Extract Fields
In the Extract Fields section, parse the data in your sourcetypes to create field extractions. The sourcetypes you created in the previous section appear in the Select a sourcetype dropdown list.
Parse data
To parse the data for a sourcetype and extract fields:
- On the Step 4: Extract Fields page, select the sourcetype and click Parse.
- If the sourcetype has already been parsed (indicated next to the sourcetype name), click Load Results to retrieve the field extractions you have already parsed.
Supported formats
The Field Extractor does not fully support the following formats:
- JSON
- XML
- Tabular formats, such as CSV and TSV
The Add-on Builder prompts you to skip this step if you provide data in any of these formats. However, you can try to parse data anyway. If you have sample data in JSON or XML format, go back to Section 3: Upload Sample Data and edit the sourcetype by adding the following advanced setting:
- Name: KV_MODE
- Value: auto
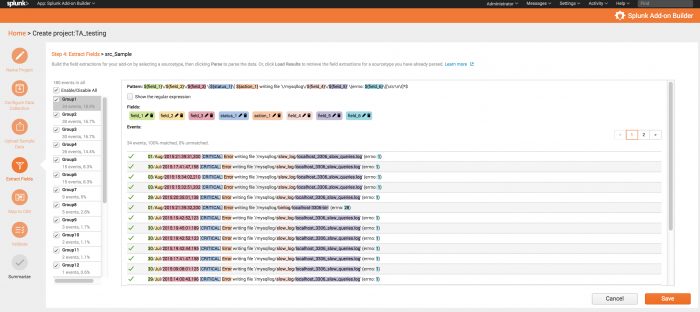
Extract fields
After parsing data, the results of parsing are displayed in the Field Extractor, which is based on the same Field Extractor in Splunk Enterprise. The Add-on Builder's Field Extractor displays a selection of events in groups, along with the fields that were extracted.
Here are some of the actions you can perform:
- Select one or more groups that best represent the data.
- If you are familiar with creating regular expressions, you can display the regular expression that the Field Extractor used, and modify it to improve the field extraction.
- Click on individual fields to include or exclude them.
- Edit the names of fields.
- Delete fields.
When you are satisfied with the results, click Save. A summary of the field extraction is displayed—click Save again.
Troubleshooting
What if I need to upload different sample data?
If you decide that you need to upload a different sample data file for a sourcetype, for example you want to clean the data first, you can return to Step 3: Upload Sample Data and upload additional data files. When you parse this sourcetype again, you can select only the groups from the newer file.
Can I delete sample data?
You cannot delete any events that have been indexed using the Add-on Builder. However, you can delete all events for a sourcetype manually using Splunk Search. For example, in the search bar, enter:
index=add_on_builder_index sourcetype="<sourcetypename>" | delete
You must have delete privileges to perform this action.
A regular expression had too many capture groups, what do I do?
This error is displayed after attempting to parse a file, and the regular expression created by the Field Extractor contains more than 100 capture groups (fields).
This error might indicate a problem with the Event Break setting for the sourcetype:
- Go back to Step 3: Upload Sample Data.
- Edit the sourcetype and select a different option for Event Break.
- Upload the sample events again. Because the Event Break option is applied when indexing the data, changing this value does not affect events that have already been indexed.
- Parse the data again.
The sample data might contain an event that is too long:
- Edit the sample data file by splitting the long lines to clean up the data.
- Go back to Step 3: Upload Sample Data.
- Upload the sample events again.
- Parse the data again.
Learn more
For more information, see the following Splunk Enterprise documentation:
- About fields in the Knowledge Manager Manual
- Build field extractions with the field extractor in the Knowledge Manager Manual
- Field Extractor: Select Fields step in the Knowledge Manager Manual
| Upload Sample Data | Map to CIM |
This documentation applies to the following versions of Splunk® Add-on Builder: 1.0.0, 1.0.1
 Download manual
Download manual
Feedback submitted, thanks!