Identity dashboards
The Identity dashboards correlate host information to assets and provides additional information about the source and targets of events.
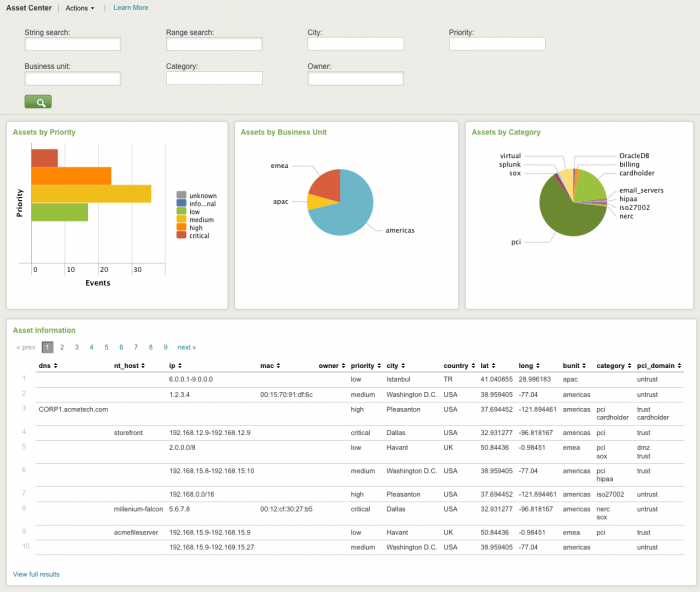
Asset Center
The Asset Center dashboard provides a way to review and search the asset list and activities associated with those assets.
Relevant data sources
The Asset Center dashboard uses information from your assets lists as data sources.
How to configure this dashboard
1. Index relevant data sources from a device, application, or system in Splunk.
2. Map the data to the Assets and Identities data model. See the Assets and Identities topic for more information. The Common Information Model fields bunit and category are derived by automatic identity lookup, and do not need to be mapped directly.
Dashboard description
Asset Center dashboard data is derived from the Assets_And_Identities data model and accelerated automatically.
To verify that asset data is present, use this search:
| datamodel Assets_And_Identities All_Assets search
To verify that events are being accelerated by the data model correctly, use this search (be careful not to search across all time):
| tstats summariesonly=true count from datamodel=Assets_And_Identities by user
For more information on distributed namespaces, see "Tscollect" and "Data Model" in the Splunk Search Reference Manual for more information about data models and namespaces.
Useful searches/Troubleshooting
| Troubleshooting Task | Search/Action | Expected Result |
|---|---|---|
| Verify that you have data from your network device(s) | sourcetype=<your_sourcetype_for_your_data> | Returns data from your network device(s). |
| Verify that asset data is indexed in Splunk | | datamodel Assets_And_Identities All_Assets search | Returns all asset data from your device(s) |
| Verify that asset data is normalized to the Common Information Model properly | | datamodel Assets_And_Identities All_Assets search | table identity first last priority | Returns a list of events and the specific asset data fields populated from your device(s) |
Additional Information
For more information about using the Asset Center dashboard, see "Asset Center dashboard" in the Splunk App for Enterprise Security User Manual.
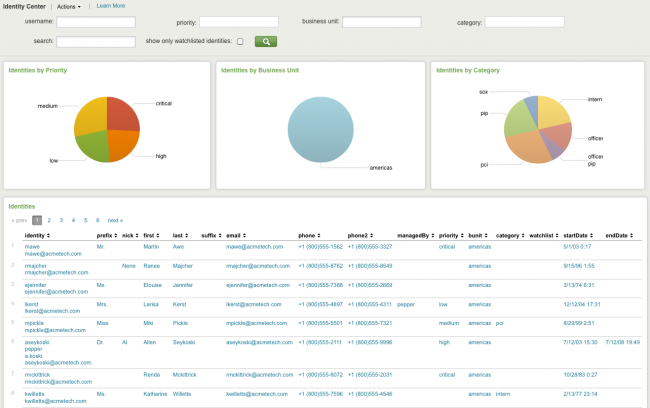
Identity Center
The Identity Center dashboard provides information about all of the identities associated with this instance of the Splunk App for Enterprise Security.
Relevant data sources
The Identity Center dashboard uses information from your identities lists as its data sources.
How to configure this dashboard
1. Index relevant data sources from a device, application, or system in Splunk.
2. Map the data to the Assets and Identities data model. See the Assets and Identities topic for more information. The Common Information Model fields bunit and category are derived by automatic identity lookup, and do not need to be mapped directly.
Dashboard description
Identity Center dashboard data is derived from the Assets_And_Identities data model and accelerated automatically.
To verify that identity data is present, use this search:
| datamodel Assets_And_Identities All_Identities search
To verify that events are being accelerated by the data model correctly, use this search (be careful not to search across all time):
| tstats summariesonly=true count from datamodel=Assets_And_Identities by user
For more information on distributed namespaces, see "Tscollect" and "Data Model" in the Splunk Search Reference Manual for more information about data models and namespaces.
Useful searches/Troubleshooting
| Troubleshooting Task | Search/Action | Expected Result |
|---|---|---|
| Verify that you have data from your network device(s) | sourcetype=<your_sourcetype_for_your_data> | Returns data from your network device(s). |
| Verify that identity information is indexed in Splunk | | datamodel Assets_And_Identities All_Identities search | Returns all identity data from your device(s) |
| Verify that identity data is normalized to the Common Information Model properly | | datamodel Assets_And_Identities All_Identities search |table ip mac owner priority | Returns a list of events and the specific identity data fields populated from your device(s) |
Additional Information
For more information about using the Identity Center dashboard, see "Identity Center dashboard" in the Splunk App for Enterprise Security User Manual.
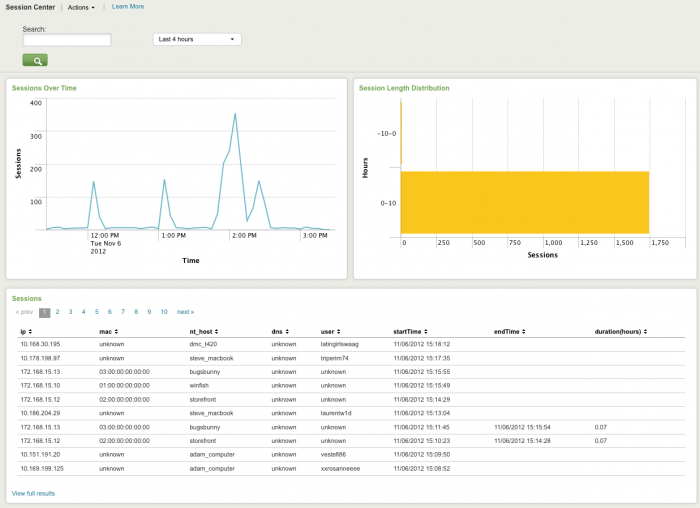
Session Center
The Session Center dashboard provides an overview of network sessions, used to correlate network activity to a user, using session data provided by DHCP or VPN servers, for example.
Relevant data sources
Relevant data sources for the Session Center dashboard include data from DHCP and VPN servers, and information from the asset and identity tables in your deployment.
How to configure this dashboard
1. Index relevant data sources from a device, application, or system in Splunk.
2. Map the data to the Network_Sessions data model. See the Common Information Model Add-on Manual for more information. The Common Information Model fields bunit and category are derived by automatic identity lookup, and do not need to be mapped directly.
3. Tag your data with "network" AND "session"("start" OR "end)".
Dashboard description
Session Center dashboard data is derived from the Network_Sessions data model and accelerated automatically.
To verify that network session data is present, use this search:
| datamodel Network_Sessions All_Session search
To verify that events are being accelerated by the data model correctly, use this search (be careful not to search across all time):
| tstats summariesonly=true count from datamodel=Network_Sessions by user
For more information on distributed namespaces, see "Tscollect" and "Data Model" in the Splunk Search Reference Manual for more information about data models and namespaces.
Useful searches/Troubleshooting
| Troubleshooting Task | Search/Action | Expected Result |
|---|---|---|
| Verify that you have data from your network device(s) | sourcetype=<your_sourcetype_for_your_data> | Returns data from your network device(s). |
| Verify that session data is indexed in Splunk | tag=network (tag=start OR tag=end) or | datamodel Network_Sessions All_Session search |
Returns all data from your device(s) |
| Verify that session data is normalized to the Common Information Model properly | | datamodel Network_Sessions All_Session search |table key ip mac nt_host dns user startTime endTime | Returns a list of events and the specific session data fields populated from your device(s) |
Additional Information
For more information about using the Session Center dashboard, see "Session Center dashboard" in the Splunk App for Enterprise Security User Manual.
| More Network dashboards | Audit dashboards |
This documentation applies to the following versions of Splunk® Enterprise Security: 3.1, 3.1.1, 3.2, 3.2.1, 3.2.2
 Download manual
Download manual
Feedback submitted, thanks!