************************************************************************
Splunk Enterprise versions higher than version 9.4.2 are documented only on our new documentation portal.
************************************************************************
To get started, see the Splunk Enterprise page on help.splunk.com and the Splunk Enterprise 9.4.3 release notes.
************************************************************************
For information about how version selection works in the new portal, see Version selection on the About This Site page.
************************************************************************
Tag the host field
Tagging the host field is useful for knowledge capture and sharing, and for crafting more precise searches. You can tag the host field with one or more words. Use this to group hosts by function or type, to enable users to easily search for all activity on a group of similar servers. If you've changed the value of the host field for a given input, you can also tag events that are already in the index with the new host name to make it easier to search across your data set.
Add a tag to the host field in search results
You can add a tag to a host field-value combination in your search results.
Prerequisites
Steps
- Perform a search for data from the host you'd like to tag.
- In the search results, click on the arrow associated with the event containing the field you want to tag. In the expanded list, click on the arrow under Actions associated the field, then select Edit Tags.
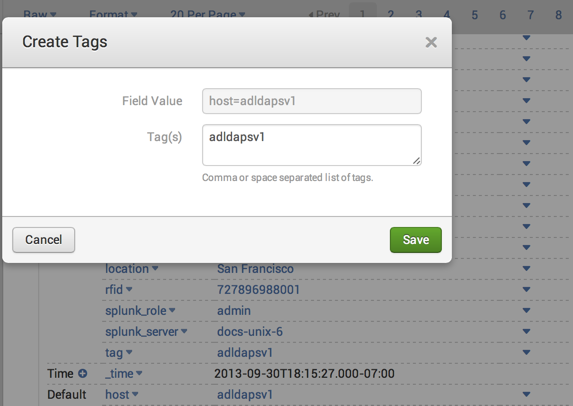
- In the Create Tags dialog enter the host field value that you'd like to tag, for example in Field Value enter Tag host= <current host value>. Enter your tag or tags, separated by commas or spaces, and click Save.
Host names vs. tagging the host field
The value of the host field is set when an event is indexed. It can be set by default based on the Splunk server hostname, set for a given input, or extracted from each event's data. Tagging the host field with an alternate hostname doesn't change the actual value of the host field, but it lets you search for the tag you specified instead of having to use the host field value. Each event can have only one host name, but multiple host tags.
For example, if your Splunk server is receiving compliance data from a specific host, tagging that host with compliance will help your compliance searches. With host tags, you can create a loose grouping of data without masking or changing the underlying host name.
You might also want to tag the host field with another host name if you indexed some data from a particular input source and then decided to change the value of the host field for that input--all the new data coming in from that input will have the new host field value, but the data that already exists in your index will have the old value. Tagging the host field for the existing data lets you search for the new host value without excluding all the existing data.
| Define and manage tags in Settings | Tag event types |
This documentation applies to the following versions of Splunk® Enterprise: 7.0.0, 7.0.1, 7.0.2, 7.0.3, 7.0.4, 7.0.5, 7.0.6, 7.0.7, 7.0.8, 7.0.9, 7.0.10, 7.0.11, 7.0.13, 7.1.0, 7.1.1, 7.1.2, 7.1.3, 7.1.4, 7.1.5, 7.1.6, 7.1.7, 7.1.8, 7.1.9, 7.1.10, 7.2.0, 7.2.1, 7.2.2, 7.2.3, 7.2.4, 7.2.5, 7.2.6, 7.2.7, 7.2.8, 7.2.9, 7.2.10, 7.3.0, 7.3.1, 7.3.2, 7.3.3, 7.3.4, 7.3.5, 7.3.6, 7.3.7, 7.3.8, 7.3.9, 8.0.0, 8.0.1, 8.0.2, 8.0.3, 8.0.4, 8.0.5, 8.0.6, 8.0.7, 8.0.8, 8.0.9, 8.0.10, 8.1.0, 8.1.1, 8.1.2, 8.1.3, 8.1.4, 8.1.5, 8.1.6, 8.1.7, 8.1.8, 8.1.9, 8.1.10, 8.1.11, 8.1.12, 8.1.13, 8.1.14, 8.2.0, 8.2.1, 8.2.2, 8.2.3, 8.2.4, 8.2.5, 8.2.6, 8.2.7, 8.2.8, 8.2.9, 8.2.10, 8.2.11, 8.2.12, 9.0.0, 9.0.1, 9.0.2, 9.0.3, 9.0.4, 9.0.5, 9.0.6, 9.0.7, 9.0.8, 9.0.9, 9.0.10, 9.1.0, 9.1.1, 9.1.2, 9.1.3, 9.1.4, 9.1.5, 9.1.6, 9.1.7, 9.1.8, 9.1.9, 9.2.0, 9.2.1, 9.2.2, 9.2.3, 9.2.4, 9.2.5, 9.2.6, 9.3.0, 9.3.1, 9.3.2, 9.3.3, 9.3.4, 9.4.0, 9.4.1, 9.4.2
 Download manual
Download manual
Feedback submitted, thanks!