About single sign-on using reverse proxy
Proxy single sign-on, or proxy SSO, is an authentication method that lets you configure single sign-on authentication for Splunk Enterprise instances through a reverse proxy server.
With proxy SSO, a proxy server exists between the Splunk Enterprise deployment and an external authentication service. You can pass user identity and group information in HTTP headers from the proxy server to Splunk Enterprise. Splunk Enterprise uses the information it receives in these headers to authenticate users and subsequently authorize them through groups that have been mapped to Splunk roles.
Authentication using proxy SSO provides the following benefits:
- It combines authentication and authorization into one step for the user, which streamlines the login process
- It eliminates a direct connection between Splunk Enterprise and the external authentication service, which increases security
- It reduces the number of configuration steps for authentication
- It lowers the amount of network communication between Splunk Enterprise and authentication services, making authentication more efficient
- It expands the number of authentication service options you can use beyond Lightweight Directory Access Protocol (LDAP), as the proxy server passes the required authentication and authorization information
It's not possible to configure proxy SSO in Splunk Enterprise using Splunk Web. Instead, you must use the Representational State Transfer (REST API) or modify configuration files.
Splunk Cloud Platform does not support authentication using proxy SSO.
For more information about how to configure these items and set up SSO, see Configure single sign-on with reverse proxy.
Prerequisites to configuring proxy SSO
To set up proxy SSO, you must have the following:
- A proxy server
- This proxy server must be configured to send HTTP headers as part of an HTTP web request or response.
- A working Splunk Enterprise deployment
How SSO through a reverse proxy works
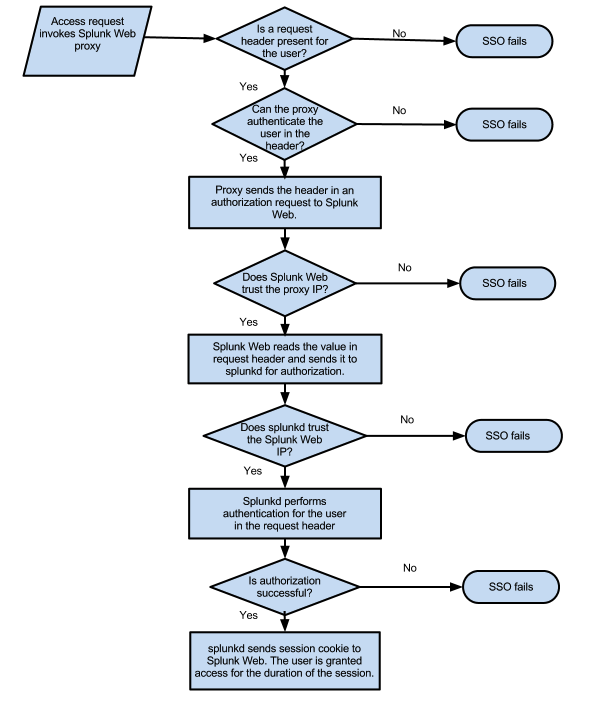
In a single sign-on configuration, Splunk Enterprise users can access Splunk Web through a proxy URL that is deployed with Splunk Web. The proxy authenticates the incoming request against the Splunk authentication system. Upon a successful authentication, the proxy sets a request header with the authenticated identity's attribute and sends this information to Splunk Enterprise.
Splunk Enterprise accepts the incoming HTTP request from the proxy server. If Splunk Enterprise recognizes the user that appears in the HTTP request header, Splunk Enterprise automatically authorizes the user and bypasses the login page for that user.
For single sign-on to succeed, all requests from the proxy to Splunk Web must include this authenticated request header. If the header is not included in a request, then Splunk Enterprise sends the user to the login page or an error page, depending on your configuration. Splunk Enterprise uses this authenticated header for the duration of the browser session.
How Splunk Enterprise processes single sign-on proxy requests
Splunk Web works with the proxy server and the Splunk daemon to process single sign-on through the proxy.
- When the proxy server makes a request to Splunk Web, Splunk Web uses the value for the
trustedIPsetting in the web.conf configuration file to verify that the network internet protocol (IP) address of the proxy server is on the trusted IP list. For Splunk Web, the trusted IP list is a list of one or more network IP addresses that Splunk Web explicitly trusts as coming from a proxy server.- If the IP address of the proxy server is not in this list, Splunk Web rejects the request and the sign-on attempt fails.
- If the proxy server IP address is in the list, then Splunk Web extracts the identity from the HTTP request header that it receives from the proxy server and sends an authorization request to the splunk daemon process that contains that header information.
- The Splunk daemon receives the authorization request from Splunk Web and verifies whether or not it trusts the incoming IP address from Splunk Web as defined by the value for the
trustedIPsetting in the server.conf configuration file.- If the Splunk daemon does not trust the Splunk Web IP address, then the Splunk daemon rejects the request, the sign-on attempt fails, and Splunk Web either returns the user to the login page or loads an error page.
- If the Splunk daemon trusts the Splunk Web IP address, then the Splunk daemon uses the information contained in the request header and proceeds with the authorization process.
For more information on how to configure how Splunk Web handles error conditions with single sign-on, see Configure single sign-on with reverse proxy.
How Splunk Enterprise authorizes a user during single sign-on
After the Splunk daemon verifies that the request for authentication is valid, as described previously, it begins authorizing the user that is based on the identity that appears in the header request that it received from the proxy server.
- The Splunk daemon first checks to see if the dentity and role matches any of the native Splunk users that are present on the instance.
- If there is no match, then the Splunk daemon checks to see if you have configured the lightweight directory access protocol (LDAP) authenticaton scheme.
- If you have configured LDAP as an authentication scheme, it checks for matches against the LDAP server. looks to see if there are any LDAP matches.
- If the Splunk daemon does not find a match in LDAP, and the identity cannot be authorized, then the Splunk daemon sends an authentication failure message, and the web browser goes to an error page.
- If there is a match, then the Splunk daemon authorizes the user and confirms if a session for the user already exists.
- If a session exists, the Splunk daemon uses the session identifier that is associated with the session and Splunk Web creates the necessary web cookies to let the user access the instance.
- If a session does not exist, then the Splunk daemon creates a new session and Splunk Web provides cookies for that session.
After Splunk Web creates the web cookies, subsequent access to Splunk Enterprise through the proxy URL does not require re-authorization as long as the request header contains the trusted identity. This session lasts until the user closes the browser window.
Configure single sign-on using reverse proxy
To set up proxy SSO for Splunk Enterprise, follow the instructions at Configure single sign-on with reverse proxy.
| Troubleshoot token authentication | Configure Single Sign-On with reverse proxy |
This documentation applies to the following versions of Splunk® Enterprise: 7.0.0, 7.0.1, 7.0.2, 7.0.3, 7.0.4, 7.0.5, 7.0.6, 7.0.7, 7.0.8, 7.0.9, 7.0.10, 7.0.11, 7.0.13, 7.1.0, 7.1.1, 7.1.2, 7.1.3, 7.1.4, 7.1.5, 7.1.6, 7.1.7, 7.1.8, 7.1.9, 7.1.10, 7.2.0, 7.2.1, 7.2.2, 7.2.3, 7.2.4, 7.2.5, 7.2.6, 7.2.7, 7.2.8, 7.2.9, 7.2.10, 7.3.0, 7.3.1, 7.3.2, 7.3.3, 7.3.4, 7.3.5, 7.3.6, 7.3.7, 7.3.8, 7.3.9, 8.0.0, 8.0.1, 8.0.2, 8.0.3, 8.0.4, 8.0.5, 8.0.6, 8.0.7, 8.0.8, 8.0.9, 8.0.10, 8.1.0, 8.1.1, 8.1.2, 8.1.3, 8.1.4, 8.1.5, 8.1.6, 8.1.7, 8.1.8, 8.1.9, 8.1.10, 8.1.11, 8.1.12, 8.1.13, 8.1.14, 8.2.0, 8.2.1, 8.2.2, 8.2.3, 8.2.4, 8.2.5, 8.2.6, 8.2.7, 8.2.8, 8.2.9, 8.2.10, 8.2.11, 8.2.12, 9.0.0, 9.0.1, 9.0.2, 9.0.3, 9.0.4, 9.0.5, 9.0.6, 9.0.7, 9.0.8, 9.0.9, 9.0.10, 9.1.0, 9.1.1, 9.1.2, 9.1.3, 9.1.4, 9.1.5, 9.1.6, 9.1.7, 9.1.8, 9.1.9, 9.2.0, 9.2.1, 9.2.2, 9.2.3, 9.2.4, 9.2.5, 9.2.6, 9.3.0, 9.3.1, 9.3.2, 9.3.3, 9.3.4, 9.4.0, 9.4.1, 9.4.2
 Download manual
Download manual
Feedback submitted, thanks!