Migrate from an unsupported version of the Splunk App for AWS
If you are migrating from version 3.X of the Splunk App for AWS to version 4.X, follow the instructions below to migrate.
Prerequisites
Before you can follow any migration steps, you must have followed all steps in the installation guide that applies to your environment. Installing the 4.X version of the app does not override the 3.X version, because they have different folder names. The two apps can exist side by side while you perform your migration steps. After you are finished migrating, you can disable the 3.X app.
Differences in functionality
If you have been using the Splunk App for AWS version 3.X, be aware of the following differences in functionality in 4.X:
- The Splunk App for AWS no longer defines indexes. All data goes to the main index by default. The new app includes the indexes aws-cloudtrail and aws-config, recommended by the 3.X app, in all relevant searches for backwards compatibility. Any new inputs that you create with the 4.X app index to
mainby default. - You can now configure your accounts and inputs using the Splunk App for AWS, using a Splunk account with administrator access. Previously, this configuration was only available through the add-on. See Add AWS accounts for the Splunk App for AWS for instructions on accessing and using the Configure tab, visible to Splunk administrators.
- You can continue to configure accounts and inputs using the Splunk Add-on for Amazon Web Services, which has a new and improved configuration UI of its own. Not all advanced configuration options are available through the Splunk App for AWS configuration, but you can access all previously available advanced settings through the add-on's configuration UI. Any configurations you save through the add-on are synced automatically with your app.
Some additional functional differences may apply, depending on your environment.
- If you are a Splunk Cloud user, and you have been using on-premises forwarders for data collection for the Splunk App for AWS 3.X, this is no longer required for 4.X. You can configure your AWS accounts and data inputs directly in your Splunk Cloud instance using the Configure tab in the app, which you can see if you are a member of the administrator role in Splunk Cloud.
- If you are an on-premises, distributed deployment Splunk Enterprise user, the 4.X app introduces a significantly different configuration option. The Splunk App for AWS now offers the ability to manage the configuration of your AWS accounts and inputs via the app UI on your search head, so you can manage your accounts and inputs from within the app rather than configuring inputs on your heavy forwarders using the Splunk Add-on for Amazon Web Services. See Install on a distributed deployment for details of the new distributed deployment instructions.
Migrate your existing input configurations
You can open any input configurations that you saved while using the Splunk App for AWS 3.X through the 4.X app and resave them. Regardless of what context you used when you saved the inputs before, resaving them from the 4.X app stores the input configurations in the Splunk Add-on for Amazon Web Services, where they are accessed by the app.
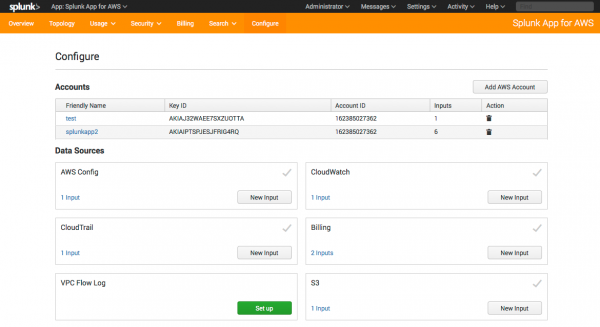
1. Go to the Configure tab in the app.
2. Your existing account information and input information appears in the new app, as shown.
3. In each box under Data Sources, click the link that indicates the number of inputs that you have.
4. For each input, click to open it, then click Save. This action saves the input configuration in the context of the add-on, where it can be read by the app.
When you resave the inputs from the app, the Splunk App for AWS makes some changes to the inputs to enforce some new requirements and settings required by the app. Specifically:
- Some input stanza names change in your configuration files to match the input naming standards of the app. For Config and CloudTrail, the app renames the input stanzas using the account friendly name, the AWS regions, and the queue names. For CloudWatch, the app renames the input stanzas using the account friendly name and the namespaces. There are no changes to the stanza names for Billing and S3 inputs.
- Some input stanzas that you configured as separate inputs merge into single inputs. For Config, CloudTrail, and CloudWatch, the app merges multiple inputs into a single entry per account friendly name. Billing and S3 inputs are not merged. Any advanced settings not visible in the Splunk App for AWS configuration UI merge as well, and the newly merged input uses the first value it finds for each setting. Thus, if you had configured different intervals, for example, in different inputs, the app resaves the input using the first configured interval value that it finds. To examine all the advanced settings of your merged inputs and adjust them if necessary, open your inputs using the Splunk Add-on for AWS. There, you can view and change advanced settings.
Migrate your custom dashboards
If you created any custom dashboards in previous versions of the app, migrate them to the new app.
1. Copy all dashboard xml files under $SPLUNK_HOME/etc/apps/SplunkAppForAWS/local/data/ui/views to$SPLUNK_HOME/etc/apps/splunk_app_aws/local/data/ui/views.
2. Modify $SPLUNK_HOME/etc/apps/splunk_app_aws/default/data/ui/nav/default.xml to include the custom views.
For any other customized knowledge objects, such as macros, saved searches, or alerts, the same process applies. Copy the object files or stanzas from the old version of the app to the equivalent file in the new app.
If you are using Splunk Cloud and cannot access the file system, contact support for assistance.
After you have migrated all your inputs, dashboards, and any other custom content, you can safely disable and remove the old app.
View legacy data in your dashboards
All data that you indexed using a previous version of the app and the add-on is available in the 4.X app dashboards, with the exception of CloudWatch data. The Splunk Add-on for AWS added a new field, aws_account_id, to help you filter data to specific AWS accounts. This field is required in dashboards using CloudWatch data. Because CloudWatch data collected with previous versions of the add-on lacked this field, it does not appear in your dashboards.
| Install the Splunk App for AWS on Splunk Enterprise | Add AWS accounts for the Splunk App for AWS |
This documentation applies to the following versions of Splunk® App for AWS (EOL): 4.0.0
 Download manual
Download manual
Feedback submitted, thanks!