Lateral Movement model
Lateral movement is a technique used by adversaries to enter and control remote systems on a network. Lateral movement is a common step in a security breach, used as an attempt to access and explore the targeted network. Adversaries explore the network laterally until they find what they are looking for, such as a database server, a file server, or an email server.
The Lateral Movement model uses advanced graph computation, sequence analysis, and various anomaly detection algorithms. This batch model collects internal activity data from various sources such as Active Directory Logs, Firewall, and EndPoint. The model also captures anomalies related to the lateral movement of users and devices that are critical to the environment, based on watchlists you define.
By default, the model uses 30 days of activity data. This value is configurable.
In UBA version 5.3.0, enhancements are available that improve the detection capabilities of the model:
- New types of Windows events and processes are now supported.
- For Windows events, see Windows events supported by Lateral movement model.
- For processes, see Supported processes.
- To reduce false positives, the model compares entity activities with peer groups and with newly integrated security rules.
- Security configurations, including allow list and deny list processes, are updated to accommodate support for new operating systems.
Viewing Lateral Movement
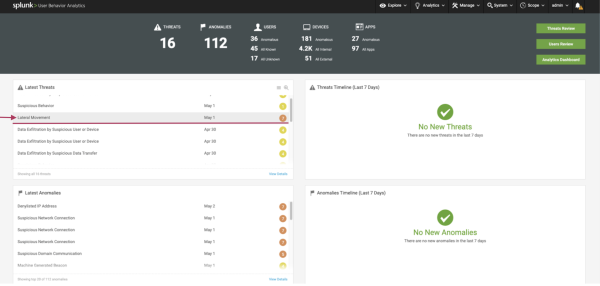
From the front page of Splunk UBA open the Latest Threats panel. Confirm you see Lateral Movement listed. You can then see the details of any Lateral Movement threats including the following information
- Detection Date: The most recent date that the threat was triggered.
- Last Update: The latest time the model was executed.
If no Lateral Movement is listed, no threat has been detected.
The following image shows an example of the UBA front page and the Latest Threats panel:
Example scenario
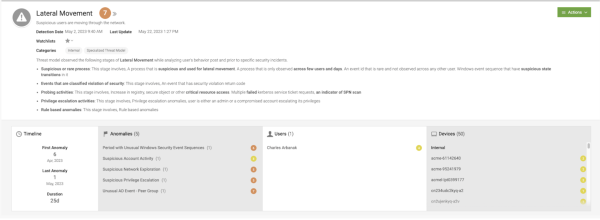
The following example scenario identifies an intruder. The timeline spans from April 6, 2023, to May 1, 2023, with a total duration of 25 days.
The following image shows the example intruder as they appear in Splunk UBA:
Lateral Movement progresses through several stages, each following a specific sequence to accomplish an objective:
- In the initial stage, a suspicious process is observed across multiple users over several days. This event is considered rare as it is not observed among other users. These events generate anomalies categorized as Period with Unusual Windows Security Event Sequences.
- After a few days, the model detects an event with a security violation return code. Intruders typically exhibit slower actions during the early stages of lateral movement.
- Subsequently, probing activities and privilege escalation activities are detected. A regular user cannot traverse an organization with their assigned privileges, so the intruder must escalate their privileges to expand their reach.
- Once the intruder successfully acquires additional access privileges, multiple actions are taken. In this example, on May 1, 2023. As the intruder's login pattern and device access might differ from their peers, unusual Windows events are detected by the peer group-based security rules. The user-interface displays all 50 devices associated with the various stages of lateral movement.
View the Threat Relations
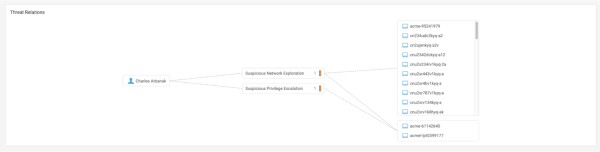
You can also view Threat Relations and see all the devices that have been affected by a specific user. The following image shows the Threat Relations panel with example data:
By examining the relationships between the target account/user and the devices, you can gain insights into the types of triggered anomalies that were detected when the target user accessed those devices. This feature helps you understand the security implications and potential risks associated with the user-device interactions within your environment.
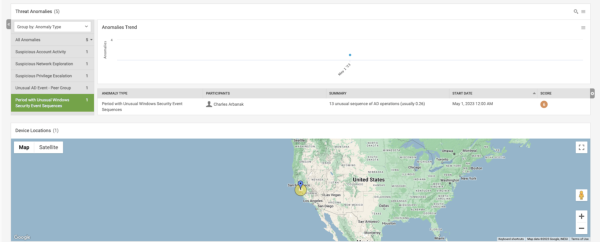
View the Threat Anomalies Timeline
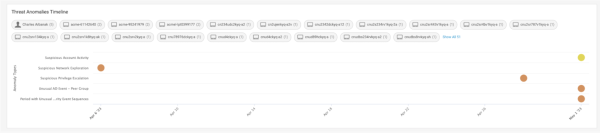
The Threat Anomalies Timeline provides an alternative perspective on the progression of each stage in a lateral movement scenario within your systems. The following image shows the actions taken by the identified intruder over a span of time:
The intruder initiated activity on April 23 by exploring the network system. After several days, the intruder attempted to gain additional privileges for accessing resources. Within a brief timeframe, the intruder became more active and engaged in a series of suspicious account activities, carrying out abnormal windows operations that were detected by analyzing his peer groups. This timeline offers insights into the evolving nature of the threat and the associated anomalies detected at each stage.
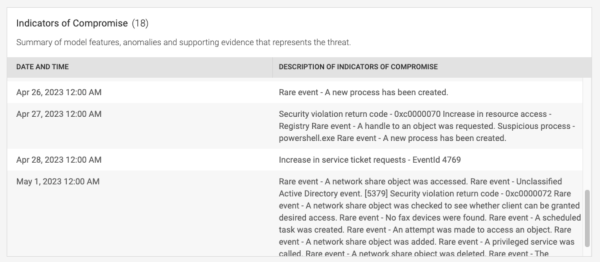
View the Indicators of Compromise
To gain a comprehensive understanding of the actions performed by intruders, the Indicators of Compromise provides a detailed account of all the abnormal activities observed within the system. The following image shows the Indicators of Compromise panel with example data:
You can see the specific violations committed by the user that contributed to the detection of potential threats. The model offers a customizable framework that enables you to update your allow list and deny list configurations for a tailored security solution.
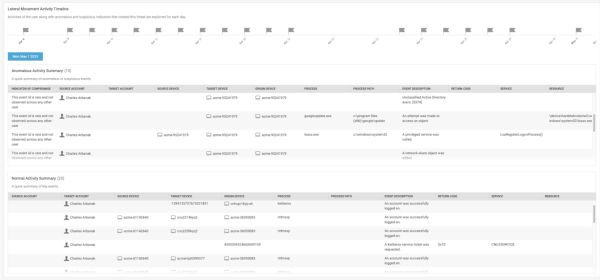
View the Anomalous Activity Summary
The Anomalous Activity Summary provides detailed information about each anomalous or suspicious event. The following image shows the Anomalous Activity Summary panel with example data:
Review the source and target accounts, devices, origin device, process, return codes, services, and event descriptions extracted from system logs. This overview can help you better understand potential security issues.
View the Device Location
The Device Location pinpoints the location of suspicious events and assigns risk levels to each event. You can use this information to prioritize investigations based on the severity of the risk associated with each event. The following image shows the Device Location panel with example data:
In this example, the identified intruder can be observed in a period of Unusual Windows Security Event Sequences in which the models compare the baseline (0.26) against 13 new and unusual events detected. This might indicate account compromise, takeover, or lateral movement from another account.
Supported processes
The following Lateral Movement model processes are supported. You can add new process names into the model configuration file.
| Process name | Description |
|---|---|
| arpspoof | Redirects packets from a target host (or all hosts) on the LAN intended for another host on the LAN by forging ARP replies. |
| bluecoat | AV appliances enable organizations to detect viruses, worms, spyware and trojans at the Web gateway. |
| cmd | In Windows operating systems, the Command Prompt is a program that emulates the input field in a text-based user interface screen with the Windows Graphical User Interface (GUI). It can be used to execute entered commands and perform advanced administrative functions. |
| fireeye | A modern endpoint protection platform combining traditional anti-virus with advanced real-time indicator detection and prevention. |
| keylogger | A keylogger or keystroke logger is a type of monitoring software that can be used to collect keystrokes that you type. |
| mcafee | Client-server solution that protects laptops, desktops, and servers in your network against malware, risks, and vulnerabilities. |
| mimikatz | An open-source application that allows users to view and save authentication credentials such as Kerberos tickets. |
| mousejiggler | Software that "fakes" mouse input to Windows. |
| mstsc | Command line interface to run the Microsoft Remote Desktop (RDP) client. Not necessarily malicious. |
| powershell | A task automation and configuration management program from Microsoft, consisting of a command-line shell and the associated scripting language. |
| symantec | Client-server solution that protects laptops, desktops, and servers in your network against malware, risks, and vulnerabilities. |
| wmiprvse | Windows Management Instrumentation Provider Service. Not necessarily malicious. |
| Batch models | VPN login related anomaly detection models |
This documentation applies to the following versions of Splunk® User Behavior Analytics: 5.3.0, 5.4.0, 5.4.1
 Download manual
Download manual
Feedback submitted, thanks!