How the Splunk platform handles syslog data over the UDP network protocol
If you run Splunk Cloud Platform, you can configure the Splunk universal forwarder to listen on a User Datagram Protocol (UDP) network port and forward that data to your Splunk Cloud Platform deployment.
Splunk Enterprise indexers can act as syslog servers that handle incoming data streams that comply with the syslog messaging standard. Splunk Enterprise can also act as a syslog message sender. Splunk Cloud Platform cannot send syslog messages, nor can it move messages from one device to another.
How the Splunk platform handles syslog inputs
When you configure a UDP network input to listen to a syslog-standard data stream on Splunk Enterprise or the universal forwarder, any syslog events that arrive through the input receive a timestamp and connected host field. The platform prepends these fields to each event before it indexes them. When you configure a universal forwarder to send data to Splunk Cloud Platform, Splunk Cloud Platform indexes the fields as it receives them from the universal forwarder.
The Splunk platform does not modify Transmission Control Protocol (TCP) network packets in this fashion. If you send syslog data over TCP, the platform does not strip priority information from the events. It does, however, prepend a host name and timestamp to the event unless you configure it not to. One TCP source stream will be assigned to one data pipeline and any others, so you should adjust for scalability.
How Splunk Enterprise handles syslog outputs
The follow section applies to Splunk Enterprise only. Neither Splunk Cloud Platform nor the universal forwarder has the capability to forward events to another syslog server.
Splunk Enterprise can forward events to another syslog server. When it does, it prepends the priority information to the event so that the downstream syslog server can translate the events properly.
When the event reaches the downstream syslog server, that machine prepends a timestamp, priority, and connected host name, which is the Splunk Enterprise instance, to the event.
You can also prepend a timestamp and host name to the event at the time you forward the event to the syslog server. You do this as part of modifying the data as it leaves the Splunk Enterprise instance.
For information on configuring routing, filtering, and usage of source types, see Route and filter data in the Splunk Enterprise Forwarding Data manual and the props.conf spec file in the Admin Manual.
How Splunk Enterprise moves syslog events when you configure it to use syslog source type
The following section applies to Splunk Enterprise only. Splunk Cloud Platform isn't able to send syslog events to another downstream syslog server.
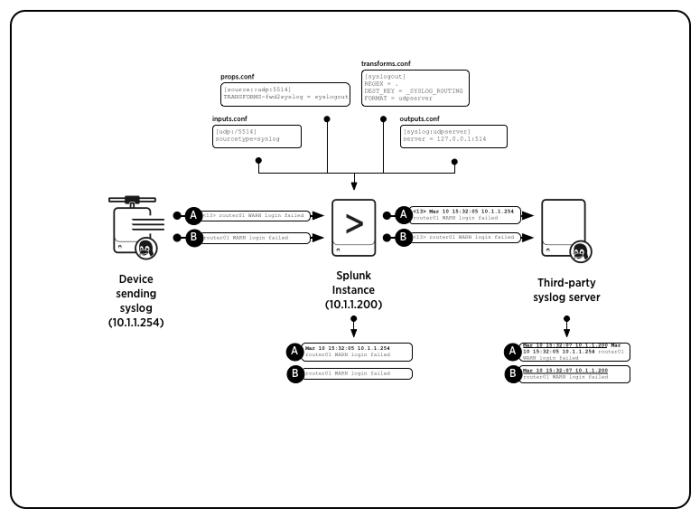
The following diagram shows how Splunk Enterprise moves two syslog messages from one syslog server to another. In the diagram, Splunk Enterprise listens on a UDP network port and indexes incoming events. On the other side, the same instance forwards events to a third-party syslog server.
In the diagram, Message A originates as a syslog event and Message B originates as a similar event that does not have priority information associated with it. Upon receipt, Splunk Enterprise tags the events with a timestamp and the host that generated the event.
If you configured the instance as a forwarder, Splunk Enterprise then transforms the events by adding a priority header that you specify in the outputs.conf file before it forwards the events on to the syslog server. Once they arrive at the syslog server, that server prepends the timestamp and host data to the events as it received them from the Splunk Enterprise instance.
How Splunk Enterprise moves syslog events when you configure a custom source type
The following section applies to Splunk Enterprise only. Splunk Cloud Platform isn't able to move syslog events.
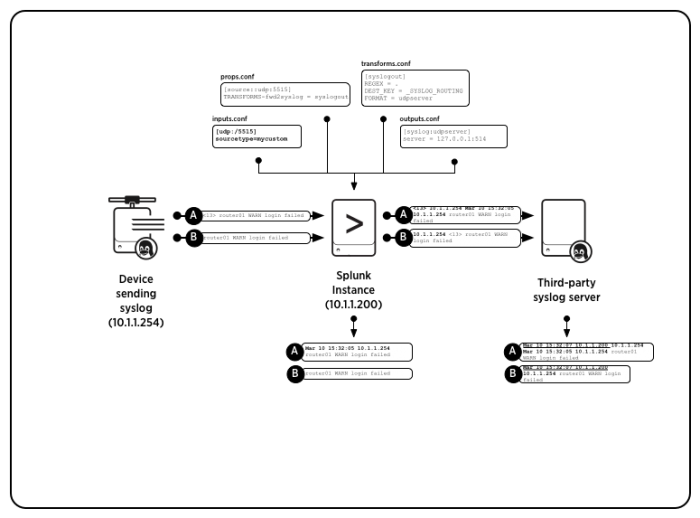
In this diagram, Splunk Enterprise has been configured to use a non-syslog source type. The initial Messages A and B are identical to the first example. In this example, Splunk Enterprise prepends the event with an originating host name or IP address.
How Splunk Enterprise moves syslog events when you configure it with a timestamp
The following section applies to Splunk Enterprise only. Splunk Cloud Platform isn't able to move syslog events.
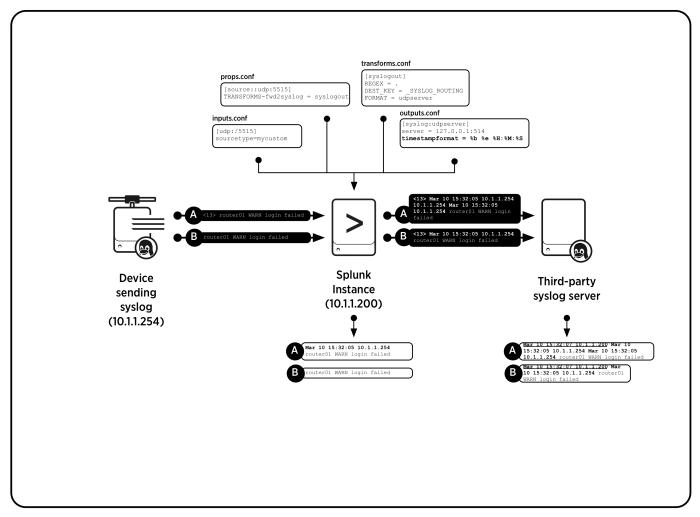
You can also configure Splunk Enterprise to add timestamps to syslog events when you forward those events. You could add a timestamp to the events when you don't want the downstream server to add its own timestamp.
The following diagram shows the required attribute and depicts how Splunk Enterprise deals with the data. The initial Messages A and B are identical to the first and second examples. Splunk Enterprise prepends the events with a timestamp and an originating host name or IP address.
Caveats to using Splunk Enterprise as a syslog server or message sender
The following section applies to Splunk Enterprise only. Splunk Cloud Platform isn't able to be used as a syslog server or message sender.
While you can configure Splunk Enterprise to receive syslog events directly, refrain from doing so for the following reasons:
- Splunk best practice involves setting up a separate machine that runs a syslog service to handle syslog tasks.
- The Splunk platform modifies syslog data by default as part of the indexing process. It assigns a timestamp and a host to the event.
- Syslog data streams to only one Splunk Enterprise instance in this scenario. In a deployment with multiple indexers, you must perform additional work to distribute the streams across those indexers
- If Splunk Enterprise or fails for any reason, any syslog messages that arrive during the downtime can be irrecoverably lost.
Don't substitute Splunk Enterprise for a syslog server in regular use unless you have no other options.
If you must retain raw syslog data, such as when a data retention policy requires access to untouched events, consider using a tool such as syslog-ng to simultaneously save the raw data to a log file and forward those events to your Splunk Enterprise instance. These tools give you the advantage of indexing the log file later if you want.
| Get data from TCP and UDP ports | Send SNMP events to your Splunk deployment |
This documentation applies to the following versions of Splunk® Enterprise: 7.0.0, 7.0.1, 7.0.2, 7.0.3, 7.0.4, 7.0.5, 7.0.6, 7.0.7, 7.0.8, 7.0.9, 7.0.10, 7.0.11, 7.0.13, 7.1.0, 7.1.1, 7.1.2, 7.1.3, 7.1.4, 7.1.5, 7.1.6, 7.1.7, 7.1.8, 7.1.9, 7.1.10, 7.2.0, 7.2.1, 7.2.2, 7.2.3, 7.2.4, 7.2.5, 7.2.6, 7.2.7, 7.2.8, 7.2.9, 7.2.10, 7.3.0, 7.3.1, 7.3.2, 7.3.3, 7.3.4, 7.3.5, 7.3.6, 7.3.7, 7.3.8, 7.3.9, 8.0.0, 8.0.1, 8.0.2, 8.0.3, 8.0.4, 8.0.5, 8.0.6, 8.0.7, 8.0.8, 8.0.9, 8.0.10, 8.1.0, 8.1.1, 8.1.2, 8.1.3, 8.1.4, 8.1.5, 8.1.6, 8.1.7, 8.1.8, 8.1.9, 8.1.10, 8.1.11, 8.1.12, 8.1.13, 8.1.14, 8.2.0, 8.2.1, 8.2.2, 8.2.3, 8.2.4, 8.2.5, 8.2.6, 8.2.7, 8.2.8, 8.2.9, 8.2.10, 8.2.11, 8.2.12, 9.0.0, 9.0.1, 9.0.2, 9.0.3, 9.0.4, 9.0.5, 9.0.6, 9.0.7, 9.0.8, 9.0.9, 9.0.10, 9.1.0, 9.1.1, 9.1.2, 9.1.3, 9.1.4, 9.1.5, 9.1.6, 9.1.7, 9.1.8, 9.1.9, 9.2.0, 9.2.1, 9.2.2, 9.2.3, 9.2.4, 9.2.5, 9.2.6, 9.3.0, 9.3.1, 9.3.2, 9.3.3, 9.3.4, 9.4.0, 9.4.1, 9.4.2
 Download manual
Download manual
Feedback submitted, thanks!