Configure lists and lookups
To configure or edit the lists or lookup files used with the Splunk Enterprise Security, click Lists and Lookups on the Data Enrichment panel.
Use Lists and Lookups to view and edit the default lists and lookups in Enterprise Security.
Click the name of a list to view or edit it. Click Export to export a copy of the file in CSV format.
Internal lookups
Internal lookups are used by Enterprise Security to generate information to drive dashboards or create notable events.
These lookups are created in three ways:
- Populated by a static lookup table
- Populated internally by search commands
- Populated with information from the Internet
Splunk Enterprise Security is distributed with lookup files containing open-source information from the Internet. These lookups are used by some of the correlation searches that identify hosts that are recognized as malicious or suspicious according to various online sources (such as SANS). When an Internet connection is unavailable, these files will not be updated. If these lists are not updated, the correlation searches that rely on them may not function correctly.
Note: Many of these lookups can now be updated using the lookup editor, so file system access is not necessarily required.
For the list of pre-configured threat intelligence sources, see the topic Threat sources included with ES in this manual.
Lists and lookups editor
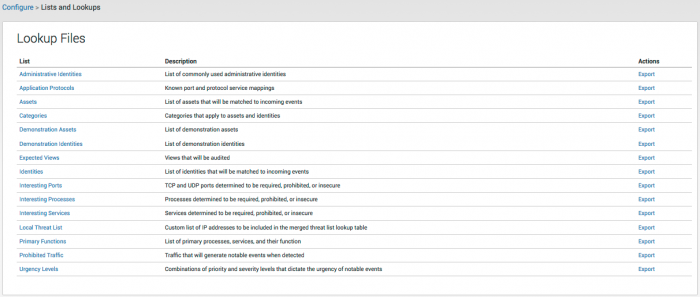
Go to Configure > Lists and Lookups to view the list of current lookup files. Click on a file name to open that lookup file in the lookup editor.
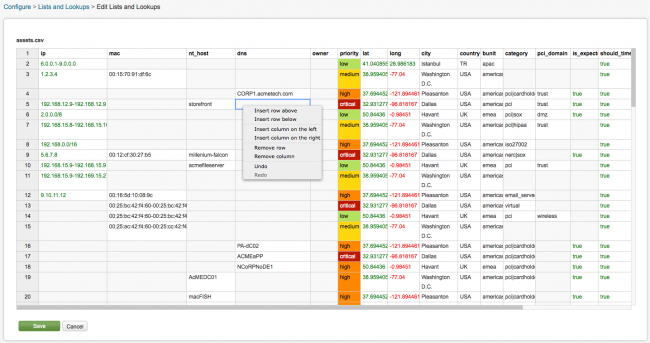
The name of the CSV file is shown in the upper left-hand corner of the panel, assets.csv in this example. The lookup fields are shown at the top of the table, the values for the fields are displayed in the rows below that. Positive numbers are in green, negative numbers are shown in red. The priority values in this file are color-coded. Each CSV file will look slightly different depending on the fields it contains.
Enable lookup edit
To edit a lookup file, you must modify the local.meta file in the app where the lookup file resides.
For instance, to edit expected_views.csv in SA-AuditAndDataProtection ($SPLUNK_HOME/etc/apps/SA-AuditAndDataProtection/metadata/local.meta/), add the following stanza to the local.meta file:
[lookups] access = read : [ * ], write : [ admin,user ]
Edit lookup content
A drop-down, context-sensitive menu is available when you right-click in the lookup table. Use the menu to add columns or rows to the file.
Note: You cannot save a lookup file that contains empty header fields.
- To change a value in a cell, select the cell and type in the new value.
- To add a new value to the file, right-click on the table and select Insert a row... from the drop-down options.
Click Save when you are done. Cancel returns you to the list of lookups.
Note: If you edit a file that does not exist, a warning message alerts you that the file does not exist.
Importing lookup files
An admin may import new CSV files to support new functions and data enrichment in the application.
To do this:
- Go to Settings > Knowledge > Lookups > Lookup table files.
- Click New. Be sure the Destination app is set to SplunkEnterpriseSecuritySuite.
- Browse to the file location and select the file to import.
- Enter a Destination filename to be displayed in the lookup list.
- Click Save.
To be sure that the new information is available to others, change the file permissions from "Private" to "App" or "Global". This moves the CSV file out of the user's folder so that it is be seen by searches, upgrade events, and other users.
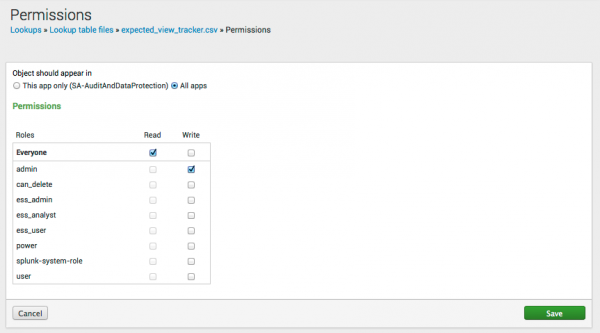
- Click Permissions next to the newly imported CSV file.
- Select the appropriate level and type of permissions for this file. Use permissions to set access to for just this app ("App"), or all apps in this Splunk instance ("Global").
- Click Save.
Verify lookup files
Lookup files must be updated or replaced using the Lists and Lookups editor or directly on the file-system of the search head. After being modified, the lookup list in Splunk will automatically accept the changes (no restart is required).
To import and edit CSV files, see Lists and lookups editor for details.
After editing the file, make sure that the contents can be loaded correctly by using the inputlookup search command to display the list.
inputlookup append=T application_protocol_lookup
Note: The CSV files used as lookups must be created with Unix-style line endings ("\n"). Splunk will not correctly read lookup files saved using Macintosh ("\r") or Windows line endings ("\r\n").
Application Protocols
The Application Protocols list is a list of port/protocol combinations and their approval status in the organization. This list is used to drive the Port & Protocol Tracker dashboard. The Application Protocols list can be found in the following location on the search head:
$SPLUNK_HOME/etc/apps/SA-NetworkProtection/lookups/application_protocols.csv
The following table shows the fields in this file:
| Field | Description |
|---|---|
| dest_port | The destination port number (must be 0-65535) |
| transport | The protocol of the network traffic (icmp, tcp, udp). |
| app | application name |
| status | The approval status of the port (approved, pending, unapproved). By default, the port is considered approved. |
Assets
The Assets lookup contains information about the assets associated with this deployment. This list of assets will be matched to incoming events. See Adding asset data in this manual for information on configuring your asset list.
Categories
A category is logical classification or grouping used for assets and identities. The category list can contain any set of categories you choose for organizing an asset or an identity. Common choices for assets include compliance and security standards such as PCI, or functional categories such as server and web_farm. Common choices for identities include titles and roles. For additional examples, see Asset lookup fields and Identity lookup fields in this manual.
The Categories list is manually updated by default. To access and update the list, browse to Settings > Data Enrichment > Lists and Lookups and select the Asset/Identity Categories list.
A saved search exists that collects all records in the Category field across both assets and identities, update the list, and populate the lookup. To enable the [Identity - Make Categories - Lookup Gen] saved search:
- Select Configure > Content Management.
- Use the search filter to find the Identity - Make Categories - Lookup Gen search.
- Open the search and select the Schedule this search checkbox.
- Adjust the scheduling settings.
- Save the search.
The Categories list is a lookup stored under:
$SPLUNK_HOME/etc/apps/SA-IdentityManagement/lookups
Expected Views
The Expected Views list specifies Enterprise Security views that should be monitored on a regular basis and is used by the View Auditing dashboard (Audit > View Auditing).
The Expected Views list can be found in the following location on the search head:
$SPLUNK_HOME/etc/apps/SA-AuditAndDataProtection/lookups/expected_views.csv
The following table shows the fields in this file:
| Field | Description |
|---|---|
| app | The application that contains the view (SplunkEnterpriseSecuritySuite in this case) |
| is_expected | Either "true" or "false". By default, Enterprise Security assumed activity is not expected so you do not need any entries that include "false". |
| view | The name of the view; this is available in the URL. |
To find the name of a view:
- Navigate to the view in Enterprise Security
- Look at the last segment of the URL to find the view name
For example, the view in the URL below is named incident_review:
Identities
The Identities lookup contains a list of identities that will be matched to incoming events. For information on setting up an identities list, see "Identity Management" in this manual.
Interesting Ports
Interesting Ports contains a list of TCP and UDP ports determined to be required, prohibited, or insecure in your deployment. Solutions administrators should set a policy defining the allowed and disallowed ports.
- Review the Interesting Ports list.
- Edit the list, changing the fields and adding new entries based upon the policy definition.
- Enable the correlation search that will trigger an alert.
Interesting Ports list lookup fields
The list can be found under Configure > Data Enrichment > Lists and Lookups. Choose the Interesting Ports list. In the Lookup editor, the lookup file interesting_ports.csv is displayed. The first line in the file is the header that describes the fields in the file.
| Field | Description | Example |
|---|---|---|
| app | The application or service name | Win32Time |
| dest | The destination host for the network service. Accepts a wildcard. | DARTH*, 10.10.1.100, my_host, etc. Using just a wildcard * will match all hosts.
|
| dest_pci_domain | An optional PCI Domain. Accepts a wildcard. | trust, untrust, etc. |
| dest_port | The destination port number. Accepts a wildcard. | 443, 3389, 5900, etc. |
| transport | The transport protocol. Accepts a wildcard. | tcp or udp |
| is_required | Is the service required to be running? Alert if not present. | true or false |
| is_prohibited | Is the service/traffic/port prohibited from running? Alert if present. | true or false |
| is_secure | Is the service traffic encrypted? | true or false |
| note | A brief description of the service and use-case | Unencrypted telnet services are insecure .. I will look for you, I will find you, and I will kill you. |
Add to, or modify this list using the editor. Click Save when you are done.
- Use a search to review the user and time the lookup file was edited. Example:
index=_internal uri_path="/splunk-es/en-US/app/SplunkEnterpriseSecuritySuite/ess_lookups_edit" - A lookup will not accept regular expressions.
Interesting Processes
Interesting Processes contains a list of processes. This list is used to determine whether a process is required, prohibited, and/or secure. Use the List and Lookup editor to modify or add to this list. The Interesting Processes file can be found in the following location on the search head:
$SPLUNK_HOME/etc/apps/SA-EndpointProtection/lookups/interesting_processes.csv
The following table shows the fields in this file:
| Column | Description |
|---|---|
| app | application name |
| dest | destination of process |
| dest_pci_domain | PCI domain, if available |
| is_required | true or false |
| is_prohibited | true or false |
| is_secure | true or false |
| note | Any additional information about this process |
Interesting Services
Interesting Services contains a list of services in your deployment. This list is used to determine whether a service is required, prohibited, and/or secure. Use the List and Lookup editor to modify or add to this list. The Interesting Services file can be found in the following location on the search head:
$SPLUNK_HOME/etc/apps/SA-EndpointProtection/lookups/interesting_services.csv
The following table shows the fields in this file:
| Column | Description |
|---|---|
| app | application name |
| dest | destination of process |
| dest_pci_domain | PCI domain, if available |
| is_required | true or false |
| is_prohibited | true or false |
| is_secure | true or false |
| note | Any additional information about this process |
Primary Functions
Primary Functions contains a list of primary processes and services, and their function in your deployment. Use this list to designate which services are primary and the port and transport to use. The Primary Functions file can be found in the following location on the search head:
$SPLUNK_HOME/etc/apps/SA-EndpointProtection/lookups/primary_functions.csv
The following table shows the fields in this file:
| Column | Description |
|---|---|
| process | name of process |
| service | name of service |
| dest_pci_domain | PCI domain, if available |
| transport | tcp or udp |
| port | port number |
| is_primary | true or false |
| function | function of this process (for example, Proxy, Authentication, Database, Domain Name Service (DNS), Web, Mail) |
Prohibited Traffic
Prohibited Traffic lists processes that will generate an alert if they are detected. This list is used by the System Center dashboard and is useful for detecting software that has been prohibited by the security policy (such as IRC or data destruction tools) or for software that is known to be malicious (such as malware that was recently implicated in an outbreak).
The Prohibited Traffic file can be found in the following location on the search head:
$SPLUNK_HOME/etc/apps/SA-NetworkProtection/lookups/prohibited_traffic.csv
The following table shows the fields in this file:
| Field | Description |
|---|---|
| app | The name of the process (such as echo, chargen, etc.) |
| is_prohibited | Either "true" or "false" |
| note | A text description of why the process is rejected |
Urgency Levels
Urgency Levels contains the combinations of priority and severity that dictate the urgency of notable events. For more information, see Notable Event Urgency assignment in this manual.
| Content Management | Dashboard Troubleshooting |
This documentation applies to the following versions of Splunk® Enterprise Security: 4.1.0, 4.1.1, 4.1.2, 4.1.3, 4.1.4
 Download manual
Download manual
Feedback submitted, thanks!