Deploy a distributed search environment
Important: The topics in this chapter explain how to deploy a non-clustered distributed search topology. For information on deploying a search head cluster instead, read the chapter Deploy search head clustering.
The basic configuration to enable distributed search is simple. You designate one Splunk Enterprise instance as the search head and establish connections from the search head to one or more search peers, or indexers.
If you need to deploy more than a single search head, the best practice is to deploy the search heads in a search head cluster.
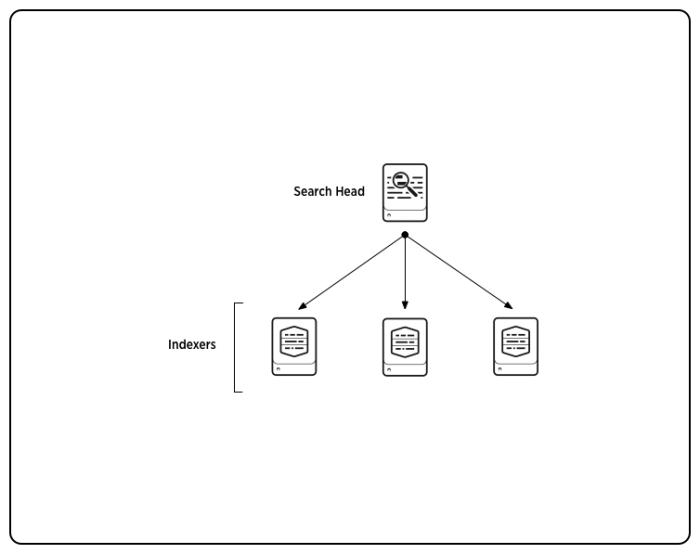
This is the type of topology that this topic specifically addresses:
The search head interfaces with the user and manages searches across the set of indexers. The indexers index incoming data and search the data, as directed by the search head.
Deploy distributed search
To set up a simple distributed search topology, consisting of a single dedicated search head and several search peers, perform these steps:
1. Identify your requirements. See System requirements and other deployment considerations for distributed search.
2. Designate a Splunk Enterprise instance as the search head. Since distributed search is enabled automatically on every full Splunk Enterprise instance, you do not actually perform any action in this step, aside from choosing the instance that you want to be your search head.
Choose an existing instance that is not indexing external data or install a new instance. For installation information, see the topic in the Installation Manual specific to your operating system.
3. Establish connections from the search head to all the search peers that you want it to search across. This is the key step in the procedure. See Add search peers to the search head.
4. Add data inputs to the search peers. You add inputs in the same way as for any indexer, either directly on the search peer or through forwarders connecting to the search peer. See the Getting Data In manual for information on data inputs.
5. Forward the search head's internal data to the search peers. See Best practice: Forward search head data to the indexer layer.
6. Log in to the search head and perform a search that runs across all the search peers, such as a search for *. Examine the splunk_server field in the results. Verify that all the search peers are listed in that field.
7. See the Securing Splunk Enterprise manual for information on setting up authentication.
To increase indexing capacity, deploy additional search peers. To increase the search management capacity, deploy multiple search heads as members of a search head cluster.
Deploy multiple search heads
To deploy multiple search heads, the best practice is to deploy the search heads in a search head cluster. This provides numerous advantages, including simplified scaling and management. See the chapter Deploy search head clustering.
Deploy search heads in indexer clusters
Splunk indexer clusters use search heads to search across their set of indexers, or peer nodes. You deploy search heads very differently when they are part of an indexer cluster. To learn about deploying search heads in indexer clusters, read Enable the search head in the Managing Indexers and Clusters of Indexers manual.
| Troubleshoot knowledge bundle replication | System requirements and other deployment considerations for distributed search |
This documentation applies to the following versions of Splunk® Enterprise: 7.0.0, 7.0.1, 7.0.2, 7.0.3, 7.0.4, 7.0.5, 7.0.6, 7.0.7, 7.0.8, 7.0.9, 7.0.10, 7.0.11, 7.0.13, 7.1.0, 7.1.1, 7.1.2, 7.1.3, 7.1.4, 7.1.5, 7.1.6, 7.1.7, 7.1.8, 7.1.9, 7.1.10, 7.2.0, 7.2.1, 7.2.2, 7.2.3, 7.2.4, 7.2.5, 7.2.6, 7.2.7, 7.2.8, 7.2.9, 7.2.10, 7.3.0, 7.3.1, 7.3.2, 7.3.3, 7.3.4, 7.3.5, 7.3.6, 7.3.7, 7.3.8, 7.3.9, 8.0.0, 8.0.1, 8.0.2, 8.0.3, 8.0.4, 8.0.5, 8.0.6, 8.0.7, 8.0.8, 8.0.9, 8.0.10, 8.1.0, 8.1.1, 8.1.2, 8.1.3, 8.1.4, 8.1.5, 8.1.6, 8.1.7, 8.1.8, 8.1.9, 8.1.10, 8.1.11, 8.1.12, 8.1.13, 8.1.14, 8.2.0, 8.2.1, 8.2.2, 8.2.3, 8.2.4, 8.2.5, 8.2.6, 8.2.7, 8.2.8, 8.2.9, 8.2.10, 8.2.11, 8.2.12, 9.0.0, 9.0.1, 9.0.2, 9.0.3, 9.0.4, 9.0.5, 9.0.6, 9.0.7, 9.0.8, 9.0.9, 9.0.10, 9.1.0, 9.1.1, 9.1.2, 9.1.3, 9.1.4, 9.1.5, 9.1.6, 9.1.7, 9.1.8, 9.1.9, 9.2.0, 9.2.1, 9.2.2, 9.2.3, 9.2.4, 9.2.5, 9.2.6, 9.3.0, 9.3.1, 9.3.2, 9.3.3, 9.3.4, 9.4.0, 9.4.1, 9.4.2
 Download manual
Download manual
Feedback submitted, thanks!