Exploring the Search views
In Part 2, you learned about the types of data that the Splunk platform works with and uploaded the tutorial data into the index. In Part 3, you will learn about the Search app.
Find Splunk Search
- If you are not on the Splunk Home page, click the Splunk logo on the Splunk bar to go to Splunk Home.
- From Splunk Home, click Search & Reporting in the Apps panel.
This opens the Search Summary view in the Search app.
Search Summary view
The Search Summary view includes common elements that you see on other views, including the Applications menu, the Splunk bar, the Apps bar, the Search bar, and the Time Range Picker. Elements that are unique to the Search Summary view are the panels below the Search bar: the How to Search panel and the Search History panel.
The Search Summary view in Splunk Cloud Platform and Splunk Enterprise are almost identical.
The following image shows the Search Summary view in Splunk Cloud Platform.
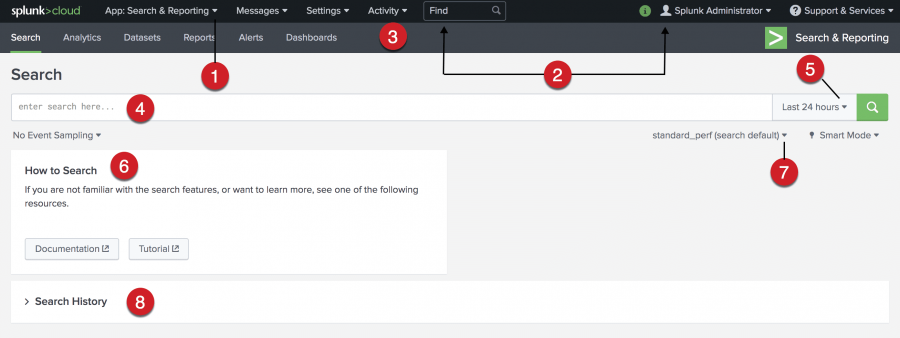
| Number | Element | Description |
|---|---|---|
| 1 | Applications menu | Switch between Splunk applications that you have installed. The current application, Search & Reporting app, is listed. This menu is on the Splunk bar. |
| 2 | Splunk bar | Edit your Splunk configuration, view system-level messages, and get help on using the product. |
| 3 | Apps bar | Navigate between the different views in the application you are in. For the Search & Reporting app the views are: Search, Analytics, Datasets, Reports, Alerts, and Dashboards. |
| 4 | Search bar | Specify your search criteria. |
| 5 | Time range picker | Specify the time period for the search, such as the last 30 minutes or yesterday. The default is Last 24 hours. |
| 6 | How to search | Contains links to the Search Manual and the Search Tutorial. |
| 7 | Workload management (Splunk Cloud Platform only) | Specify which pool to run your search in or to use a policy-based pool. The policies are defined in the Workload Management app. |
| 8 | Search history | View a list of the searches that you have run. The search history appears after you run your first search. |
In Splunk Enterprise there is an additional option in How to search, called Data Summary, which shows a summary of the data that is uploaded to the Splunk instance and that you are authorized to view. There is also an option entitled Analyze Your Data with Table Views where you can prepare data without using the Search Processing Language (SPL).
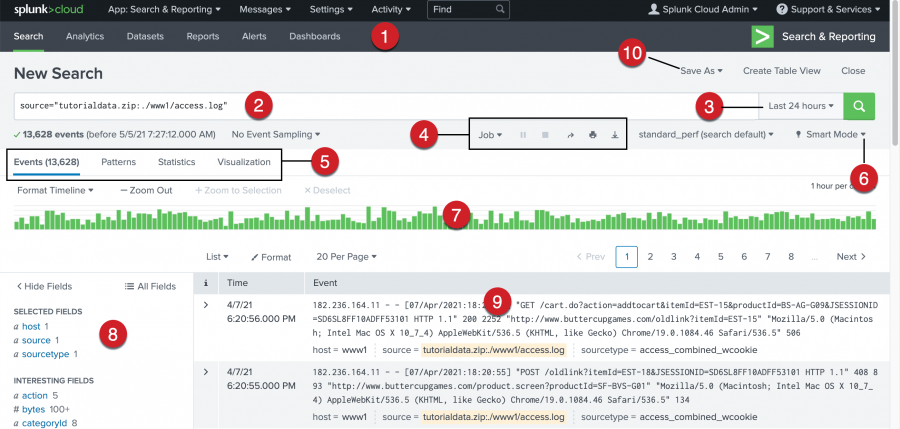
New Search view
The New Search view opens after you run a search.
Some of the elements in this view might be familiar, such as the Apps bar, the Search bar, and the time range picker. Below the Search bar, are the Timeline, the Fields sidebar, and the Events view.
The New Search view in Splunk Cloud Platform and Splunk Enterprise are almost identical.
The following image shows the New Search view in Splunk Cloud Platform.
| Number | Element | Description |
|---|---|---|
| 1 | Apps bar | Navigate between the different views in the Search & Reporting app: Search, Analytics, Datasets, Reports, Alerts, and Dashboards. |
| 2 | Search bar | Specify your search criteria. |
| 3 | Time range picker | Specify the time period for the search. |
| 4 | Search action buttons | Actions that you can perform, including working with your search Job, sharing, printing, and exporting your search results. |
| 5 | Search results tabs | The tab that your search results appear on depends on your search. Some searches produce a set of events, which appear on the Events tab. Other searches transform the data in events to produce search results, which appear on the Statistics tab. |
| 6 | Search mode menu | Use the search mode selector to provide a search experience that fits your needs. The modes are Smart (default), Fast, and Verbose. |
| 7 | Timeline | A visual representation of the number of events that occur at each point in time. Peaks or valleys in the timeline can indicate spikes in activity or server downtime. The timeline options are located above the timeline. You can format the timescale, zoom out, or zoom to a selected set of events. |
| 8 | Fields sidebar | Displays a list of the fields discovered in the events. The fields are grouped into Selected Fields and Interesting Fields. |
| 9 | Events viewer | Displays the events that match your search. By default, the most recent event is listed first. In each event, the matching search terms are highlighted. To change the event view, use the List, Format, and Per Page options. |
| 10 | Save As menu | Use the Save As menu to save your search results as a Report, Dashboard Panel, Alert, or Event Type. |
Next step
Learn about specifying time ranges in your searches.
See also
View and interact with your Search History in the Search Manual
Why source types matter in Getting Data In
| Upload the tutorial data | Specifying time ranges |
This documentation applies to the following versions of Splunk Cloud Platform™: 9.3.2411 (latest FedRAMP release), 8.2.2112, 8.2.2201, 8.2.2202, 8.2.2203, 9.0.2208, 9.0.2205, 9.0.2209, 9.0.2303, 9.0.2305, 9.1.2308, 9.1.2312, 9.2.2403, 9.2.2406, 9.3.2408
 Download manual
Download manual
Feedback submitted, thanks!