top
Description
Finds the most common values for the fields in the field list. Calculates a count and a percentage of the frequency the values occur in the events. If the <by-clause> is included, the results are grouped by the field you specify in the <by-clause>.
Syntax
top [<N>] [<top-options>...] <field-list> [<by-clause>]
Required arguments
- <field-list>
- Syntax: <field>, <field>, ...
- Description: Comma-delimited list of field names.
Optional arguments
- <N>
- Syntax: <int>
- Description: The number of results to return.
- Default: 10
- <top-options>
- Syntax: countfield=<string> | limit=<int> | otherstr=<string> | percentfield=<string> | showcount=<bool> | showperc=<bool> | useother=<bool>
- Description: Options for the
topcommand. See Top options.
- <by-clause>
- Syntax: BY <field-list>
- Description: The name of one or more fields to group by.
Top options
- countfield
- Syntax: countfield=<string>
- Description: For each value returned by the
topcommand, the results also return a count of the events that have that value. This argument specifies the name of the field that contains the count. The count is returned by default. If you do not want to return the count of events, specifyshowcount=false. - Default: count
- limit
- Syntax: limit=<int>
- Description: Specifies how many results to return. To return all values, specify zero ( 0 ). Specifying
top limit=<int>is the same as specifyingtop N. - Default: 10
- otherstr
- Syntax: otherstr=<string>
- Description: If
useother=true, a row representing all other values is added to the results. Useotherstr=<string>to specify the name of the label for the row. - Default: OTHER
- percentfield
- Syntax: percentfield=<string>
- Description: For each value returned by the
topcommand, the results also return a percentage of the events that have that value. This argument specifies the name of the field that contains the percentage. The percentage is returned by default. If you do not want to return the percentage of events, specifyshowperc=false. - Default: percent
- showcount
- Syntax: showcount=<bool>
- Description: Specify whether to create a field called "count" (see "countfield" option) with the count of that tuple.
- Default: true
- showperc
- Syntax: showperc=<bool>
- Description: Specify whether to create a field called "percent" (see "percentfield" option) with the relative prevalence of that tuple.
- Default: true
- useother
- Syntax: useother=<bool>
- Description: Specify whether or not to add a row that represents all values not included due to the limit cutoff.
- Default: false
Usage
The top command is a transforming command. See Command types.
Default fields
When you use the top command, two fields are added to the results: count and percent.
| Field | Description |
|---|---|
count
|
The number of events in your search results that contain the field values that are returned by the top command. See the countfield and showcount arguments.
|
percent
|
The percentage of events in your search results that contain the field values that are returned by the top command. See the percentfield and showperc arguments.
|
Default maximum number of results
By default the top command returns a maximum of 50,000 results.
This maximum is controlled by the maxresultrows setting in the [top] stanza in the limits.conf file. Increasing this limit can result in more memory usage.
Only users with file system access, such as system administrators, can edit the configuration files. Never change or copy the configuration files in the default directory. The files in the default directory must remain intact and in their original location. Make the changes in the local directory.
See How to edit a configuration file.
If you have Splunk Cloud Platform, you need to file a Support ticket to change this limit.
Lexicographic order of results
In searches that use the limit option with multiple sets of field lists, only the last lexicographical value of the <field-list> is returned in the search results. For example, in the following search, Orlando is the only location field that is returned because it's the last value when sorted lexicographically.
| makeresults
| eval location="Orlando Dallas Atlanta"
| makemv location
| mvexpand location
| eval user="Alex Kai Morgan"
| makemv user
| mvexpand user
| top limit=1 location by user
The search results look something like this.
| user | location | count | percent |
|---|---|---|---|
| Alex | Orlando | 1 | 33.333333 |
| Kai | Orlando | 1 | 33.333333 |
| Morgan | Orlando | 1 | 33.333333 |
Examples
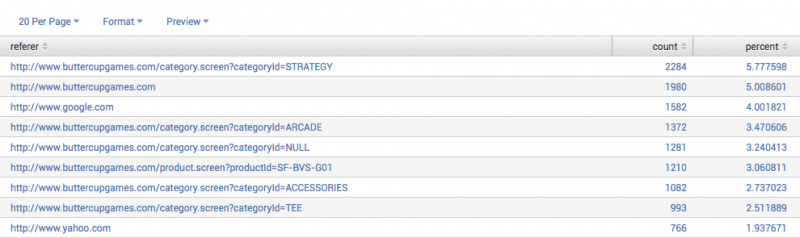
Example 1: Return the 20 most common values for a field
This search returns the 20 most common values of the "referer" field. The results show the number of events (count) that have that a count of referer, and the percent that each referer is of the total number of events.
sourcetype=access_* | top limit=20 referer
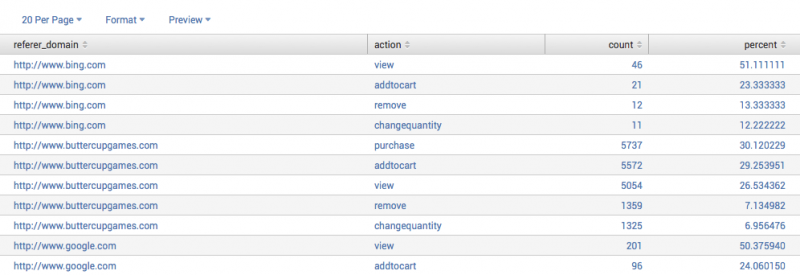
Example 2: Return top values for one field organized by another field
This search returns the top "action" values for each "referer_domain".
sourcetype=access_* | top action by referer_domain
Because a limit is not specified, this returns all the combinations of values for "action" and "referer_domain" as well as the counts and percentages:
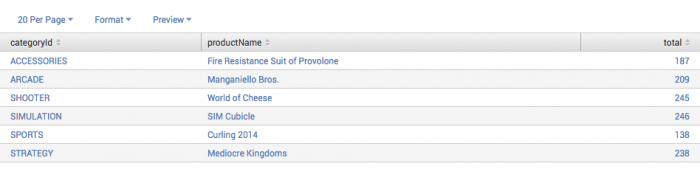
Example 3: Returns the top product purchased for each category
This example uses the sample dataset from the Search Tutorial and a field lookup to add more information to the event data.
After you configure the field lookup, you can run this search using the time range, All time. |
This search returns the top product purchased for each category. Do not show the percent field. Rename the count field to "total".
sourcetype=access_* status=200 action=purchase | top 1 productName by categoryId showperc=f countfield=total
See also
| timewrap | transaction |
This documentation applies to the following versions of Splunk® Enterprise: 7.0.0, 7.0.1, 7.0.2, 7.0.3, 7.0.4, 7.0.5, 7.0.6, 7.0.7, 7.0.8, 7.0.9, 7.0.10, 7.0.11, 7.0.13, 7.1.0, 7.1.1, 7.1.2, 7.1.3, 7.1.4, 7.1.5, 7.1.6, 7.1.7, 7.1.8, 7.1.9, 7.1.10, 7.2.0, 7.2.1, 7.2.2, 7.2.3, 7.2.4, 7.2.5, 7.2.6, 7.2.7, 7.2.8, 7.2.9, 7.2.10, 7.3.0, 7.3.1, 7.3.2, 7.3.3, 7.3.4, 7.3.5, 7.3.6, 7.3.7, 7.3.8, 7.3.9, 8.0.0, 8.0.1, 8.0.2, 8.0.3, 8.0.4, 8.0.5, 8.0.6, 8.0.7, 8.0.8, 8.0.9, 8.0.10, 8.1.0, 8.1.1, 8.1.2, 8.1.3, 8.1.4, 8.1.5, 8.1.6, 8.1.7, 8.1.8, 8.1.9, 8.1.10, 8.1.11, 8.1.12, 8.1.13, 8.1.14, 8.2.0, 8.2.1, 8.2.2, 8.2.3, 8.2.4, 8.2.5, 8.2.6, 8.2.7, 8.2.8, 8.2.9, 8.2.10, 8.2.11, 8.2.12, 9.0.0, 9.0.1, 9.0.2, 9.0.3, 9.0.4, 9.0.5, 9.0.6, 9.0.7, 9.0.8, 9.0.9, 9.0.10, 9.1.0, 9.1.1, 9.1.2, 9.1.3, 9.1.4, 9.1.5, 9.1.6, 9.1.7, 9.1.8, 9.1.9, 9.2.0, 9.2.1, 9.2.2, 9.2.3, 9.2.4, 9.2.5, 9.2.6, 9.3.0, 9.3.1, 9.3.2, 9.3.3, 9.3.4, 9.4.0, 9.4.1, 9.4.2
 Download manual
Download manual
Feedback submitted, thanks!