Departmental deployment: Single indexer
A single Splunk Enterprise instance, serving as both indexer and search head, usually meets the indexing and search needs of a single department within a larger organization. You typically also install forwarders on the data-generating hosts. The forwarders feed data from the hosts to the indexer.
This topic describes how to implement a deployment consisting of:
- One combined indexer/search head
- Multiple forwarders
Use case
Characteristics of this type of deployment include:
- Indexing volume of under 20GB/day.
- A few users, typically less than 10.
- A relatively small number of forwarders sending data to the instance, typically less than 10 and rarely exceeding 100.
For details on the characteristics of a departmental deployment, see "Types of deployments."
Architecture
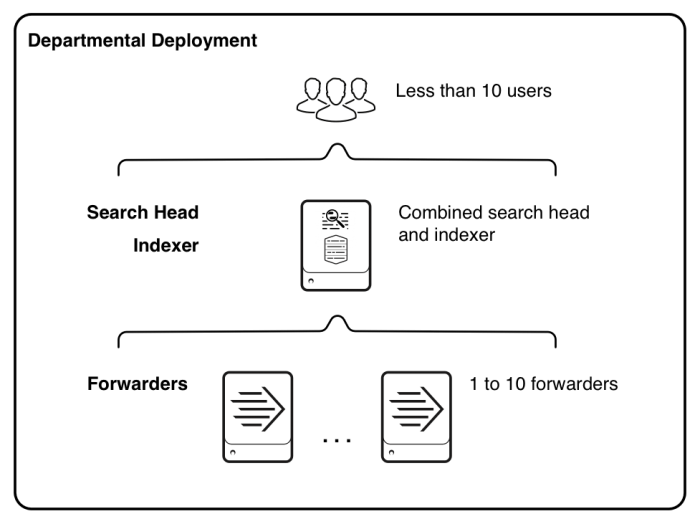
This diagram shows a high-level view of the architecture for this type of deployment:
Starting from the bottom, the diagram illustrates the tiers of processing:
- Data input. Data enters the system through forwarders, which consume external data, perform a small amount of preprocessing on it, and then forward the data to the indexer. In a departmental deployment, you typically have fewer than ten forwarders, although, for some use cases, you might have as many as 100.
- Indexing and searching (combined). A single indexer receives, indexes, and stores incoming data from the forwarders. The indexer also doubles as a search head. In that capacity, it handles search requests, such as ad hoc requests from users and saved search requests. The search head provides the user with various tools, such as dashboards, to assist the search experience.
Implementation framework
To implement this type of scenario:
1. Install one Splunk Enterprise instance to serve as the combined indexer/search head. For installation instructions, see "Installation overview" in the Installation Manual.
2. Configure the Splunk Enterprise license. See "How Splunk Enterprise licensing works" in the Admin Manual.
3. Configure the instance's receiving port. The forwarders send data to the indexer through this port. See "Enable a receiver" in the Forwarding Data manual.
4. Install universal forwarders on the machines hosting your data sources, and configure the forwarders to send data to the Splunk Enterprise instance. How you do this depends on your needs and preferences, as well as on how many forwarders you are deploying. For example:
- You can install forwarders one-by-one or simultaneously across many machines.
- You can install forwarders and then configure them later, or install and configure forwarders at the same time.
- You can configure forwarders either manually or by means of the deployment server or third-party software.
For information on installing and configuring universal forwarders, see Install the universal forwarder software in the Splunk Universal Forwarder Manual.
5. Configure the inputs to the forwarders, so that data begins to enter the system. See "Configure your inputs" in the Getting Data In manual.
Next steps
Once you have your Splunk Enterprise instance up and running, you can further refine your system and prepare the data and its presentation for the benefit of your end users. For a summary of the types of activities you need to perform now, see "Post-deployment activities."
To scale further
To increase your indexing and search capacity, the first step is to separate the indexing function from the search management function. To do this, add a second Splunk Enterprise instance to serve as a dedicated search head. Once you have a dedicated search head, you can boost indexing capacity by adding more indexers. See "Small enterprise deployment: single search head with multiple indexers."
For guidance on determining when to add more instances, and whether to add only indexers, or both indexers and search heads, see:
- "Types of deployments" in this manual.
- Summary of performance recommendations" in the Capacity Planning manual.
| Types of distributed deployments | Small enterprise deployment: Single search head with multiple indexers |
This documentation applies to the following versions of Splunk® Enterprise: 7.0.0, 7.0.1, 7.0.2, 7.0.3, 7.0.4, 7.0.5, 7.0.6, 7.0.7, 7.0.8, 7.0.9, 7.0.10, 7.0.11, 7.0.13, 7.1.0, 7.1.1, 7.1.2, 7.1.3, 7.1.4, 7.1.5, 7.1.6, 7.1.7, 7.1.8, 7.1.9, 7.1.10, 7.2.0, 7.2.1, 7.2.2, 7.2.3, 7.2.4, 7.2.5, 7.2.6, 7.2.7, 7.2.8, 7.2.9, 7.2.10, 7.3.0, 7.3.1, 7.3.2, 7.3.3, 7.3.4, 7.3.5, 7.3.6, 7.3.7, 7.3.8, 7.3.9, 8.0.0, 8.0.1, 8.0.2, 8.0.3, 8.0.4, 8.0.5, 8.0.6, 8.0.7, 8.0.8, 8.0.9, 8.0.10, 8.1.0, 8.1.1, 8.1.2, 8.1.3, 8.1.4, 8.1.5, 8.1.6, 8.1.7, 8.1.8, 8.1.9, 8.1.10, 8.1.11, 8.1.12, 8.1.13, 8.1.14, 8.2.0, 8.2.1, 8.2.2, 8.2.3, 8.2.4, 8.2.5
 Download manual
Download manual
Feedback submitted, thanks!