Deployment architectures
Splunk App for Stream supports the following deployment architectures:
- Single instance deployment
- Distributed deployment
Single instance deployment
You can install Splunk App for Stream on a single Splunk Enterprise instance. A single instance serves as both search head and indexer, providing both search and storage capability. A single instance deployment can support one or two users running concurrent searches.
For single instance installation instructions, see Install Splunk App for Stream in this manual.
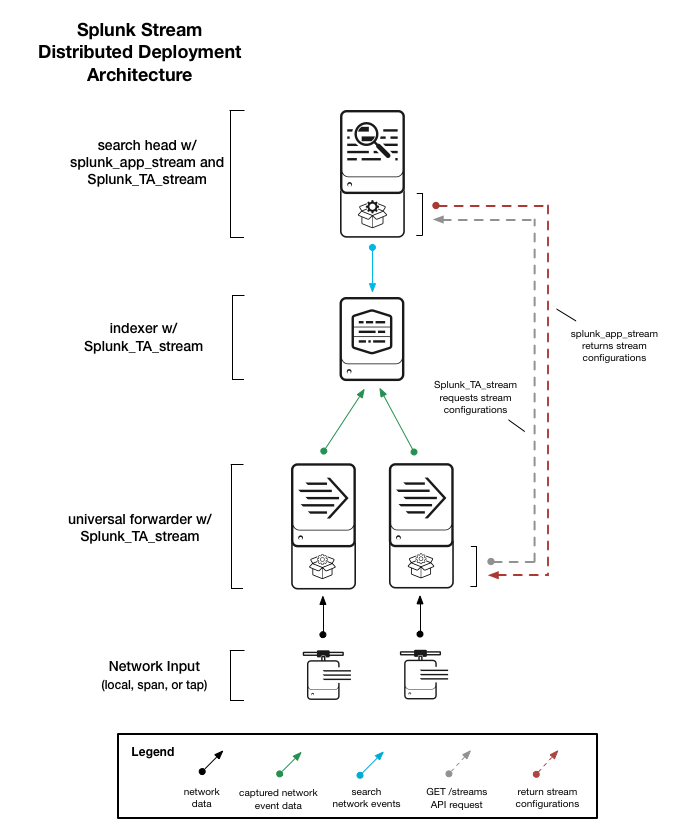
Distributed deployment
A Splunk App for Stream distributed deployment can capture network event data from multiple network devices, including NICs, switches, routers, and so on. A distributed deployment can apply to many types of medium and large enterprise network infrastructures.
The diagram illustrates a Splunk App for Stream distributed deployment.
A Splunk App for Stream distributed deployment includes these Splunk components:
Search Heads
Install Splunk App for Stream (splunk_app_stream) on one or more search heads.
Note: Splunk App for Stream currently does not support search head clustering.
Indexers
Install Splunk_TA_stream on all indexers.
Universal forwarders
Install Splunk_TA_stream on any number of universal forwarders at the location(s) where you want to capture network data. See Network collection architectures in this manual.
Deployment server and distributed management console (DMC)
In a small, single search head deployment, both the deployment server and distributed management console (DMC) can run on the same Splunk Enterprise instance on which you install splunk_app_stream.
In deployments with large numbers of forwarders (over 100), we recommend that you run splunk_app_stream on the DMC host, and run the deployment server on a separate host.
For more information on deployment server architecture and scalability, see Deployment server provisioning in Upgrading Splunk Enterprise Instances.
For more information on Splunk Enterprise components, see Components of a Splunk Enterprise deployment in the Splunk Enterprise Capacity Planning Manual.
How it works
Splunk_TA_stream, which includes the streamfwd binary, captures network event data from NICs on local machines (such as each node of a subnet environment) or from a network SPAN or TAP. See Network collection architectures in this manual.
Splunk_TA_stream then sends the captured network event data from universal forwarders to indexers using the "Wire Data" modular input.
Use the Configure Streams UI inside splunk_app_stream to configure the network data protocols (such as http, tcp, dns, and so on) that you want the streamfwd binary to capture.
Use the streamfwd.xml file in Splunk_TA_stream/local to configure system-level parameters (specify IP address/ports, add network interfaces, enable SSL, and so on) for the streamfwd binary. See Configure Stream forwarder in this manual.
While you can use multiple search heads to search and analyze captured network event data on your indexers, you do not need to install splunk_app_stream on more than one search head.
How Splunk_TA_stream communicates with splunk_app_stream
Splunk_TA_stream, which contains the streamfwd binary, pings splunk_app_stream at regular intervals over HTTP port 8000. If streamfwd detects a change in stream configurations in the Configure Streams UI, it sends an API request to the endpoint to return the latest configuration data. For more information, see Splunk App for Stream REST API in this manual.
The streamfwd binary pings splunk_app_stream at the location (URI) that you specify when you create a Wire Data modular input in Splunk Enterprise. The location of splunk_app_stream is stored in $SPLUNK_HOME/etc/apps/Splunk_TA_stream/local/inputs.conf. See Specify the location of splunk_app_stream.
Note: streamfwd pings splunk_app_stream at default intervals of 5 seconds. To change the ping interval, use the <PingInterval> element in streamfwd.xml. See Configure Stream forwarder.
| Deployment requirements | Network collection architectures |
This documentation applies to the following versions of Splunk Stream™: 6.4.0, 6.4.1, 6.4.2
 Download manual
Download manual
Feedback submitted, thanks!