 Download topic as PDF
Download topic as PDF
Common terms in Splunk Intelligence Management
Splunk Intelligence Management uses the following common terms and definitions:
- Analytics
- The capability in Splunk Intelligence Management that uses Mean Time to Detection (MTTD) and Mean Time to Response (MTTR) metrics to analyze the performance of security systems. Tracking these metrics helps to understand how much coverage your intelligence sources provide and determine ways to increase coverage. For more information on the analytics capability of Splunk Intelligence Management, see Use analytics to detect and resolve threats faster.
- Approved Indicator
- When you enrich an observable into an Indicator, that data object contains attributes that provide context, such as scores, tags, and other information. You can review these Indicators and filter them into a specific Enclave to create a group of Indicators that are clearly malicious to your business. Splunk Intelligence Management refers to these as approved indicators.
- Attribute
- A piece of data that adds context to an Indicator, such as a tactics, techniques, and procedures (TTP), a campaign, a malware family, or a threat actor. Attributes help Splunk Intelligence Management to categorize an indicator as malicious.
- Attributes Parser
- Feature in Phishing triage and Normalized indicator scoring.
- Campaign
- A group of incidents, TTPs, and threat actors that work together on an attack. An Indicator might include campaign information as an attribute that provides context for its maliciousness.
- Capabilities
- The processes you build in Splunk Intelligence Management to connect and leverage intelligence across your ecosystem of tools, teams, and partners. Capabilities include governance, workflows, advanced searching, scoring, and analytics. For more information on the capabilities of Splunk Intelligence Management, see Unify security operations using the capabilities of Splunk Intelligence Management.
- Collection
- Data collection is the first step in the Intelligence Pipeline, where you import internal events and intelligence sources. You can send data to Splunk Intelligence Management using workflow applications, managed connectors, email, custom scripts, or the Splunk Intelligence Management Web App. For more information on how data collection and processing works in Splunk Intelligence Management, see How data processing works in Splunk intelligence Management.
- Community enclave
- A community enclave is available to all users. Any individual user can submit information to this type of enclave. For example, Splunk Intelligence Management created the COVID-19 OSINT community enclave to help identify malicious data related to the COVID-19 pandemic. For more information on trusted community intelligence sources, see Trusted community intelligence sources.
- Correlation
- The process of matching new data with existing data in Splunk Intelligence Management. For example, a new observable submitted to a Splunk Intelligence Management enclave is automatically correlated with data in all the enclaves that you can access within Splunk Intelligence Management. You can also correlate reports between enclaves using a custom script.
- Coverage
- The surface area of where intelligence sources add labels to unlabeled data in the form of scores or context. The goal of threat intelligence is to maximize this coverage by choosing the best sources for your organization based on budget constraints.
- Data-centric security automation
- Feature that helps to manage intelligence separately from the applications where you automate actions. For example, your organization might use a detection tool that can identify malicious data. Rather than import sources into that detection tool, you can export the data to an Intelligence Management Platform that enriches the data by correlating it with intelligence sources and return the enriched data to the detection tool and other tools in your workflow, such as SOAR or SIEM tools. For more information on automating security operations using Splunk Intelligence Management, see Automate security operations using Splunk Intelligence Management.
- Enclave
- A cloud-based data repository with access control where you organize and store events or intelligence in Splunk Intelligence Management. Following are the possible enclave categories:
Event Enclaves: Stores raw data that comes in to Splunk Intelligence Management as cases, alerts, events, emails, logs, and so on. Splunk Intelligence Management includes the following types of event enclaves:
- Internal: Raw data such as logs and cases from your organization
- Phishing Triage: Raw emails sent to Splunk Intelligence Management as part of the Phishing Triage feature
Intelligence Enclaves: Stores enriched data used in workflows to determine if an event is malicious or benign. Splunk Intelligence Management supports the following types of intelligence enclaves:
- Historical intelligence
- Sharing
- Community
- Open Source Intelligence
- Premium Intelligence
For more information on enclaves, see Use enclaves to organize your intelligence.
- Enclave inbox
- An email inbox directly connected to a specific enclave. You can use this feature to submit incident and alert information directly to your enclaves using email. Process emails sent to this inbox and submit them to the enclave every minute.
- Enrichment
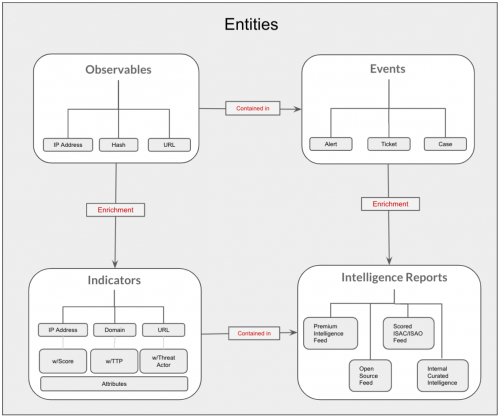
- As part of the Intelligence Pipeline, Splunk Intelligence Management queries all the intelligence enclaves that you can access for matches with the processed observables. Add all information found in those enclaves to the observable, which enriches and transforms the observable into an indicator.
- Entity
- A concept used by Splunk Intelligence Management to categorize and manage data types.
- Event
- An event in Splunk Intelligence Management is an anomalous behavior or activity that you capture through your internal systems, such as an alert, email, case, or issue. Each event contains one or more observables. Store events submitted to Splunk Intelligence Management in event enclaves.
- Governance
- Governance is how you manage control and permissions in Splunk Intelligence Management, including multi-factor authentication and enterprise-level single sign-on (SSO). The core of governance within the Splunk Intelligence Management platform is the seamless control and secure dissemination of data using enclaves. For more information on governance, see Governance: Manage and control permissions.
- Historical intelligence
- Refers to an organization's curated data from incidents and investigations, which includes Internally generated reports, closed cases and associated tags. Historical intelligence is the most useful source for the security workflow because it contains the most relevant and approved context compared to external sources. See also Internal Data.
- Indicator
- An entity or data object, such as a URL, an IP address, a hash, or an email address associated with an attribute or set of attributes. Indicators establish a baseline for the maliciousness of an entity. See also Approved indicator.
- Indicator prioritization
- An intelligence workflow that takes indicators from the selected sources and prioritizes them using normalized indicator scores and attributes, filters them by specific factors, and sends the Indicators that remain to either an enclave or to a third-party tool.
- Intelligence management platform
- A tool or platform such as Splunk Intelligence Management that helps you to manage internal and external intelligence sources to accelerate the detection of and response to malicious events.
- Intelligence pipeline
- An intelligence pipeline can improve data quality by eliminating outdated or incorrect elements and normalizing data from multiple sources into a single data model and schema, regardless of the original data structures. The intelligence pipeline provides the highest fidelity intelligence in structured outputs such as JSON that support automated actions in your security workflows. For more information on how data collection and processing works in Splunk Intelligence Management, see How data processing works in Splunk intelligence Management.
- Intelligence report
- An intelligence report contains one or more indicators and related attributes that can help provide context to determine if an event is malicious or benign.
- Intelligence source
- The Splunk Intelligence Management includes a variety of data sources that provide information about events and observables. Some of these sources are external, such as open source intelligence and premium intelligence. Others are internal, such as the historical intelligence generated by an organization. See also Threat intelligence.
- Intelligence workflow
- A no-code process to create customized intelligence pipelines that automate data processing. For each pipeline, you can select the sources, the transformations, and the destinations for the enriched data. Splunk Intelligence Management offers two standard intelligence workflows: Phishing Triage and Indicator Prioritization. For more information on intelligence workflows, see Intelligence workflows to automate data processing and distribution.
- Internal data
- The raw data generated within your organization, such as logs, emails, and network traffic. This raw data is what you submit to Splunk Intelligence Management for enrichment and then share internally and externally to assist in security investigations and detections. You store internal data in an event enclave. See also Historical intelligence.
- JSON
- An open standard, lightweight data-interchange format. JSON uses human-readable text to store and transmit data objects consisting of attribute–value pairs and array data types.
- Malware family
- A group of applications with similar attack techniques. An Indicator might include information about a malware family as an attribute that provides context for the Indicator's maliciousness.
- Managed Connector
- A lightweight plug-in that provides a one-way connection between Splunk Intelligence Management and a third-party Intelligence Source or workflow application. Built using the Splunk Intelligence Management Unified API, managed connectors are available through the Customer Success organization for Splunk Intelligence Management.
- MTTD (Mean time to detection)
- Duration of time when a potential threat enters the network and when you prioritize it for action or dismiss it as a viable event. One example of this is an email containing a URL. The MTTD is the total time from when that email enters the organization's network until the time you take to mark it as malicious or safe.
- MTTR (Mean time to resolution)
- Average amount of time it takes to respond to a threat. You determine the severity and nature of response based on context when you detect a suspicious event. Compare an email with a suspicious URL against known security issues and take action based on that information.
- MITRE ATT&CK
- A real-time knowledge base of observed adversary behaviors, which can be useful when investigating security incidents. Splunk Intelligence Management users can automatically extract MITRE ATT&CK techniques and tactics from premium intelligence sources. See also MITRE ATT&ACK framework.
- Normalized indicator score
- Splunk Intelligence Management converts all third-party scores for an Indicator into a single, standardized value, called a normalized indicator score. The scoring system for Splunk Intelligence Management uses a scale of 0-3, where 0 is Benign, 1 is Low, 2 is Medium and 3 is High. For example, a source might assign an Indicator the score of "Somewhat Malicious", which translates to 2 in the Splunk Intelligence Management scoring system. See also Normalized indicator scores
- Observable
- An entity, such as a URL, an IP address, a hash, or an email address. Observables do not always establish a baseline for whether an entity is good or bad, but they are useful to create relationships between two or more data entities that can lead to assigning a Safe or Malicious label to that Observable. Splunk Intelligence Management supports more than a dozen types of observables. See also Indicator.
- Open source intelligence
- A public data stream that is available to everyone, including blogs, RSS feeds, and Open APIs. This type of source is less curated and provides less valuable labels such as scores.
- Original indicator score
- A score assigned by any intelligence source to an Indicator. Because different sources score using different techniques, a single Indicator might have a High score from one source, a value of 9 from another source, and a Malicious score from a third source, leading to confusion when trying to determine the true maliciousness of that indicator. Splunk Intelligence Management normalizes these original indicator scores into a single normalized indicator score.
- Phishing triage
- An intelligence workflow that takes submitted emails and prioritizes them using normalized indicator scores and indicator attributes from your Intelligence Sources. The workflow stores those Indicators and events in an approved enclave automatically or through human intervention for use by security tools. For more information on phishing triage, see Use the phishing triage workflow to automate suspicious email triage.
- Premium intelligence source
- Privately maintained data sources that require some commercial relationship with the provider or membership in a group, such as an ISAC/ISAO. The providers of these sources are intelligence specialists who curate and disseminate valuable enriched intelligence. See the list of premium intelligence sources.
- Priority event score
- Created when Splunk Intelligence Management aggregates normalized indicator scores for an event such as an email and assigns a score that reflects the overall priority of the event. Priority event scoring is available as part of the Phishing Triage feature. See also Priority event scores
- Priority indicator score
- Created when Splunk Intelligence Management enriches an Indicator by pulling original scores from intelligence sources, converting them to a single normalized indicator score, and then assigns a priority indicator score to that indicator, based on the maximum of the available normalized scores. Used in specific workflow tools, such as the Splunk Intelligence Management App for Splunk Enterprise Security (ES). see also Priority indicator scores
- Redaction library
- The list of terms specified by your organization for removal from a report before sharing or exporting it from Splunk Intelligence Management. For more information on the redaction library, see Use the redaction library to modify reports.
- Safelist
- The list of observables that are not processed for your organization's users. This feature does not support the use of wildcards or CIDR blocks. For more information on configuring the company safelist, see Configure the company safelist to ignore certain indicators.
- Scripted Extension
- A REST API script that Splunk Intelligence Management has created to manage data in Splunk Intelligence Management enclaves and to exchange data with third-party applications. See also Managed Connectors.
- Search
- The capability that provides advanced searching and filtering using attributes, tags, and notes attached to Indicators. You can use either the Splunk Intelligence Management REST API or the Splunk Intelligence Management Web App to search for an Indicator and then view a summary of it or deep-dive into Intelligence Reports that contain that Indicator.
- Sharing enclave
- A data repository that is available to members of a specific ISAC or ISAO organization. For example, the RH-ISAC sharing enclave is available to members of the retail and hospitality ISAC.
- Threat actor
- Data that identifies or describes an adversary. This data can include motivations, desired results, and historical behavior. An Indicator might include information about threat actors as an attribute that provides context for the Indicator's maliciousness. Similar to other Indicators, threat actors are searchable using the web and API and extracted in a graph visualization. Splunk Intelligence Management maintains an extensive list of threat actors, developed from internal sources as well as external sources, such as MITRE.
- Threat Intelligence
- Threat Intelligence provides an outside opinion, or context, on observables, such as maliciousness or attributes that can include actors, campaigns, malware, CVEs, and other non malicious objects. You can combine external intelligence sources with your internal historical data to label and score internal events or suspicious alerts, automating the process of investigation and accelerating your response to events. See also Intelligence source.
- Splunk Intelligence Management Python SDK
- A Python package to interact with the Splunk Intelligence Management Rest API from within any Python program. It is compatible with both Python 2 and Python 3; however some of the example scripts that use the package target Python 2. For more information on Python SDK, see Use the Python SDK to interact with the REST API.
- Splunk Intelligence Management REST API
- The REST API supporting programmatic access to the full range of Splunk Intelligence Management capabilities. The REST API offers a set of unified endpoints that you can use to access, clean, and normalize intelligence across multiple sources, then send it to specific destinations, such as teams, tools, or Splunk Intelligence Management enclaves. For more information on REST API, see REST API version 1.3 and REST API version 2.0.
- Splunk Intelligence Management Web App
- A lightweight browser-based tool that you can use to manage users, enclaves, whitelisting, redaction, workflow, searches, and more. For more information on the web app, see Overview of the Splunk Intelligence Management web app.
- TTP (tactics, techniques, and procedures)
- Denotes how adversaries operate, such as intended victims, patterns, and malware used, and what tools and personas they use in their attacks. An Indicator might include TTP information as an attribute that provides context for its maliciousness.
- Use Case
- Use cases in the Splunk Intelligence Management platform cover how most cybersecurity professionals work:
- Detect: Make detection workflows more accurate by reducing false positives.
- Triage: Leverage internal and external sources to identify malicious versus safe items for prioritizing new events as they occur.
- Investigate: Enrich data in by searching for Indicators across all available sources, then deep-dive into source intelligence reports to get context.
- Disseminate: Customize, control, and share intelligence with tools, teams, and communities.
- Workflow app
- A fully functional, bi-directional integration with a third-party tool. These purpose-built applications can assist in detecting security events, enriching alerts and incident investigations, or streamlining intelligence management in response and orchestration applications.
|
PREVIOUS Deprecated Features |
NEXT Policy for API usage in Splunk Intelligence Management |
This documentation applies to the following versions of Splunk® Intelligence Management (Legacy): current
Feedback submitted, thanks!