclude from search options show event numbers below the option names.
- The event number under Add to search indicates how many events contain the value for the field.
- The event number under Exclude from search indicates how many events do not contain the value for the field.
Run the drilldown search in a new tab
When you select one of the drilldown options, the search is run in the current tab and replaces your current search.
However, you can run the drilldown search in a new tab and leave your current search results intact. To run the drilldown search in a new tab, click the Open In New Tab icon for the option.
Drilldown searches for event timestamps
Event timestamp drilldown searches can help you find event correlations and perform root cause analysis.
Click on an event timestamp to run a secondary search that returns events which are chronologically close to that event.
When you open an event you can also click on the _time field to run this kind of drilldown search.
The controls for this search are called a _time accelerator. See Use time to find nearby events in this manual for details on how the _time accelerator is used.
| Use the timeline to investigate events | Identify event patterns with the Patterns tab |
This documentation applies to the following versions of Splunk® Enterprise: 7.1.0, 7.1.1, 7.1.2, 7.1.3, 7.1.4, 7.1.5, 7.1.6, 7.1.7, 7.1.8, 7.1.9, 7.1.10, 7.2.0, 7.2.1, 7.2.2, 7.2.3, 7.2.4, 7.2.5, 7.2.6, 7.2.7, 7.2.8, 7.2.9, 7.2.10, 7.3.0, 7.3.1, 7.3.2, 7.3.3, 7.3.4, 7.3.5, 7.3.6, 7.3.7, 7.3.8, 7.3.9, 8.0.0, 8.0.1, 8.0.2, 8.0.3, 8.0.4, 8.0.5, 8.0.6, 8.0.7, 8.0.8, 8.0.9, 8.0.10, 8.1.0, 8.1.1, 8.1.2, 8.1.3, 8.1.4, 8.1.5, 8.1.6, 8.1.7, 8.1.8, 8.1.9, 8.1.10, 8.1.11, 8.1.12, 8.1.13, 8.1.14, 8.2.0, 8.2.1, 8.2.2, 8.2.3, 8.2.4, 8.2.5, 8.2.6, 8.2.7, 8.2.8, 8.2.9, 8.2.10, 8.2.11, 8.2.12, 9.0.0, 9.0.1, 9.0.2, 9.0.3, 9.0.4, 9.0.5, 9.0.6, 9.0.7, 9.0.8, 9.0.9, 9.0.10, 9.1.0
 Download manual
Download manual
Feedback submitted, thanks!