My Investigations
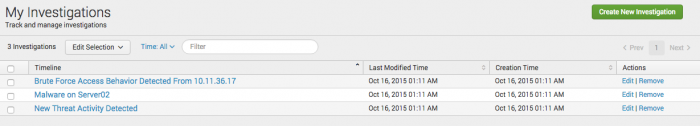
You can track your active investigations on the My Investigations dashboard. View or filter your investigation timelines, or create a new one. You can view all timelines that you create or collaborate on using this dashboard.
Start an investigation
Start an investigation by creating a new investigation timeline from the My Investigations dashboard.
- Click Create New Investigation.
- Add a title to replace the default one, then select the green checkmark to save it.
- Optionally, enter a description and select the green checkmark to save it.
See Investigation Timelines in this manual for more.
Manage your investigation timelines
Manage ongoing investigations from the My Investigations dashboard.
Filter investigations
Quickly locate an investigation timeline or refine the list of timelines using filters.
| Filter by | Description | Action |
|---|---|---|
| Time | Select a time to view only the timelines last modified in the specified time period. | Drop-down. Select to filter by |
| Title | Type a value from the title of a timeline in the text box to view only matching timelines. | Text field. Empty by default. Filters as you type. |
Delete investigations
You can delete individual or several timelines on the My Investigations dashboard. Once a timeline is deleted, it cannot be restored. Assess the audit or research value of a timeline before deleting it.
Delete an individual timeline from the Actions column.
- Click Remove.
- Confirm deletion of the timeline by clicking Remove.
Delete multiple timelines using the Edit Selection menu.
- Select the checkbox next to the timelines you wish to delete.
- Click Edit Selection, then select Delete.
- Confirm deletion of the timeline by clicking Remove.
Edit investigations
Open an investigation timeline to make changes.
- Locate the timeline you want to edit on the My Investigations dashboard.
- Click Edit in the Actions column to open the timeline.
See Investigation Timelines in this manual.
Data sources for investigations
Splunk Enterprise Security stores investigation information in several KVStore collections. The investigations on the My Investigations dashboard, investigation timeline entries, and the action history items that you can add to a timeline each have their own collection. See My Investigations in the Dashboard requirements matrix in this manual for details.
Add _lookup to the end of a KVStore collection to search it using the inputlookup command. For example:
| inputlookup append=t action_history_lookup
Access to timelines
Users with the ess_admin role can create and view investigations by default. To allow other users to create or edit a timeline, add the `edit_timeline` capability. See Configure users and and roles in the Installation and Upgrade Manual.
After an investigation timeline is created, only the owner of and collaborators added to that timeline can view and edit it. However, a user with the ess_analyst role can view timeline information for any investigation by querying the relevant KV Store collection using inputlookup.
Action history data sources
Action history items do not show up instantly. Five saved searches create action history items. View them by navigating to Configure > Content Management and using the filters. If you modify these saved searches, action history items could stop appearing in your action history.
- "Dashboard Views - Action History”
- "Search Tracking - Action History”
- "Per-Panel Filtering - Action History”
- "Notable Suppression - Action History”
- "Notable Status - Action History”
If you want to exclude a search that you perform from your action history, use the Action History Search Tracking Whitelist lookup. See Configure lists and lookups for more about lookups.
| Investigation Timelines | Investigation Bar |
This documentation applies to the following versions of Splunk® Enterprise Security: 4.1.0, 4.1.1, 4.1.2, 4.1.3, 4.1.4, 4.2.0 Cloud only, 4.2.1 Cloud only, 4.2.2 Cloud only
 Download manual
Download manual
Feedback submitted, thanks!