Introduction to behavioral analytics service
Behavioral analytics service is a cloud-native user and entity behavioral analytics (UEBA) solution that helps investigative analysts uncover hidden threats. Behavioral analytics service is provisioned on a tenant in Splunk Mission Control. See How do I get behavioral analytics service?
Behavioral analytics service is available on Splunk Cloud Platform in the US East (Virginia) AWS region only.
Behavioral analytics service brings UEBA capabilities to the Splunk Cloud Platform environment. Behavioral analytics service provides comprehensive security visibility to uncover hidden and unknown threats that cannot be easily detected through searches. See How does behavioral analytics service enhance your Splunk SIEM environment?
How does behavioral analytics service enhance your Splunk SIEM environment?
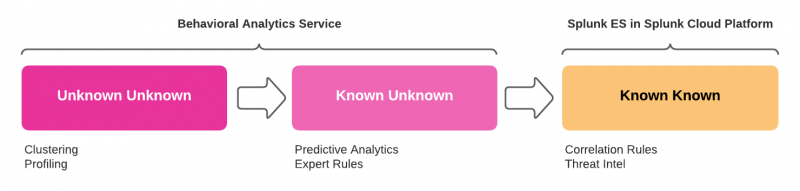
The following image shows how behavioral analytics service can enhance and extend threat hunting in your existing Splunk SIEM environment:
| Phase | Description |
|---|---|
| Unknown Unknown | There are unknown threats in your environment, and the nature of the threats is also unknown. Behavioral analytics service uses the following processes to help uncover hidden threats:
|
| Known Unknown | Once threats are identified, behavioral analytics service uses the following procedures to further analyze behavioral information and understand the nature of the threat:
|
| Known Known | Use your existing Splunk SIEM to detect known threats.
|
What do I need to run behavioral analytics service?
Verify that you have the following in order to run behavioral analytics service:
- Splunk Connect for Mission Control (SC4MC) 2.0.1. See Install and configure Splunk Connect for Mission Control.
- Splunk Cloud stack on 8.2104.1 or later in the US East (Virginia) region
- Splunk Enterprise Security (ES) 6.1 or later
Behavioral analytics service is not available in the following compliant environments:
- FedRAMP Moderate
- IL5
- IRAP
How do I get behavioral analytics service?
In order to get access to behavioral analytics service, you need the following products or services:
| Product or service | Required? | Description |
|---|---|---|
| An on-premises heavy forwarder | Required | The heavy forwarder receives data from on-premises assets and forwards the data to Splunk Mission Control. See Get data into behavioral analytics service for information about how to configure the heavy forwarder. |
| Access to Splunk Mission Control | Required | Behavioral analytics service is provisioned on a tenant in Splunk Mission Control.
After you are invited to a behavioral analytics service tenant, you must register as a new user before you log in. On the login screen, click register to create a new Splunk Cloud Services account before you log in to your behavioral analytics service tenant. |
| Splunk Enterprise Security | Required | Behavioral analytics service ingests asset and identity data from Splunk Enterprise Security (ES) in Splunk Cloud Platform for optimal identity resolution. See How to import assets and identities data from Splunk ES on Splunk Cloud Platform into behavioral analytics service. |
| What's new in behavioral analytics service |
This documentation applies to the following versions of Splunk® Enterprise Security: 7.0.1, 7.0.2
 Download manual
Download manual
Feedback submitted, thanks!