Use Analytic Stories for actionable guidance in
The Splunk Security Research team writes Analytic Stories that provide actionable guidance for detecting, analyzing, and addressing security threats. An Analytic Story contains the searches you need to implement the story in your own environment. It also provides an explanation of what the search achieves and how to convert a search into adaptive response actions, where appropriate.
By default, the ess_admin and ess_analyst roles can configure the use case library with relevant Analytic Stories. See Manage Analytic Stories through the use case library in Splunk Enterprise Security in the Administer Splunk Enterprise Security manual.
Determine which Analytic Stories to use
You can use common industry use cases to determine which Analytic Stories and searches are useful to you. There are a variety of ways to determine if an Analytic Story contains the searches you need:
- by industry use case
- by framework
- by data
In the following scenario, you know that you're interested in common AWS-related security issues, so you start by filtering on known use cases for cloud security.
- From the Splunk ES menu bar, select Configure > Content > Use Case Library.
- From the use cases filters on the left, click Cloud Security.
- From an Analytic Story, such as Suspicious AWS EC2 Activities, click the greater than ( >) symbol to expand the display.
- You see the detection searches that are related to this use case.
- You also see your data sources, data models, and lookups that these searches use.
Data Sources Description Recommended Data Sources The type of data sources that are likely to provide valuable data. Sourcetypes Your sourcetypes that are in use by the detection searches for this Analytic Story. If the status icon shows a red exclamation mark, hover over the icon to see the reason. Data Models Your data that is in use by the detection searches for this Analytic Story as mapped to the Splunk data models via the CIM add-on. If the status icon shows a red exclamation mark, hover over the icon to see the reason. Lookups Your lookups that are in use by the detection searches for this Analytic Story. If the status icon shows a red exclamation mark, hover over the icon to see the reason.
You can use an Analytic Story if the recommended data sources, sourcetypes, data models, and lookups do not have red exclamation marks. However, even though green checkmarks indicate that sources are available, they don't always mean that the searches return results based on the ingested data.
Use Analytic Stories to search for results and get guidance
In the following scenario, you know that you're interested in EC2 instances that originate from unusual locations or those launched by previously unseen users, so you start by filtering on known use cases for cloud security.
- From the Splunk ES menu bar, select Configure > Content > Use Case Library.
- From the use cases filters on the left, click Cloud Security.
- Click the name of the Analytic Story. In this case, click Suspicious AWS EC2 Activities.
The Analytic Story Details page opens for the story. - From the References section, see any links, white papers, or PDFs provided.
- From the Detection section, select a search, such as ESCU - EC2 Instance Started In Previously Unseen Region.
- From the Search section, click the greater than (>) symbol to expand the display.
- Revise the time picker and click Search to manually run the search and see the results.
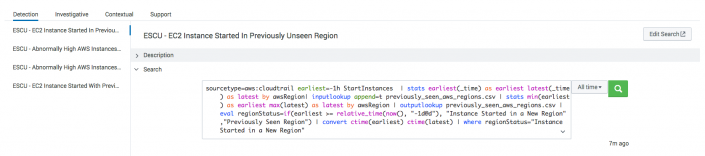
- From the Known False Positives section, click the greater than (>) symbol to expand the display for tips on when the results might not indicate a problem.
By default, the ess_admin and ess_analyst roles can enable and schedule to run this search automatically on a regular basis. See Enable and schedule the Analytic Story in the Administer Splunk Enterprise Security manual.
Bookmark the Analytic Story
Bookmarks persist per user, so you can bookmark the Analytic Stories that are specific to your duties.
- From the Splunk ES menu bar, select Configure > Content > Use Case Library.
- Find the name of the Analytic Story.
- Toggle the Bookmark switch to enable it.
- From the drop-down filters, select Bookmarked > True to find your bookmarked stories.
| Review the summary of an investigation in Splunk Enterprise Security | Analyze risk in Splunk Enterprise Security |
This documentation applies to the following versions of Splunk® Enterprise Security: 7.0.1, 7.0.2, 7.1.0, 7.1.1, 7.1.2, 7.2.0, 7.3.0, 7.3.1, 7.3.2, 7.3.3
 Download manual
Download manual
Feedback submitted, thanks!