Lookup example in Splunk Web
This example defines a file-based CSV lookup that adds two fields, status_description and status_type, to your web access events. This lets you search for events when you do not know the specific error code. Instead of searching for all server error codes, use status="Server Error".
Upload the lookup table to the Splunk platform
Prerequisities
- See Define a CSV lookup in Splunk Web.
- Download the
http_status.csvfile: http_status.csv file. - Your role must have the upload_lookup_files capability. Without it you cannot upload lookup table files in Splunk Web.
- If you use Splunk Enterprise, see Define roles on the Splunk platform with capabilities in Securing Splunk Enterprise.
- If you use Splunk Cloud Platform, see Define roles on the Splunk platform with capabilities in Securing Splunk Cloud Platform.
The following is a sample of the file:
status,status_description,status_type 100,Continue,Informational 101,Switching Protocols,Informational 200,OK,Successful 201,Created,Successful 202,Accepted,Successful 203,Non-Authoritative Information,Successful ...
Steps
- From the Search app, then select Settings > Lookups.
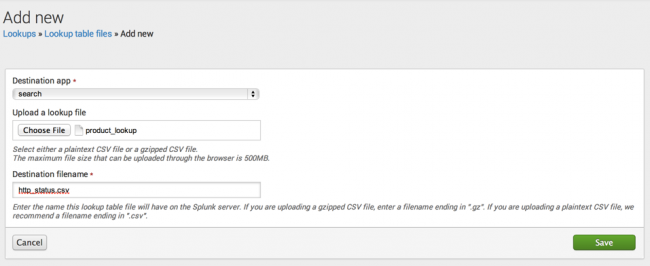
- Select Add new for Lookup table files.
- Select search for the destination app.
- Browse for the CSV file that you downloaded earlier.
- Provide a Destination filename of http_status.csv.
- Click Save.
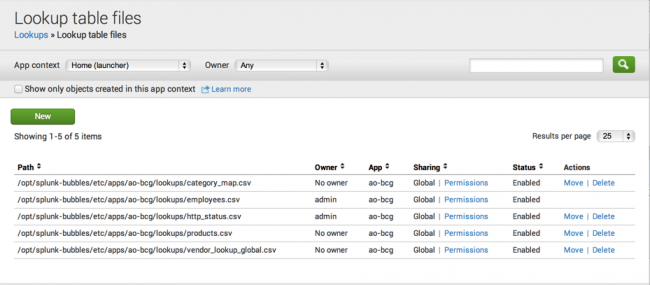
After your Splunk platform deployment saves the file, it takes you to the following view:
Define the lookup
Prerequisites
Steps
- From Settings > Lookups, select Add new for Lookup definitions.
- Select search for the Destination app.
- Name your lookup definition http_status.
- Select File-based under Type.
- From the Lookup file dropdown, select http_status.csv.
- Click Save.
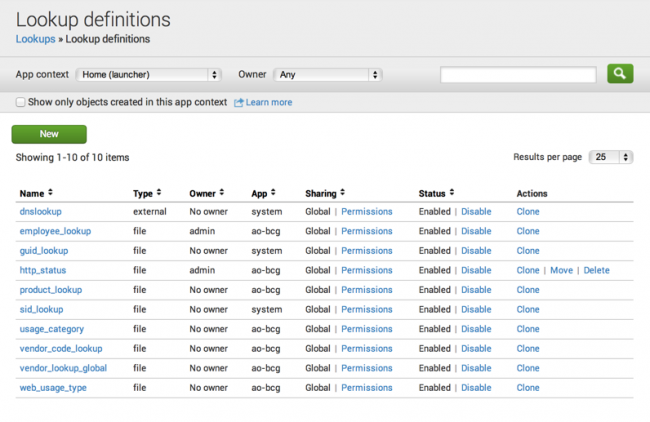
Notice there are some actions you can take on your lookup definition. Permissions lets you change the accessibility of the lookup table. You can Disable, Clone, and Move the lookup definition to a different app. Or, you can Delete the definition. Once you define the lookup, you can use thelookupcommand to invoke it in a search or you can configure the lookup to run automatically.
Set the lookup to run automatically
Prerequisites
Steps
- Return to the Settings > Lookups view and select Add new for Automatic lookups.
- In the Add new page:
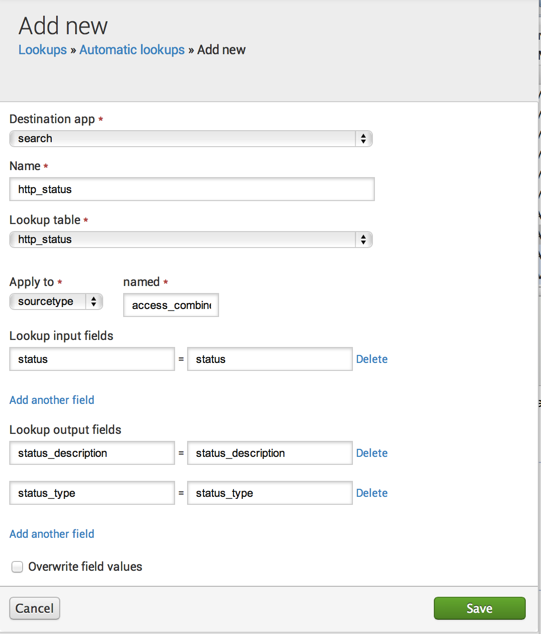
- Select search for the Destination app.
- Name the lookup http_status.
- Select
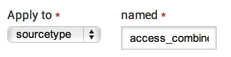
http_statusfrom the Lookup table drop down. - Apply the lookup to the
sourcetypenamedaccess_combined.
- Lookup input fields are the fields in our events that you want to match with the lookup table. Here, both are named
status(the CSV column name goes on the left and the field that you want to match goes on the right):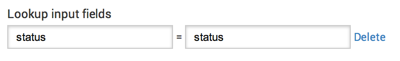
- Lookup output fields are the fields from the lookup table that you want to add to your events:
status_descriptionandstatus_type. The CSV column name goes on the left and the field that you want to match goes on the right.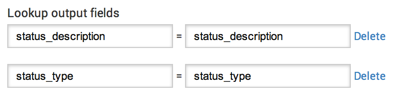
- Click Save.
| Define an automatic lookup in Splunk Web | Introduction to lookup configuration |
This documentation applies to the following versions of Splunk® Enterprise: 7.3.0, 7.3.1, 7.3.2, 7.3.3, 7.3.4, 7.3.5, 7.3.6, 7.3.7, 7.3.8, 7.3.9, 8.0.0, 8.0.1, 8.0.2, 8.0.3, 8.0.4, 8.0.5, 8.0.6, 8.0.7, 8.0.8, 8.0.9, 8.0.10, 8.1.0, 8.1.1, 8.1.2, 8.1.3, 8.1.4, 8.1.5, 8.1.6, 8.1.7, 8.1.8, 8.1.9, 8.1.10, 8.1.11, 8.1.12, 8.1.13, 8.1.14, 8.2.0, 8.2.1, 8.2.2, 8.2.3, 8.2.4, 8.2.5, 8.2.6, 8.2.7, 8.2.8, 8.2.9, 8.2.10, 8.2.11, 8.2.12, 9.0.0, 9.0.1, 9.0.2, 9.0.3, 9.0.4, 9.0.5, 9.0.6, 9.0.7, 9.0.8, 9.0.9, 9.0.10, 9.1.0, 9.1.1, 9.1.2, 9.1.3, 9.1.4, 9.1.5, 9.1.6, 9.1.7, 9.1.8, 9.1.9, 9.2.0, 9.2.1, 9.2.2, 9.2.3, 9.2.4, 9.2.5, 9.2.6, 9.3.0, 9.3.1, 9.3.2, 9.3.3, 9.3.4, 9.4.0, 9.4.1, 9.4.2
 Download manual
Download manual
Feedback submitted, thanks!