Sample platform instrumentation searches
This topic introduces a few examples of analysis you can perform using Splunk Enterprise platform instrumentation. Read About Splunk Enterprise platform instrumentation for an introduction to the feature.
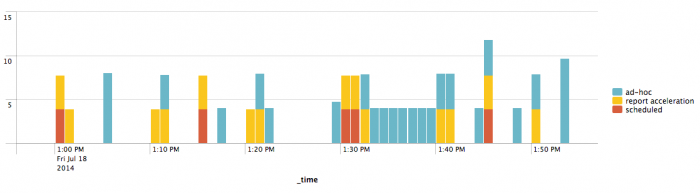
Aggregate median physical memory usage per search type
Use this search to find the median total physical memory used in MB, per search type (ad hoc, scheduled, report acceleration, data model acceleration, or summary indexing) for one host over the last hour:
index=_introspection host=<hostname> data.search_props.sid=* earliest=-1h | bin _time span=10s|stats latest(data.mem_used) as mem_used by data.search_props.sid, data.search_props.type, _time | stats sum(mem_used) as mem_used by data.search_props.sid, data.search_props.type, _time | timechart median(mem_used) by data.search_props.type
As a stacked column chart, this search produces a visualization that looks like this:
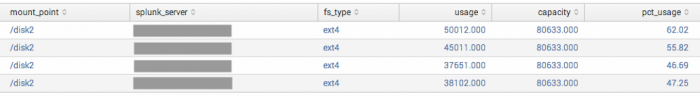
Current disk usage per partition in use by Splunk Enterprise
Use this search to find the latest value of Splunk Enterprise disk usage per partition and instance:
| rest /services/server/status/partitions-space | eval usage = capacity - free
| eval pct_usage = round(usage / capacity * 100, 2)
| stats first(fs_type) as fs_type first(usage) as usage first(capacity) as capacity
first(pct_usage) as pct_usage by mount_point, splunk_server
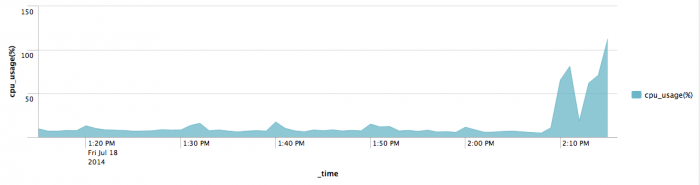
Median CPU usage for the main splunkd process for one host
Use this search to find the median CPU usage of the main splunkd process for one host over the last hour:
index=_introspection component=PerProcess host=<hostname> data.process=splunkd (data.args="-p * start" OR data.args="service") earliest=-1h | timechart median(data.pct_cpu) as cpu_usage(%)
Fill in "<hostname>" with the "host" metadata field associated with your instance, as recorded in inputs.conf's "host" property. As an area chart, this search produces something like this:
Median search concurrency by search mode for all instances
Use this search to find the median number of searches running at any given time, split by mode (historical, historical batch, real-time, or real-time indexed):
index=_introspection data.search_props.sid=* earliest=-1h | bin _time span=10s|stats dc(data.search_props.sid) as search_count by data.search_props.mode, _time | timechart median(search_count) by data.search_props.mode
Peak splunkweb file descriptor usage over time for one instance
index=_introspection component=PerProcess host="<hostname>"
(data.process="python*" data.args="*/mrsparkle/root.py*")
OR data.process=splunkweb
| timechart max(data.fd_used) as fd_used
Fill in "<hostname>" with the "host" metadata field associated with your instance, as recorded in inputs.conf's "host" property.
| Configure platform instrumentation | Contact Support |
This documentation applies to the following versions of Splunk® Enterprise: 7.0.0, 7.0.1, 7.0.2, 7.0.3, 7.0.4, 7.0.5, 7.0.6, 7.0.7, 7.0.8, 7.0.9, 7.0.10, 7.0.11, 7.0.13, 7.1.0, 7.1.1, 7.1.2, 7.1.3, 7.1.4, 7.1.5, 7.1.6, 7.1.7, 7.1.8, 7.1.9, 7.1.10, 7.2.0, 7.2.1, 7.2.2, 7.2.3, 7.2.4, 7.2.5, 7.2.6, 7.2.7, 7.2.8, 7.2.9, 7.2.10, 7.3.0, 7.3.1, 7.3.2, 7.3.3, 7.3.4, 7.3.5, 7.3.6, 7.3.7, 7.3.8, 7.3.9, 8.0.0, 8.0.1, 8.0.2, 8.0.3, 8.0.4, 8.0.5, 8.0.6, 8.0.7, 8.0.8, 8.0.9, 8.0.10, 8.1.0, 8.1.1, 8.1.2, 8.1.3, 8.1.4, 8.1.5, 8.1.6, 8.1.7, 8.1.8, 8.1.9, 8.1.10, 8.1.11, 8.1.12, 8.1.13, 8.1.14, 8.2.0, 8.2.1, 8.2.2, 8.2.3, 8.2.4, 8.2.5, 8.2.6, 8.2.7, 8.2.8, 8.2.9, 8.2.10, 8.2.11, 8.2.12, 9.0.0, 9.0.1, 9.0.2, 9.0.3, 9.0.4, 9.0.5, 9.0.6, 9.0.7, 9.0.8, 9.0.9, 9.0.10, 9.1.0, 9.1.1, 9.1.2, 9.1.3, 9.1.4, 9.1.5, 9.1.6, 9.1.7, 9.1.8, 9.1.9, 9.2.0, 9.2.1, 9.2.2, 9.2.3, 9.2.4, 9.2.5, 9.2.6, 9.3.0, 9.3.1, 9.3.2, 9.3.3, 9.3.4, 9.4.0, 9.4.1, 9.4.2
 Download manual
Download manual
Feedback submitted, thanks!