Data requirements for the Content Pack for Monitoring Citrix
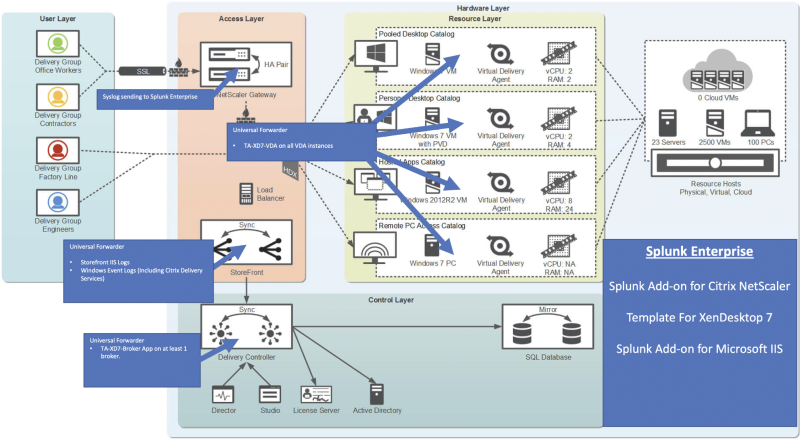
The Content Pack for Monitoring Citrix requires that you install several Citrix add-ons to collect and send data to your Splunk deployment. The following diagram describes where to install each add-on:
Install the Splunk Add-on for Microsoft IIS
Download the Splunk Add-on for Microsoft IIS from Splunkbase. The add-on allows a Splunk software administrator to collect Web site activity data in the W3C log file format from Microsoft IIS servers. For detailed installation instructions, see Install the Splunk Add-on for Microsoft IIS.
Adjust StoreFront KV setup
StoreFront doesn't follow the same naming convention as the default IIS logs. You have to modify the formatting of the defined transform in order for StoreFront IIS data to use the appropriate field list.
- Within ITSI, go to Settings > Fields > Field transformations.
- Change the app context to Splunk Add-on for Microsoft IIS.
- Open auto_kv_for_iis_default, which is the only transform that comes with the IIS add-on.
- The field list for the transform is the default listing for internet information services log types. Change the field list to the following in order for the StoreFront logs to properly parse:
date time s-sitename s-computername s-ip cs-method cs-uri-stem cs-uri-query s-port cs-username c-ip cs-version cs(User-Agent) cs(Cookie) cs(Referer) cs-host sc-status sc-substatus sc-win32-status sc-bytes cs-bytes time-taken
- Click Save.
This change might have downstream affects, such as breaking other data sources leading to other IIS logs not parsing properly.
Install the Template for Citrix XenDesktop 7
Download the Template for Citrix XenDesktop 7 from Splunkbase. The Template for Citrix XenDesktop 7 is comprised of two add-ons: the XenDesktop brokers and the XenDesktop VDAs. These add-ons contain the knowledge objects and index creation required to start collecting Citrix data. If you're in a distributed environment, you need to deploy some components to your indexers and some to the search heads as there is index creation, or you can create those indexes manually. For detailed installation instructions, see Template for Citrix XenDesktop 7 Installation on GitHub.
Install the Splunk Add-on for Citrix NetScaler
Download the Splunk Add-on for Citrix NetScaler from Splunkbase. The add-on handles the sourcetypes for NetScaler Syslog data. For installation instructions, see Install the Splunk Add-on for Citrix NetScaler.
| Release notes for the Content Pack for Monitoring Citrix | Install and configure the Content Pack for Monitoring Citrix |
This documentation applies to the following versions of Content Pack for Monitoring Citrix: 1.0.2
 Download manual
Download manual
Feedback submitted, thanks!