Integrate Splunk Enterprise Security and Splunk UBA with this add-on
Use the Splunk add-on for Splunk UBA to integrate Splunk Enterprise Security and Splunk User Behavior Analytics (UBA). You can integrate Splunk UBA and Splunk Enterprise Security to share the following types of data:
- Send threats and anomalies from Splunk UBA to Splunk Enterprise Security to adjust risk scores and create notable events.
- Send correlation search results from Splunk Enterprise Security to Splunk UBA to be processed for anomalies.
- Retrieve user and device association data from Splunk UBA to view it in Splunk Enterprise Security. Identify user accounts and devices associated with devices during specific sessions, and devices associated with users during specific sessions.
- Send audit events to the Splunk platform to be added to the
_auditindex.
Although you can use this add-on to integrate the Splunk platform with Splunk UBA without using Splunk Enterprise Security, the add-on is only available with Splunk Enterprise Security. Splunk Enterprise Security includes additional functionality in SA-UEBA that is configured to use the data in the UEBA data model and sent from Splunk UBA.
After you complete the integration, users can view information in Splunk Enterprise Security and the Splunk platform. See Viewing data from Splunk UBA in Enterprise Security in Use Splunk Enterprise Security.
Prerequisites
Before integrating Splunk UBA and Splunk Enterprise or Splunk Enterprise Security, meet these prerequisites.
Prerequisites for integrating with Splunk Enterprise
Before integrating Splunk UBA and the Splunk platform, meet these prerequisites.
- A user account with capabilities to perform real-time search, perform REST API calls, and access to the data. The
adminrole in the Splunk platform has the required capabilities by default. If you use a different role, you need thert_search,edit_forwarders,list_forwarders, andedit_uba_settingscapabilities. Add these capabilities to a role in Splunk Web. See Add and edit roles with Splunk Web in Securing Splunk Enterprise. - The user account must also have no concurrent search quota and sufficient disk usage quota (for example, 40GB).
- Compatible software versions installed in your environment.
- The Splunk add-on for Splunk UBA installed and enabled on your search head with the
uebaindex deployed to your indexers. See Deploy the Splunk add-on for Splunk UBA.
Splunk Cloud customers must contact Splunk Support to fully integrate with Splunk UBA. The Splunk Cloud admin role cannot perform UBA setup.
Prerequisites for integrating with Splunk Enterprise Security
Starting with release 6.1.0, Splunk ES can use a local user account to integrate with Splunk UBA. To perform the integration, meet the following requirements:
- In Splunk UBA, configure an account with the name of
ubaesuserand the role ofUser. See Add a local user account in the Administer Splunk User Behavior Analytics manual in the Splunk UBA documentation. - In Splunk ES, create the matching credentials. See Add a new credential for UBA input in the Splunk Enterprise Security Administer Splunk Enterprise Security manual.
Splunk authentication is used when integrating with Splunk Enterprise Security prior release 6.1.0. Before integrating Splunk UBA and Splunk ES, meet this prerequisite.
- Splunk Authentication must be configured in Splunk UBA. See "Select Splunk Authentication" in Configure Splunk authentication using Splunk UBA in the Splunk User Behavior Analytics Administer Splunk User Behavior Analytics manual.
Steps to integrate Splunk Enterprise Security and Splunk UBA
To take advantage of all of the functionality available from integrating Splunk Enterprise Security and Splunk UBA, perform all of the steps in the table.
To use only specific functionality from Enterprise Security or Splunk UBA, perform only the steps marked in the table for the specific set of functionality. For example, to send threats and anomalies to ES, perform the tasks marked with an "X" in the "Send threats and anomalies to ES" column in the order they are listed.
- Enable SA-UEBA.
- Set up a Splunk ES search head to receive TCP data.
- Connect Splunk UBA to the Splunk platform using SSL.
- Add an output connector in Splunk UBA.
| Step | Send threats and anomalies to ES | Send correlation search results to UBA | Send user and device data to ES | Send audit events to ES |
|---|---|---|---|---|
| Enable SA-UEBA. | X | |||
| UBA Add or set the uba.sys.audit.push.splunk.enabled property in Splunk UBA | X | |||
| Set up a search head or forwarder to receive TCP data. | X | X | X | |
| Perform UBA setup to send correlation search results to Splunk UBA. | X | |||
| Perform UBA setup to send user and device association data to Splunk ES. | X | |||
| Connect Splunk UBA to the Splunk platform using SSL. | X | X | X | X |
| Add an output connector in Splunk UBA. | X | |||
| Set up correlation search results as a data source in Splunk UBA. | X | |||
| Set up Splunk UBA to send user and device association data to Enterprise Security. | X |
If Enterprise Security is installed on a search head cluster, choose one search head to integrate with Splunk UBA. Splunk UBA does not support integrating with multiple search heads.
Enable SA-UEBA
Enable SA-UEBA so that dashboards and knowledge objects are visible to users in Splunk Enterprise Security. This step is required to retrieve data from Splunk UBA to display on the Session Center dashboard in Splunk Enterprise Security, and to model data sent from Splunk UBA with the UEBA data model and use correlation searches to analyze threats and anomalies sent from Splunk UBA.
- Log in to the Splunk search head with Splunk Enterprise Security installed.
- In Splunk Web, select Apps > Manage Apps.
- Locate the SA-UEBA add-on.
- Click Enable to enable the add-on.
Add or set the uba.sys.audit.push.splunk.enabled property in Splunk UBA
Perform the following tasks in Splunk UBA to begin enabling audit logs to be sent to the Splunk platform:
- Set the
uba.sys.audit.push.splunk.enabledproperty in the/etc/caspida/local/conf/uba-site.propertiesfile totrue:uba.sys.audit.push.splunk.enabled=true
- In distribIuted deployments, synchronize the cluster. Run the following command:
/opt/caspida/bin/Caspida sync-cluster /etc/caspida/local/conf
Set up a search head or forwarder to receive data from Splunk UBA
You can choose to set up either a search head or a forwarder to receive data sent from Splunk UBA.
- In Splunk UBA release 4.3.0 and earlier, you can send data only to a Splunk search head.
- In Splunk UBA release 4.3.1 and later, you can send data to a Splunk search head or forwarder.
Perform the following tasks to set up a search head to receive data from Splunk UBA:
- In Splunk Web, select Settings > Data Inputs.
- Select TCP.
- Click the button to enable TCP port 10008, which is configured to work with Splunk UBA.
Perform the following tasks to set up a forwarder to receive data from Splunk UBA:
- Deploy the Splunk add-on for Splunk UBA to the forwarder. See Deploy the Splunk add-on for Splunk UBA.
- Configure the TCP input on the Splunk forwarder. See Get data from TCP and UDP ports in Getting Data In for information on how to configure a Splunk forwarder to receive a syslog input
Perform UBA setup to send correlation search results to Splunk UBA
Splunk Cloud customers must contact Splunk Support to perform Splunk UBA setup.
Perform the following tasks to setup Splunk UBA to receive correlation search results from Splunk ES:
- From the Enterprise Security menu bar, select Configure > UBA Setup. You can also click Apps > Manage Apps and select Set up next to this add-on.
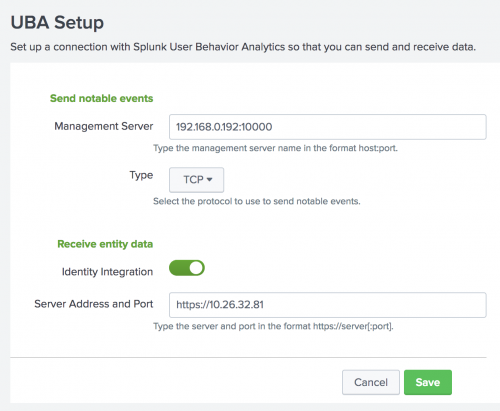
- In the Management Server field, type the host name and port of Splunk Enterprise Security output connector on the Splunk UBA management server, port 10008. For example,
<server IP address>:10008. - In the Type field, select whether to use the TCP or UDP protocol to send the correlation search results to Splunk UBA.
Perform UBA setup to send user and device association data to Splunk ES
Send user and device association data, or entity data, to Splunk ES.
Splunk Cloud customers must contact Splunk Support to perform UBA setup.
- From the Enterprise Security menu bar, select Configure > UBA Setup. You can also click Apps > Manage Apps and select Set up next to this add-on.
- Click the button to enable identity integration.
- In the Server Address and Port field, type
https://followed by the IP address of the Splunk UBA management server. If using HTTPS, the port number is optional because you specifyhttps://with the IP address.
For example,https://<server IP address>. - Click Save.
- In Splunk UBA, enable authentication from the Splunk platform. See Configure authentication for Splunk platform users.
You must restart the Splunk platform after setting up the integration to send correlation search results to Splunk UBA. If you are on a search head cluster, use the deployer to deploy the change from the Splunk_TA-ueba outputs.conf file to the cluster members.
See System requirements for Splunk UBA for more details on the ports used by Splunk UBA.
Connect Splunk UBA to the Splunk platform using SSL
See Connect Splunk UBA to Splunk platform to view supporting events.
Starting in Splunk UBA version 3.2.0, the connection between Splunk UBA and the Splunk platform uses TCP-SSL by default. Set up the Splunk platform to accept the encrypted connection. This step is required to send data from Splunk UBA to the Splunk platform using an output connector.
Splunk Cloud customers must work with Splunk Support to set up this connection.
- In the Splunk add-on for Splunk UBA, open
/opt/splunk/etc/apps/Splunk_TA_ueba/local/inputs.conffor editing. - Add two stanzas to match the following.
[tcp-ssl:10008] listenOnIPv6 = no index = ueba sourcetype = ueba [SSL] rootCA = $SPLUNK_HOME/etc/auth/cacert.pem serverCert = $SPLUNK_HOME/etc/auth/server.pem password = password
- In a distributed environment, deploy the changes to the
inputs.conffile to indexers and forwarders as needed. - Restart splunkd.
- In Splunk Web, select System > Server controls.
- Click Restart Splunk.
- Verify that SSL is enabled for port 10008 in
splunkd.log11-07-2016 15:07:42.661 -0800 INFO TcpInputProc - Creating raw Acceptor for IPv4 port 10002 with Non-SSL 11-07-2016 15:07:42.661 -0800 INFO TcpInputProc - Creating fwd data Acceptor for IPv4 port 10003 with Non-SSL 11-07-2016 15:07:42.661 -0800 INFO TcpInputProc - Creating raw Acceptor for IPv4 port 10008 with SSL
- Copy the root CA certificate from the Splunk platform to Splunk UBA.
/opt/splunk/etc/auth/cacert.pem - Log in to the Splunk UBA management server as the caspida user.
- Import the rootCA certificate to the Java certificate store. For example:
sudo keytool -import -alias "splunk es" -keystore /usr/lib/jvm/java-1.8.0-openjdk-amd64/jre/lib/security/cacerts -file ~/cacert.pem
If your JDK is not installed in
/usr/lib/jvm/java-1.8.0-openjdk-amd64, perform the following steps import the rootCA certificate:- Ensure that
$JAVA_HOMEis set correctly on your system. In the following examples, replace<jdk-install-dir>with the directory where the JDK is installed, such as/usr/lib/jvm/java-1.8.0-openjdk-amd64.- To set the
$JAVA_HOMEin Korn and Bash shells:export JAVA_HOME=<jdk-install-dir> export PATH=$JAVA_HOME/bin:$PATH
- To set the
$JAVA_HOMEin Bourne shells:JAVA_HOME=<jdk-install-dir> export JAVA_HOME PATH=$JAVA_HOME/bin:$PATH export PATH
- To set the
$JAVA_HOMEin C shells:setenv JAVA_HOME <jdk-install-dir> setenv PATH $JAVA_HOME/bin:$PATH export PATH=$JAVA_HOME/bin:$PATH
- To set the
- Import the rootCA certificate to the Java certificate store.
sudo keytool -import -alias "splunk es" -keystore $JAVA_HOME/jre/lib/security/cacerts -file ~/cacert.pem
When prompted, type the keystore password and trust the certificate. The default keystore password is
changeit. - Ensure that
- From the command line of the Splunk UBA management server, edit the
/etc/caspida/local/conf/uba-site.propertiesfile to include theconnectors.output.splunkes.sslparameter.connectors.output.splunkes.ssl=true - Restart Splunk UBA. See Reboot Splunk UBA in Administer Splunk UBA.
Add an output connector in Splunk UBA
Set up Splunk UBA to send data to the Splunk search head or a Splunk forwarder. Splunk UBA uses the output connector to send anomalies and threats to Splunk Enterprise Security.
- Make sure the Splunk Add-on for Splunk UBA (Splunk_TA_ueba) is properly deployed and enabled.
- Make sure the SA-UEBA add-on is enabled.
- Log in to Splunk UBA as an admin user.
- Select Manage > Output Connectors.
- Click New Output Connector.
- Select an output connector of SplunkES and click Next.
- Type a Name for the output connector.
- The Forwarder Host is the IP address of the Splunk search head or forwarder with the TCP data input enabled. For a search head cluster, choose a search head to integrate with Splunk UBA as Splunk UBA does not support integrating with multiple search heads.
- The Forwarder Port is the TCP port that is open for receiving data on the Splunk search head or forwarder. Make sure this port is open behind your firewall.
- Specify the Splunk ES API URL in the following format:
https://<forwarder-host>:<mgmt-port>
Splunk UBA uses this connection to synchronize the status of its threats with notable events in Splunk ES. The management port is usually 8089. - Specify a username and password. See Prerequisites for the requirements of this user account you are providing.
- Select how you want this output connector to process anomalies and threats.
Option Description Process Threats Select Process Threats to enable Splunk UBA export threats based on any configured output connectors, such as sending email or sending threats to Splunk ES. If this is not selected, no threats are exported from Splunk UBA, even if Auto Process is selected. Process Anomalies Select Process Anomalies to enable Splunk UBA export anomalies based on any configured output connectors, such as sending email or sending anomalies to Splunk ES. If this is not selected, no anomalies are exported from Splunk UBA, even if Auto Process is selected. Auto Process Select Auto Process to automatically forward threats as they are created to Splunk ES. If this is not selected, you must forward each threat individually during threat review with the Export to Splunk ES action from the Threat Details page. See Threat Details. The Auto Process option does not work with anomalies. - Click OK to save the new output connector.
If the output connector does not work, verify that you configured the host server correctly in the uba-site.properties file. The host identified in the file populates the host field for events sent to Splunk Enterprise Security or the Splunk platform. See Connect Splunk Web to Splunk platform to view supporting events.
Set up correlation search results as a data source in Splunk UBA
Set up a new data source in Splunk UBA to receive correlation search results from Splunk Enterprise Security.
In Splunk UBA:
- Select Config > Data Sources and click New Data Source.
- Select a data source of Netcat.
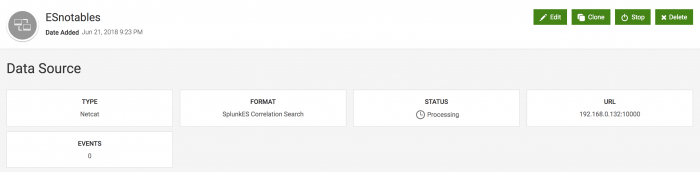
- Specify a name for the data source, such as ESnotables. The data source name must be alphanumeric, with no spaces or special characters.
- Select a format of SplunkES Correlation Search.
- Click Next.
- Deselect the check box for Test Mode.
- Click OK to save the new data source.
Click on the data source after it is created, and make a note of the URL, including the port number. Each time a new data source is created, the port number is incremented by 1. The port number is required to send content from Splunk Enterprise Security to Splunk UBA. If you are adding multiple data sources, or testing and adding the same data source multiple times, keep track of the port number assigned to the data sources you want to use.
In Splunk Enterprise Security:
- Select Configure > UBA Setup.
- Enter the IP address and port number of the data source in the Management Server field. This value should match the IP address and port number shown in the data source you created. Note that you do not need to provide the
https://portion of the URL. - Restart the Splunk platform.
Set up Splunk UBA to send user and device association data to Enterprise Security
Set up Splunk UBA to send user and device association data to Enterprise Security. User and device association data from Splunk UBA is visible on the Session Center dashboard in Splunk Enterprise Security. See Session Center dashboard in Use Splunk Enterprise Security.
- Log in to the Splunk UBA management server as the caspida user using SSH.
- Open the
/etc/caspida/local/conf/uba-site.propertiesfile. - Edit or create the
identity.resolution.export.enabledsetting and set it totrue.
identity.resolution.export.enabled=true
- Restart the Splunk UBA UI service for the changes to take effect.
sudo service caspida-ui stop sudo service caspida-ui start
| Configure inputs for the Splunk add-on for Splunk UBA |
This documentation applies to the following versions of Splunk® Add-on for Splunk UBA: 1.3.0
 Download manual
Download manual
Feedback submitted, thanks!