About private connectivity
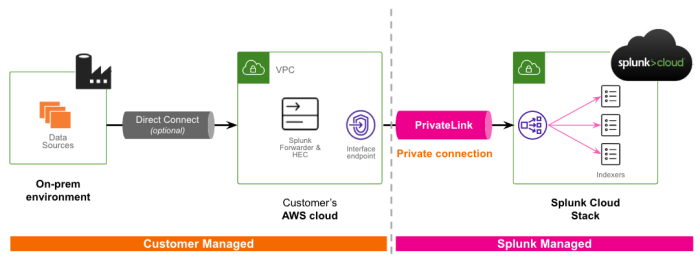
Splunk Cloud private connectivity allows you to directly connect your Splunk Cloud Platform environment with your Amazon Virtual Private Cloud (VPC). This allows you to route the data you ingest into the Splunk Cloud Platform through the Amazon Web Service (AWS) internal network using AWS PrivateLink. Although AWS-to-AWS traffic should not leave the global AWS network (with a minor documented exception), the PrivateLink feature ensures your AWS traffic sent to the Splunk Cloud Platform only traverses private IPs (in other words, non-public internet routable addresses).
Splunk Cloud encrypts all data in flight by employing Transport Layer Security (TLS) 1.2+ for ingest data and Hypertext Transfer Protocol Secure (HTTPS) for search data. You can also restrict traffic further by establishing firewall rules or by creating an IP allow list. While these protections are sufficient for most Splunk Cloud customers, Splunk Cloud private connectivity supports the additional needs of customers who operate in one of the following regulated environments:
- Health Insurance Portability and Accountability Act (HIPAA)
- Payment Card Industry Data Security Standard (PCI DSS)
- Infosec Registered Assessors Program (IRAP)
- Federal Risk and Authorization Management Program Impact Level 2 (FedRAMP IL2)
To configure private connectivity, Splunk Cloud administrators can use Admin Config Service (ACS) APIs to confirm their eligibility and enable this feature. Splunk Cloud will then provision service endpoints and ensure your data is accepted in your Splunk Cloud deployment.
Requirements
To leverage private connectivity for your Splunk Cloud deployment:
- You must be using AWS infrastructure.
- You must be in a PCI, HIPAA, IRAP, or FedRAMP IL2 environment.
- You must be on the Victoria Experience for AWS standard environments or the Classic Experience for GovCloud and FedRAMP IL2 environments.
New Splunk Cloud deployments that are built with HIPAA and PCI are eligible for private connectivity. Only Existing customers with Splunk Cloud deployments that were built with both HIPAA and PCI at the same time, or customers who upgraded their existing deployment to a higher compliance certification (for example: PCI), are not eligible for private connectivity.
Scope and considerations
Consider the following before enabling the private connectivity feature:
- Only ingest data that you send to the Splunk Cloud Platform from a universal forwarder, heavy forwarder, or Http Event Collector (HEC) will flow over AWS PrivateLink.
- All other Splunk Cloud Platform data will flow over the public internet. This includes search, UI, and app data or services that require HEC acknowledgements.
- Data that you send to the Splunk Cloud Platform must originate from the same region as your Splunk Cloud environment.
- To connect multiple AWS accounts through private connectivity, you need to create a VPC and PrivateLink endpoint for each account.
- You are responsible for AWS costs associated with your VPC. For more information, see: AWS PrivateLink pricing.
| Area | Customer Responsibilities | Splunk Responsibilities |
|---|---|---|
| Pre-enablement verification | Review and acknowledge the feature scope, consider security and implementation impact, align internal stakeholders, and prepare your environment for enablement. | N/A |
| Enablement | Follow Enable private connectivity to configure your Splunk Cloud environment. | Provision service endpoints. |
| Network connectivity | Update universal forwarder credentials. For each connecting VPC, establish private endpoints and the appropriate DNS mappings for routing data using the AWS PrivateLink endpoint service. | Accept data from private endpoints into the Splunk Cloud Platform. |
| Management | Configure resources like security group rules and DNS zones within your VPC and ensure service availability. | Maintain performance and availability standards defined in the Splunk Cloud Service Level Agreement (SLA). |
If private connectivity meets your requirements, and you would like to enable this feature for your Splunk Cloud deployment, follow the instructions in Enable private connectivity.
| Turning off Splunk platform role-based field filtering | Enable private connectivity |
This documentation applies to the following versions of Splunk Cloud Platform™: 9.0.2205, 9.0.2208
 Download manual
Download manual
Feedback submitted, thanks!