Integrate ITSI with Splunk Add-on for Jira Cloud
Integrating Splunk Add-on for Jira Cloud with IT Service Intelligence (ITSI) enables users to do the following:
- Create tickets in a Jira platform from ITSI through episode actions.
- Create and update tickets in a Jira platform from ITSI through automated action rules in notable event aggregation policies.
For an overview of all ticketing integrations available for ITSI, see Overview of episode ticketing integrations in ITSI.
Set up the integration
Perform the following steps to set up a basic integration with Jira
Prerequisites
| Requirement | Description |
|---|---|
| ITSI role | You must have the admin role to set up integration with Splunk Add-on for Jira Cloud. |
| Splunk Add-on for Jira Cloud | You must have the Splunk Add-on for Jira Cloud version 2.1.0 or later. |
Install and configure the Splunk Add-on for Jira Cloud
Install the Splunk Add-on for Jira Cloud on your Splunk instance. The add-on is required to send ITSI episodes to Jira. Download the app from Splunkbase. For setup instructions, see Set up Splunk Add-on for Jira Cloud.
Test the integration
When you're ready to start creating Jira incidents from ITSI, test your integration by going to Alerts and Episodes in ITSI. Select an episode, then select the Actions menu. If the add-on is correctly configured, Jira Cloud Issue Integration is displayed in the list of available options.
To create a ticket, see Create a ticket in Jira and follow the steps there.
The initial integration is unidirectional, so updates to the Jira ticket aren't reflected in ITSI. To configure a bidirectional integration, see the next section.
Set up a bidirectional integration with Splunk Add-on for Jira Cloud
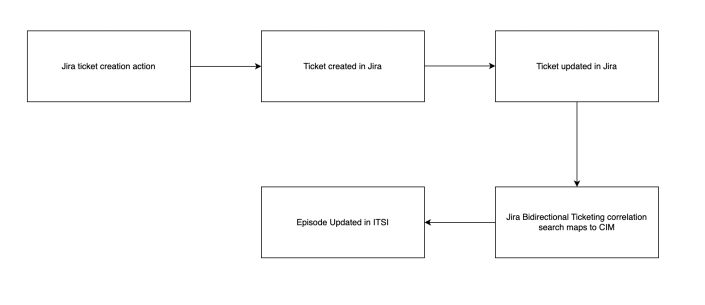
A bidirectional integration exchanges data between your ITSI instance and Jira so that when you make an update to a Jira ticket, the episode information is also updated within ITSI.
The following diagram shows the initial flow of the bi-directional ticketing:
Install the Common Information Model
ITSI leverages the Ticket Management data model in the Splunk Common Information Model (CIM) to normalize data, using the same field names and event tags for equivalent events from an external ticketing system. See Ticket Management in the Common Information Model Add-on Manual.
This normalization enables you to create action rules for fields like priority, severity, and state without having to remember what they're called in Jira. See Overview of the Splunk Common Information Model for an introduction to the data models and information about the fields and tags they use.
Install the Common Information Model Add-on (CIM) from Splunkbase. To determine the correct version to install, see ITSI compatibility with other apps and add-ons in the Install and Upgrade Manual.
Configure the incident data input
Follow the below steps to configure the incident input in Splunk Add-on for Jira Cloud:
- In Splunk Web, select the Splunk Add-on for Jira Cloud icon in the Apps sidebar.
- Select the Inputs tab to navigate to the Splunk Add-on for Jira Cloud Inputs configurations.
- In the Inputs tab, select Create New Input to create a new input for Incidents.
- Follow the steps in Configure inputs for the Splunk Add-on for Jira Cloud to configure the input.
- Enable the input in the Status column.
Enable the Jira Bidirectional Ticketing correlation search
ITSI includes a Jira Bidirectional Ticketing correlation search that queries Jira events and sends an event to the itsi_tracked_alerts index each time an update is made. The correlation search also maps Jira fields to the CIM fields. For more information, see Ticket management in the Common Information Model Add-on Manual.
The Bidirectional Ticketing correlation search is disabled by default. To enable it, perform the following steps:
- From the ITSI main menu, select Configuration > Event Management > Correlation Searches.
- Enable the Jira Bidirectional Ticketing correlation search.
(Optional) Specify the index to look at for available fields
When you configure action rules in the next step, ITSI pre-populates all possible fields and values from the main index. If your data is going into a different index, you can specify which index ITSI looks at when populating these fields:
- Open Jira Bidirectional correlation search.
- Update the first parameter (write the index name instead of main) of the macro provided into the search.
Alternatively, you can also do the following:
- Open or create a local macros.conf file at
$SPLUNK_HOME/etc/apps/SA-ITOA/local/. - Under the
[itsi_event_management_jira_issues]stanza, specify the index in the definition setting. For example:
[itsi_event_management_jira_issues] args = definition = index=myspecialindex sourcetype=jira:cloud:issues
Configure action rules to sync Jira ticket fields
Configure notable event aggregation policy action rules that update the fields in the ITSI episode when they change in Jira.
- From the ITSI main menu, click Configuration > Event Management > Notable Event Aggregation Policies.
- Open an existing custom notable event aggregation policy that creates episodes you'll send to Jira.
To use the bidirectional integration, you must create a custom aggregation policy instead of using the default aggregation policy.
- Go to the Action Rules tab.
- Select Add Rule.
- Select the Jira issue associated with this episode from the drop-down list. This option only displays if the CIM add-on and Splunk Add-on for Jira Cloud are installed.
- Build out your aggregation policy so that each important change in Jira has an action rule that updates the corresponding episode in ITSI.
- Repeat these steps for each aggregation policy you want to integrate with Jira.
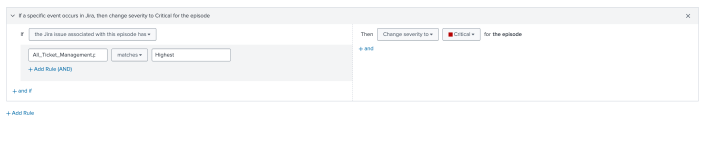
For example, the action rules for state changes might look like this:
Test the integration
Test the integration to make sure you configured the fields correctly.
- Go to Episode Review and link a ticket to an episode using Jira Cloud Issue Integration, created by the aggregation policy configured to an incident in Jira.
- Go to your Jira ticket and update one of the field values for which an action rule is created. For example, change the ticket priority from Low to Highest.
- Go back to Episode Review in ITSI and confirm that the corresponding field was updated within the episode. The field might take several minutes to update.
Automate Jira ticket creation
Configure notable event aggregation policy action rules to create and update Jira tickets when certain conditions are met.
- Within ITSI, select Configuration > Notable Event Aggregation Policies.
- Open the aggregation policy you want to integrate with Jira.
- Go to the Action Rules tab.
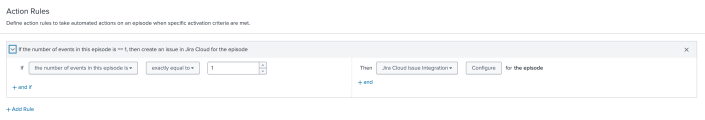
- Select Add Rule and configure trigger conditions for when to create a Jira ticket, as in the following example:
- Select Configure and configure the fields.
- Optionally, configure additional action rules to update the Jira ticket priority when the corresponding ITSI episode changes. For example, you might create an action rule to change the Jira ticket priority to Low if the ITSI episode's severity is equal to Normal.
For more information about configuring action rules, see Configure episode action rules in ITSI.
Avoid creating or updating the Jira ticket for each and every incoming event. Instead, use specific conditions such as "exactly equal to" or "if the following event occurs."
Update a Jira ticket
To update a created Jira ticket, follow the steps in the Automate Jira ticket creation section exactly as if you were creating a new incident, but only fill out the fields in the form that you want to update. For example, if you only want to update the incident's priority, only fill out the priority field, and leave the other fields blank.
When an action rule to create a Jira ticket runs multiple times on the same episode, the existing ticket is updated each time.
| Integrate ITSI with BMC Remedy or BMC Helix | Integrate ITSI with PagerDuty |
This documentation applies to the following versions of Splunk® IT Service Intelligence: 4.19.0, 4.19.1, 4.19.2, 4.19.3, 4.19.4, 4.20.0, 4.20.1
 Download manual
Download manual
Feedback submitted, thanks!