Send data from the Splunk platform directly to Kafka
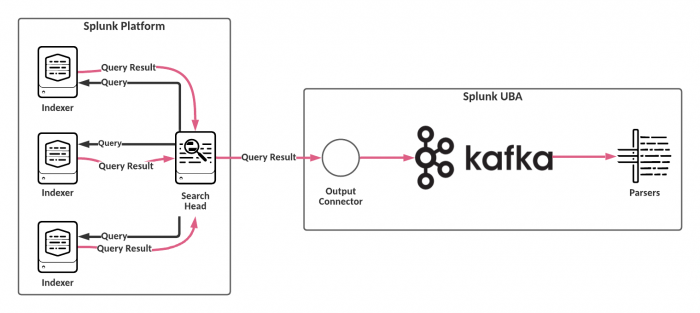
In a typical Splunk UBA configuration, both search results and raw events are sent from the indexers to the search heads. The Splunk search heads are solely responsible for processing the events and keeping track of the number of events processed. This configuration is shown in the following diagram.
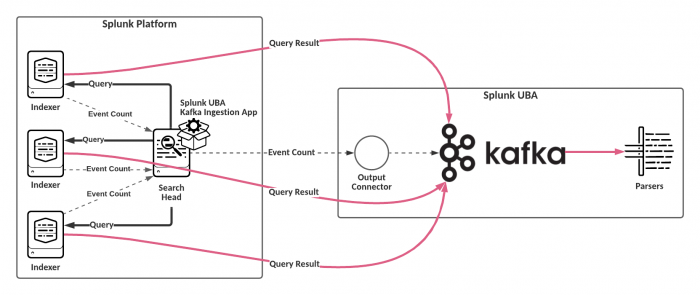
When working with large data sets, you can send events from the Splunk platform directly to Kafka for ingestion. Sending data directly to Kafka offloads the processing task from the search heads to the indexers. The search heads still track the total number of events processed.
To push data from the indexers directly to Kafka in Splunk UBA, perform the following tasks:
- Begin by installing the Splunk UBA Kafka Ingestion App on the search head. When a search is issued to a search head, add-ons installed on the search heads are automatically replicated to the indexers. This means all field extractions are also pushed to indexers, and there is no need to install the add-on on the indexers. See Install the Splunk UBA Kafka Ingestion App.
- In Splunk UBA, configure a data source and enable Kafka ingestion. See Enable Kafka data ingestion.
- In Splunk UBA, start the data source.
After Kafka ingestion is enabled, events from your search results are pushed from the indexers directly to Kafka on Splunk UBA.
| What's new in this release? | Requirements for Kafka data ingestion |
This documentation applies to the following versions of Splunk® User Behavior Analytics Kafka Ingestion App: 1.3, 1.4, 1.4.1, 1.4.2, 1.4.3, 1.4.4, 1.4.5, 1.4.6
 Download manual
Download manual
Feedback submitted, thanks!