 Download topic as PDF
Download topic as PDF
Use cases for Splunk Intelligence Management
The product architecture of Splunk Intelligence Management focuses on the following use cases:
- Detect: Make detection workflows more accurate by reducing false positives.
- Triage: Leverage internal and external sources to identify malicious items while prioritizing new events as they occur.
- Investigate: Enrich data by searching for indicators across all available sources and deep-dive into source intelligence reports for context.
- Disseminate: Customize, control, and share intelligence with tools, teams, and communities.
Improve detection workflows to reduce false positives
Use Splunk Intelligence Management to achieve the following goals:
- Optimize detection workflows for better accuracy.
- Automate the matching of high-scoring indicators into a SIEM tool and create more efficiency.
- Customize data ingest preferences to reduce false positive rate.
The following image illustrates how to improve Splunk Intelligence Management detection workflows:
Use the following workflows to improve detection and reduce false positives:
- Sources: Send the internal event data to Splunk Intelligence Management. Use premium intelligence sources and open sources to normalize, score, and prioritize the event data.
- Transformations: Prepare and prioritize data to identify malicious Indicators.
- Destinations: Send indicators and intelligence reports back to the detection tool and reduce false positive rates.
Triage to prioritize events
Use Splunk Intelligence Management to achieve the following goals:
- Automatically run user-reported emails through the intelligence pipeline.
- Automatically prioritize events based on normalized scores.
- Streamline actions by connecting indicators and events with detection, incident review, or orchestration tools.
The following figure illustrates how to prioritize events using Splunk Intelligence Management's optional phishing triage feature:
Use the following workflows to triage and prioritize events:
- Sources: Send internal event data to Splunk Intelligence Management and use your intelligence sources to normalize, score, and prioritize events.
- Transformations: Prepare and prioritize events based on normalized scores.
- Destinations: Connect indicators and events with detection, incident review, or orchestration tools to streamline defensive actions.
Investigate using enriched data
Use Splunk Intelligence Management to achieve the following goals:
- Display enriched data from Splunk Intelligence Management in your workflows and applications to provide context as required.
- One-click access to the web app of Splunk Intelligence Management for deeper link analysis.
The following figure illustrates how to investigate using Splunk Intelligence Management:
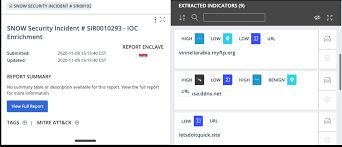
Use the following workflow to investigate using enriched data:
- Sources: Send internal event data to Splunk Intelligence Management to correlate with your historical, premium, and open intelligence sources.
- Transformations: Enrich and prioritize events with prepared and normalized data from your intelligence sources.
- Destinations: Automate and streamline the exchange of data between Splunk Intelligence Management and your case management tools. Use a link to jump to the Splunk Intelligence Management web app and view original intelligence reports and correlation with other intelligence sources.
Use Splunk Intelligence Management to achieve the following goals:
- Customize and control the flow of your data.
- Validate and share intelligence with the tools, teams, and communities that are essential to your security operations.
The following figure illustrates how to share intelligence using Splunk Intelligence Management:
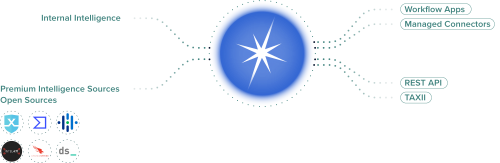
Use the following workflows to share intelligence and customize data flow:
- Sources: Send internal event data to Splunk Intelligence Management to correlate with OSINT and premium intelligence sources.
- Transformations: Redact and allow list indicators as appropriate and send to approved and community enclaves.
- Destinations: Share information internally and externally using the workflow applications for Splunk Intelligence Management, managed connectors, REST API, or TAXII infrastructure.
|
PREVIOUS Unify security operations using the capabilities of Splunk Intelligence Management |
NEXT Security compliance requirements to use Splunk Intelligence Management |
This documentation applies to the following versions of Splunk® Intelligence Management (Legacy): current

Feedback submitted, thanks!