Identity correlation
Identity correlation uses an identity list to provide information used to correlate identities (individuals) with events and assets.
What does identity correlation do?
Identity correlation provides additional information about the users involved in events. This information can be used to correlate multiple events to a single person, identify the owner of a host, determine whether an individual is subject to special attention, and more. Specifically, identity correlation provides the following:
Prioritization
The same type of access events initiated by two different users may not deserve the same level of attention; a medium severity pattern of behavior from a graphic designer's account is less urgent than the same pattern from a database administrator's account. Identity correlation allows an urgency to be computed based on the priority of individuals so that higher urgency is assigned to high priority individuals.
Categorization
Identity correlation allows information about the individuals involved to be added to events. For example, identity correlation lookups can be used in a correlation search to indicate whether the user is subject to a compliance regulation.
Normalization
Identity correlation allows accounts to be normalized and determine whether two events relate to the same individual. For example, one person may have different account names for email, ERP, and ITIL systems that they use frequently. Identify correlation helps the security analyst determine that access events for all three systems are from the same person.
Why is identity correlation important?
Identity correlation provides additional fields as part of an event to automatically designate the identity associated with the event. This makes it possible to find events for an identity and find identities for an event. Where possible, identity correlation uses session information to help match events to a session, and a session to an identity.
What is an identity?
An identity represents a user of the system. An identity can have multiple identity-related fields in the field context menu. Identity correlation will consider each of these fields in order to match the identity with the respective events.
Additionally, identities include information that describes the priority and business unit of the identity. Identities can also be put into categories to define the role of the identity or the functional area to which it belongs.
How can identity correlation be used?
The Identity Search option allows one to search for identities from anywhere that identity-related information is found in a field context menu. These searches use the Asset and Identity Search tool to look for any match in these fields. This makes it possible to:
- Update the identity lookup in the lookup editor with identities
- Automatically apply identities instantly, even for events in the past
Identity related fields are listed under Customizing identities in this topic.
How identity correlation works
Identity correlation is used to reconcile and validate the ownership of different user names that reside on systems and applications throughout the organization, and to permanently link ownership of those user names to particular individuals.
Identities (people) can operate under many different user names. For example, a person could log in as:
- jhsmith
- james_smith
- js842@gmail.com
- team.leader12
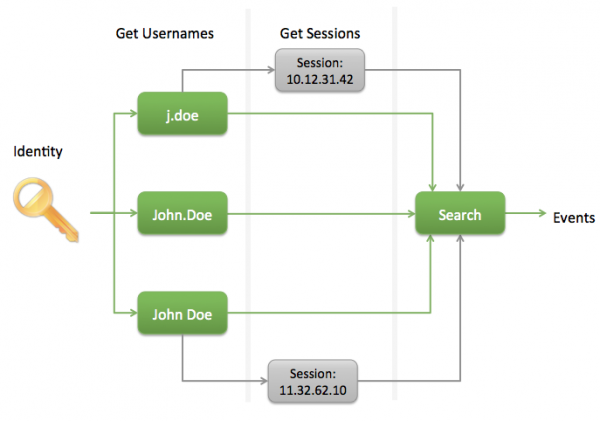
An identity search includes all of the user names for a given identity. To find events associated with an identity, Splunk searches for user names and then searches for session information to create a list of events.
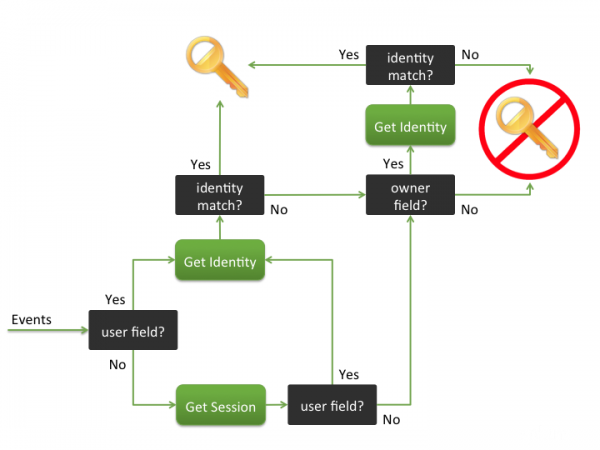
To associate an event with an identity, the event is searched for a user field, a session, or an identity field. When an identity is found, identity matching may take place to see if there are other associated user names.
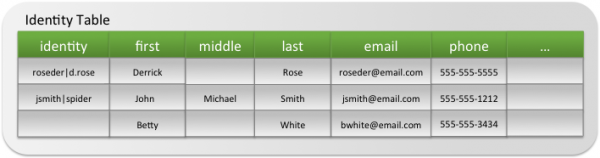
Identity matching
Identity matching is done by comparing user names associated with an event with identities in the Identities table. Splunk identity match configurations are specified using the identities.conf file. An Identity table might look like this:
Customizing identities
To view, modify, or change an Identity list, browse to Configure > Data Enrichment > Identities. Edit the content, or paste the new values in. The editor does not validate input.
Alternatively, the data can be saved as a .csv file and be placed into the path: $SPLUNK_HOME/etc/apps/SA-IdentityManagement/lookups/identities.csv . A .csv file must use UNIX line endings. Update the list periodically to ensure that Splunk App for Enterprise Security has current information.
It is possible to configure a scripted input to automatically populate the list if it is contained within a database. Automatic identity updates can be done using a combination of scripted inputs and custom search commands.
Splunk automatically loads the Identity list at search time and does not need to be restarted.
The table describes the fields in the Identities list:
| Field | Description |
|---|---|
| identity | A pipe delimited list of usernames representing the identity. This is a key field. |
| prefix | Prefix of the identity. Example: Dr. |
| nick | Nickname of an identity. |
| first | First name of an identity. |
| last | Last name of an identity. |
| suffix | Suffix of the identity. Example: Jr. |
| Email address of an identity. | |
| phone | A telephone number of an identity. |
| phone2 | A secondary telephone number of an identity. |
| managedBy | A username representing the manager of an identity. |
| priority | The assigned priority of an identity. Example: CTO = critical |
| bunit | A group or department classification for identities. |
| category | A logical classification for identities. Examples: Privileged, Officer, Intern, Contractor. |
| watchlist | The identity is on the watch list. Example: TRUE. See "User Activity Monitoring" in this manual. |
| startDate | The start or hire date of an identity. Example, 7/3/95 15:30 |
| endDate | The end or termination date of an identity. Example, 12/31/14 19:55 |
| work_city | The primary work site City for an identity. |
| work_country | The primary work site Country for an identity. |
| work_lat | The latitude of primary work site City in DD with compass direction. Example: 37.78N |
| work_long | The longitude of primary work site City in DD with compass direction. Example: 122.41W |
To validate changes to the identities list, use the "Identity Center" dashboard to view identities by priority, by business unit, and by category.
| Asset management | An Extreme search example |
This documentation applies to the following versions of Splunk® Enterprise Security: 3.3.0, 3.3.1, 3.3.2, 3.3.3
 Download manual
Download manual
Feedback submitted, thanks!