Examine the riskiest entities and anomalies in the Entity Analytics Dashboard
Access the Entity Analytics dashboard to see a summary of the riskiest entities and anomalies by risk score. See How behavioral analytics service calculates risk scores for details about risk scores are calculated in behavioral analytics service.
To access the Entity Analytics dashboard, select Dashboards > Entity Analytics from Splunk Mission Control.
- (Optional) Click on the full screen (
 ) icon to enter full screen mode for the dashboard.
) icon to enter full screen mode for the dashboard. - (Optional) Click the share (
 ) icon to copy the URL of the dashboard, which can then be shared with colleagues.
) icon to copy the URL of the dashboard, which can then be shared with colleagues. - (Optional) Click the more (
 ) icon to see additional options for the dashboard, such as duplicate, export, or set the dashboard as your home page.
) icon to see additional options for the dashboard, such as duplicate, export, or set the dashboard as your home page.
View details about a specific entity
Click on any user or device to view the details for that entity.
- Click on the entity to open the entity details in the same browser tab.
- Use command + click on MacOS or Ctrl + click on Windows to open the entity details in a new tab.
See Drill down to view entity details in behavioral analytics service.
Adjust the compute window and look-back duration
Adjust the Compute Window and Look-Back Duration to filter the data displayed in the dashboard:
- (Optional) Adjust the compute window to view entity scores over the past 24 hours or past 7 days (back to 07:00:00 UTC on the seventh day).
- (Optional) Adjust the look-back duration to adjust the anomaly summary information in the dashboard.
- Click Submit for your selections to take effect.
The table below summarizes which panels will change based on your selections:
| Panel | Affected By |
|---|---|
| Riskiest Users | Compute Window. The user risk scores are computed and normalized based on the selected compute window. |
| Riskiest Devices | Compute Windows. The device risk scores are computed and normalized based on the selected compute window. |
| Anomaly Risk Level | Look-Back Duration. The summary of top anomaly types and severities depends on how far back in time you look. |
| Anomaly Type by Volume | Look-Back Duration. The most frequently occurring anomalies vary depending on how far back in time you look. |
| Trending | Neither. See Examine the riskiest entities for more information about how data is presented in the Trending panel. |
| Riskiest Entities | Both Compute Window and Look-Back Duration. First, the top 8 riskiest entities are identified based on the compute window, and then anomaly activity over the selected look-back duration is provided. |
| Riskiest Anomalies | Look-Back Duration. The riskiest anomalies vary depending on how far back in time you look. |
Examine the riskiest entities
Use the Riskiest Users and Riskiest Devices to begin examining the users and devices with the highest risk score. Click Next or click on a page number in the navigation bar to view more entities.
See the 50 entities with the largest increase in risk score in the last 24 hours in the Trending panel.
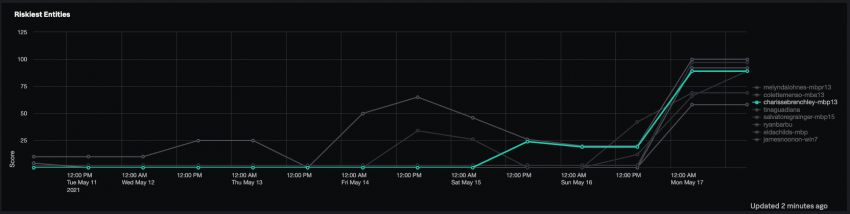
Use the Riskiest Entities panel to view a summary of the top riskiest users or devices over time. Hover over the name of a user or device to isolate that entity's graph and examine the risk trend over time. The following example shows a steady increase in risk score for the device charissebrenchley-mbp13 between 12:00 AM on May 15 to 12:00 AM on May 17.
View a summary of the anomalies in your system
View a summary of the anomalies in your system in the Anomaly Risk Level panel. The concentric rings provide the following anomaly information over the selected look-back duration:
- The inner ring and anomaly key break down the number of anomalies per severity. You can determine if you have a large number of anomalies in a particular severity, such as high or critical.
- The outer ring shows the distribution of anomalies by severity and by type. For example, you may have a large number of high severity anomalies, and you can see the breakdown of anomaly types that have a high severity. A maximum of 10 types of anomalies are shown per severity. Additional anomaly types beyond the tenth type are grouped in a category called Other.
You can view which anomaly types are most frequently found in your environment over the past 7 days in the Anomaly Type by Volume panel. Hover over any bar in the graph to see the name of the anomaly, and the number of such anomalies in your system.
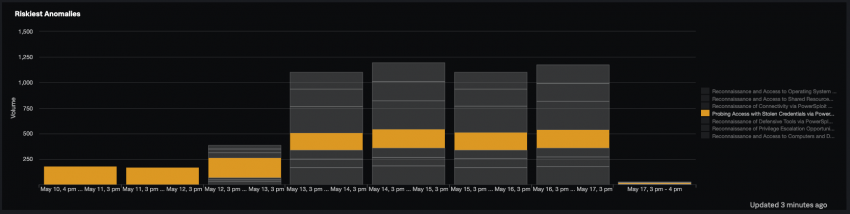
The Riskiest Anomalies panel shows a summary of the top anomaly types by volume over time. Hover over the name of an anomaly to isolate that anomaly's graph and examine the trend over time. The following example shows Probing Access with Stolen Credentials via Powersploit Modules anomaly highlighted. There is a consistent occurrence of this anomaly from May 10 to May 17.
| Create a notable to investigate in Splunk Mission Control | View behavioral analytics service detections and details |
This documentation applies to the following versions of Splunk® Enterprise Security: 7.0.1, 7.0.2
 Download manual
Download manual
Feedback submitted, thanks!