About event type priorities
You can give your event type a Priority. The Priority value that you select for an event type affects the display of events that match that event type, when those events also match other event types. For information on event types, see Define event types.
Priority affects the event type listing order in expanded events.
Event type matching takes place at search time. When you run a search and an event returned by that search matches an event type, Splunk software adds the corresponding eventtype field/value pair to it, where the value is the event type name.
You can see the event types that have been added to an event when you review your search results. Expand the event and check to see if the eventtype field is listed. If you see it, the event matches at least one event type.
If the event matches two or more event types, eventtype becomes a multivalued field whose values are ordered alphabetically, with the exception of event types that have a Priority setting. Event types with a Priority setting are listed above the event types without one, and they are ordered according to their Priority value.
If you have a number of overlapping event types, or event types that are subsets of larger ones, you may want to give the precisely focused event types a better priority. For example, you could easily have a set of events that are part of a wide-ranging all_system_errors event type. Within that large set of events, you could have events that also belong to more precisely focused event types like critical_disc_error and bad_external_resource_error.
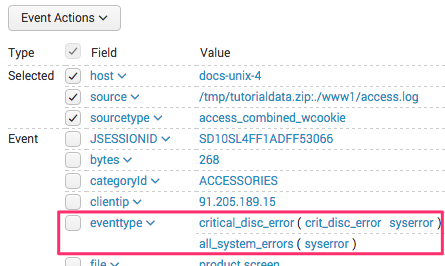
Here is an example of an event that matches the all_system_errors and critical_disc_error event types.
In this example, the critical_disk_error event type has a priority of 3 while the all_system_errors event type has a priority of 7. 3 is a better priority value than 7, so critical_disk_error appears first in the list order.
Priority determines which event type color displays for an event
Only one event type color can be displayed for each event. When an event matches multiple event types, the Color for the event type with the best Priority value is displayed. However, for event types grouped with the transaction command, no color is displayed.
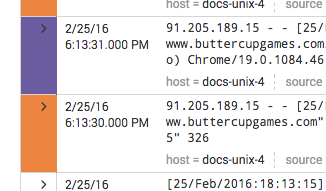
Following from the previous example, here is an example of two events with event type coloration.
Both events match the all_system_errors event type, which has a Color value of Orange. Events that have all_system_errors as the dominant event type display with orange event type coloration. One of the events also matches the critical_disk_error event type, which has a better Priority than all_system_errors. The critical_disk_error event type has Color set to Purple, so the event that matches it has purple event type coloration instead of orange.
| Define event types in Splunk Web | Automatically find and build event types |
This documentation applies to the following versions of Splunk® Enterprise: 7.0.0, 7.0.1, 7.0.2, 7.0.3, 7.0.4, 7.0.5, 7.0.6, 7.0.7, 7.0.8, 7.0.9, 7.0.10, 7.0.11, 7.0.13, 7.1.0, 7.1.1, 7.1.2, 7.1.3, 7.1.4, 7.1.5, 7.1.6, 7.1.7, 7.1.8, 7.1.9, 7.1.10, 7.2.0, 7.2.1, 7.2.2, 7.2.3, 7.2.4, 7.2.5, 7.2.6, 7.2.7, 7.2.8, 7.2.9, 7.2.10, 7.3.0, 7.3.1, 7.3.2, 7.3.3, 7.3.4, 7.3.5, 7.3.6, 7.3.7, 7.3.8, 7.3.9, 8.0.0, 8.0.1, 8.0.2, 8.0.3, 8.0.4, 8.0.5, 8.0.6, 8.0.7, 8.0.8, 8.0.9, 8.0.10, 8.1.0, 8.1.1, 8.1.2, 8.1.3, 8.1.4, 8.1.5, 8.1.6, 8.1.7, 8.1.8, 8.1.9, 8.1.10, 8.1.11, 8.1.12, 8.1.13, 8.1.14, 8.2.0, 8.2.1, 8.2.2, 8.2.3, 8.2.4, 8.2.5, 8.2.6, 8.2.7, 8.2.8, 8.2.9, 8.2.10, 8.2.11, 8.2.12, 9.0.0, 9.0.1, 9.0.2, 9.0.3, 9.0.4, 9.0.5, 9.0.6, 9.0.7, 9.0.8, 9.0.9, 9.0.10, 9.1.0, 9.1.1, 9.1.2, 9.1.3, 9.1.4, 9.1.5, 9.1.6, 9.1.7, 9.1.8, 9.1.9, 9.2.0, 9.2.1, 9.2.2, 9.2.3, 9.2.4, 9.2.5, 9.2.6, 9.3.0, 9.3.1, 9.3.2, 9.3.3, 9.3.4, 9.4.0, 9.4.1, 9.4.2
 Download manual
Download manual
Feedback submitted, thanks!