Enable Kafka data ingestion
Enable Kafka ingestion in Splunk UBA when adding a data source using the Splunk Direct or Splunk Raw Events connector. See Use connectors to add data from the Splunk platform to Splunk UBA for information about when to use the Splunk Direct connector and when to use the Splunk Raw Events connector.
Perform the following steps to enable Kafka data ingestion:
- In Splunk UBA, select Manage > Data Source.
- In the New Data Source window, select Splunk in the SIEM Connectors category and click Next.
- Specify the connection details to Splunk Enterprise. In the Connector Type field, select either Splunk Direct or Splunk Raw Events.
- Select the Kafka Ingestion checkbox.
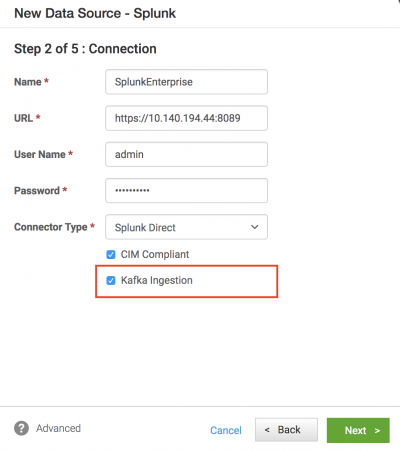
- Click Next.
- Navigate through the remainder of the screens, and then click OK at the end to create the data source.
When configuring a custom Splunk data source for Kafka ingestion, make sure that the custom SPL used in the data source query only uses commands that can run on Splunk indexers. If a custom data source query includes a command that cannot be run on Splunk indexers, Kafka ingestion will not be properly distributed out and will only run on the search head. To learn which commands can run, see Processing attributes in the Search Manual.
| Install the Splunk UBA Kafka Ingestion App | Configure Kafka data ingestion |
This documentation applies to the following versions of Splunk® User Behavior Analytics Kafka Ingestion App: 1.4, 1.4.1, 1.4.2, 1.4.3, 1.4.4, 1.4.5, 1.4.6
 Download manual
Download manual
Feedback submitted, thanks!