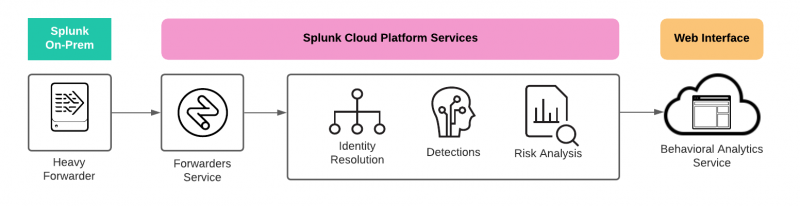
Data flow overview for behavioral analytics service
The following image summarizes how data gets into behavioral analytics service and is eventually viewed in the behavioral analytics service web interface. Each component in the flow is described in the table immediately following the image.
| Component | Description |
|---|---|
| Heavy Forwarder | The heavy forwarder sends each raw event to the following:
See Get data into behavioral analytics service for instructions. Do not modify or edit any of the Splunk SPS pipelines provisioned for behavioral analytics service. |
| Forwarders Service | The Forwarders service in Splunk Cloud Platform aggregates, formats, and routes data in real-time from the heavy forwarder to Splunk Mission Control. |
| Identity Resolution | Behavioral analytics service performs identity resolution to associate each event with an originating device or user. See How behavioral analytics service performs identity resolution to associate data with entities. |
| Detections | Behavioral analytics service generates detections based on the data in the system. See Supported detections in behavioral analytics service for a complete list of supported detections. |
| Risk Analysis | Anomalies are assigned a score, and algorithms are further applied until a normalized risk score is generated for each entity. See How behavioral analytics service calculates risk scores. |
| Behavioral Analytics Service Web Interface |
|
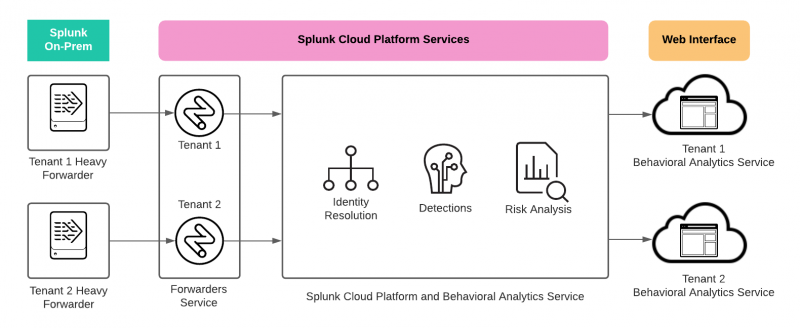
In multi-tenant environments, onboarded data from each tenant is tagged with its own unique tenant ID, then enriched and parsed by Splunk Cloud Platform and behavioral analytics service. Then, entities and detections are sent to their respective tenants and can be viewed in the behavioral analytics service web interface.
The following image summarizes the data flow in a multi-tenant environment:
| Send findings for risk analysis using the Finding Report schema | Perform identity resolution to associate data with entities in behavioral analytics service |
This documentation applies to the following versions of Splunk® Enterprise Security: 7.0.1, 7.0.2
 Download manual
Download manual
Feedback submitted, thanks!