Triage notables on Incident Review in Splunk Enterprise Security
Triage notable by drilling down on specific notables or groups of notables that pose the highest threat. Triaging notables helps to respond to security threats faster during an investigation. You can also monitor specific notables, assign notables to specific owners for review, and prioritize actions that analysts take to resolve security events on the Incident Review page.
Triage notables faster using the following options available on the Incident Review page:
- Sort notables for triage during an investigation
- Filter notables for triage during an investigation
- Include or exclude suppressed notables in dashboard metrics
- Add dispositions to notables
- Manage saved views
- Assign notables to owners
- Update the status of a notable
- Prioritize notables by urgency
- Analyze risk notables
Sort notables for triage during an investigation
Sort notables on the Incident Review page to accelerate the triage process. Sorting notables helps to group similar notables together. Select the down arrow next to the field column heading of the notable and then, select A to Z or Z to A to sort the column in ascending or descending order.
You can sort notables by the following fields:
- Risk Object
- Risk Score
- Risk Events
- Risk Object Type
- Time
- Disposition
- Security Domain
- Urgency
- Status
- Owner
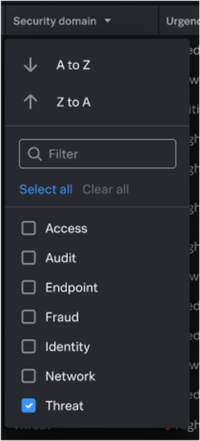
Filter notables for triage during an investigation
Filter notables to drill down on specific and detailed information about the notables so that you can categorize, track, and assign notables to analysts based on specific criteria and identify potential threats faster. For example, the ability to filter notables using dispositions removes the need to review unrelated dispositions and prevents dispositions from being duplicated.
The following screenshot shows how you can use the down arrow key next to the notable field column headings on the Incident Review page to display the available filters.
Select the filters that you want to use to filter the notables. Alternatively, you can enter a specific filter criterion and add it to the list. For example, you can add the short ID, labels, and corresponding fields in the Incident Review settings to filter notables.
You can filter notables using the following fields:
| Field | Description |
|---|---|
| Urgency | Importance of the notable event, such as, Medium, Low, High, Critical, Informational, and Unknown |
| Status | Status of the notable, such as, New, In-progress, Pending, Resolved, and Closed |
| Owner | Name of the owner. |
| Security Domain | Domain from which the notable is generated, such as, Access, Endpoint, Network, Threat, Identity, and Audit |
| Type | Option to select all notables or specific notables based on risk events Options include: All Notables, Notables (that don't use risk based alerting), and Risk Notables |
| Search type | Correlation search or sequenced search You can also filter notables using specific correlation searches |
| Time | Time span during which notables are created, such as Last 24 hours, Last 30 days, and so on. |
| Disposition | Threat level associated with the notable such as False Positive - Incorrect Analytic Logic or *'False Positive - Inaccurate Data |
| Short ID | Enterprise Security creates a short ID as a unique identifier for the notable. |
You can also customize the fields or add additional fields to display your notable events. For more information on customizing notable event fields, see Change notable event fields.
If you want to see a filtered view of Incident Review by default, ask your ES admin to modify the navigation menu in Enterprise Security to link directly to a filtered view. See Add a link to a filtered view of Incident Review in Administer Splunk Enterprise Security.
Toggle Show Charts or Hide Charts to display visualizations for the notable events based on Urgency, Status, Owner, and Domain.
Include or exclude suppressed notables in dashboard metrics
Exclude suppressed notables in the metrics displayed on the Executive dashboard and the SOC Operations dashboard so that you can triage notables faster during an investigation. You also have the option to include notables in the metrics on the Executive dashboard and the SOC Operations dashboard if you want to verify whether some notables were overlooked.
Follow these steps to include suppressed notables:
- On the Splunk Enterprise Security app, go to Security Posture.
- Select Executive Summary dashboard or SOC Operations dashboard.
- Turn on Include suppressed notables to add suppressed notables on the dashboard metrics.
By default, '''Include suppressed notables''' is turned off.
For more information on the Executive Summary dashboard, see Executive Summary dashboard.
For more information on the SOC Operations dashboard, see SOC Operations dashboard.
Add dispositions to notables
Add a disposition to any notable on the Incident Review page to identify the threat level associated with the notable accurately and accelerate the triage process. Adding dispositions helps to classify the notables and separate the false positives without impacting the status of the notable event, such as New, In-progress, Closed, and so on.
- From the Splunk Enterprise Security menu bar, click the Incident Review page.
- Scroll down to the table that lists the notables.
- Select the notable to which you want to add a disposition.
- Click Edit Selected to edit the selected notable event.
- Select one of the following options from the Disposition drop down menu:
- Undetermined
- True Positive - Suspicious Activity
- Benign Positive - Suspicious But Expected
- False Positive - Incorrect Analytic Logic
- False Positive - Inaccurate Data
- Click Save Changes.
Add custom dispositions to a notable
Follow these steps to create a custom disposition for notables:
- From the Splunk Enterprise Security menu bar, select Configure>Incident Management>Incident Review Settings.
- Scroll down to Incident Review-Dispositions.
- Click New.
- In the New Disposition dialog, add a label and description for the new disposition.
- Click Save.
Follow these steps to add the custom disposition to any notable:
- From the Splunk Enterprise Security menu bar, click the Incident Review page.
- From the list of notables, select the notables to which you want to add the custom disposition.
- Click Edit Selected.
- In the Edit Events dialog, select the custom disposition from the drop down menu.
- Click Save Changes.
- Click Close.
Configure that dispositions are required to close a notable
As a security administrator, you can configure Splunk Enterprise Security so that notable status cannot be closed without adding a disposition so that no notables are overlooked during an investigation and each notable has a priority value associated with it.
Follow these steps to ensure that notable status is not closed without adding a disposition:
- In the Splunk Enterprise Security app, go to Configure.
- Select Incident Management, then select Incident Review Settings.
- Go to Incident Review - Dispositions.
- Turn on the Required button if you want that an analyst must add a disposition when selecting an end status type such as Resolved or Closed for a notable.
- Select Save.
Add a disposition to close a notable
When attempting to close a notable, you might see errors when you try to change the status of a notable.
If the disposition is marked as required in the '''Incident Review Settings''', you cannot make any updates to the notable event without adding a disposition.
Adding a disposition ensures that no notables are overlooked during an investigation and each notable has a priority value associated with it. For more information on adding dispositions, see Add a disposition to a notable.
Follow these steps to add a disposition and close a notable:
- In the Splunk Enterprise Security app, go to Incident Review.
- Select the notable to which you want to add a disposition so that it can be closed.
- Click Edit Selected to edit the notable.
- Add a disposition other than Undetermined to close the notable.
- Select Save Changes.
Manage saved views to view notables
Create saved views of filtered notables to accelerate the triage process during an investigation workflow. Saved views allows analysts the choice to set up views based on what notables they want to see. Managing saved views, sharing saved views, and switching between saved views helps to share responsibilities and triage notables faster during an investigation.
Viewing options for notable triage during an investigation
Splunk Enterprise Security offers the following viewing options:
- Default global configuration: Displays the same views of filtered notables for each user in Splunk Enterprise Security
- Default saved view: Allows the administrator to create a default saved view for all users
- Administrator specified saved view: Allows the administrator to create customized saved views for specific users as their default
- Saved views: Allows a user to create customized saved views and manage those saved views
Viewing notables using the default global configuration requires no action since this setting is the default configuration for Splunk Enterprise Security. Filters in this view applies to all users.
Manage saved views
As an administrator or an analyst, you can manage saved views to focus on specific types of threats such as fraud anomaly or endpoint attacks and improve your triaging capabilities. In addition to saving views, you can share views with other users to make the triage process easier during an investigation. You can also edit, delete, and switch between saved views.
Follow these steps to manage saved views:
- From the Splunk Enterprise Security menu bar, select the Incident Review page.
- Select Manage Saved Views from the Saved Views drop down menu to view all the available saved views.
- Select the saved view that you want to apply to the Incident Review page in Splunk Enterprise Security. You can also switch between saved views.
- In the Manage Saved Views dialog, select the pencil icon next to the saved view that you want to edit.
- Select the trash icon to delete a saved view.
For information on creating or sharing views, see Create and manage views in Splunk Enterprise Security in the Splunk Enterprise Security Admin manual.
Select an administrator specified view to view notables
As a Splunk Enterprise Security administrator, you can save a specific view for analysts and identify that saved view as their default view. This administrator selected view is in addition to a default saved view, which is a global view and is universal for all analysts. The administrator selected view can also be shared between multiple analysts.
Follow these steps to select the administrator specified view:
- In the Splunk Enterprise Security app, go to the Incident Review page.
- Go to Saved Views and select the Admin Selected Saved View.
Alternatively, you can follow these steps to select the administrator specified view:
- In the Splunk Enterprise Security app, go to Configure.
- Select Incident Review Management, then select Incident Review Settings.
- In Incident review Settings, go to Incident review - Admin Selected View.
- Select the specific admin selected saved view form the dropdown.
Assign notables to owners
You can assign one event at a time or several at once.
- Select a notable.
- Click Edit selected.
- Select an Owner to assign the notable. Or, click Assign to me to assign the event or events to yourself.
- Save your changes.
Owners are unassigned by default, and you can assign notables to any user with an administrator, ess_admin, or ess_analyst role. For more on user roles, see Configure users and roles in the Installation and Upgrade Manual.
If you use SAML authentication, it might take up to 10 minutes to update the list of users that you can assign notables to.
Update the status of a notable
New notables have the New status. As analysts triage and move a notable through the incident review workflow, the owner of the investigation can update the status of the notable to reflect the actions they take to address the event.
- Select one or more events, then click Edit all selected. To take action on all displayed events, click Edit all ## matching events.
- In the Edit Events window, update the fields to reflect your actions.
- (Optional) Add a Comment to describe the actions you took.
- Save changes.
If your Enterprise Security (ES) administrator customized the Incident Review page, you might need to enter comments when updating a notable. See Customize Incident Review in Splunk Enterprise Security for more information about how ES admins can customize the ways that analysts view and interact with notables.
If your changes are not immediately visible, check the filters. For example, if the filter is set to "New" after you changed an event to "In Progress", your updated event will not display.
You can choose from the following notable statuses.
| Status | Description |
|---|---|
| Unassigned | Used by Enterprise Security when an error prevents the notable from having a valid status assignment. |
| New | Default status. The event has not been reviewed. |
| In Progress | An owner is investigating the event. |
| Pending | The assignee must take an action. |
| Resolved | The owner has addressed the cause of the event and is waiting for verification. |
| Closed | The resolution of the event has been verified. |
You can customize the notable status names and workflow progression to match your process. For more information, see Manage notable statuses.
Prioritize notables by urgency
Use the urgency level of a notable event to prioritize incident review. Every notable is assigned an urgency. Urgency levels can be Unknown, Low, Medium, Informational, High, or Critical.
Enterprise Security calculates the urgency level using the severity of the correlation search event and the priority of the asset or identity involved in the event. See How urgency is assigned to notable events in Splunk Enterprise Security.
By default, security analysts can change the urgency of a notable. See Customize Incident Review in Splunk Enterprise Security to learn how to change the default value for urgency of a notable.
Analyze risk notables to identify threat
Use the Incident Review page to investigate the contributing risk events that created a notable. You can quickly identify the risk events that might be a threat to your security environment by analyzing the timeline of the risk events with their associated risk score.
- From the Splunk Enterprise Security menu bar, click the Incident Review page.
- From the Type filter dropdown, select Risk Notable to display the notables that have associated risk events.
You can expand the notable on the Incident Review page to launch the risk event timeline and further investigate the risk events associated with the notable. - Review the following two fields for the risk notables:
Field Description Risk Events Events that created the notable alert Aggregated Risk Score Sum of all the scores associated with each of the contributing risk events
For example, if there are five risk events and each risk event is assigned a score of 10, 20, 30, 40, and 50 respectively, then the aggregated risk score is 150. - Click the value in the Risk Events field for the notable that you want to investigate.
This opens a window that contains two panels. The top panel displays a timeline visualization of the contributing risk events that created the notable. The bottom panel includes a table with detailed information on the contributing risk events. - Sort the contributing risk events in the table based on any of the following fields:
- Time
- Risk Rule
- Risk Score
- Expand the risk notable in the Contributing Risk Events table for more details to further analyze the risk objects in your security environment.
This includes information on the following fields:- Risk Object
- Source
- Risk Score
- Risk Message
- Saved Search Description
- Threat Object
- Threat Object Type
- Click View Contributing Events for information on the contributing events that triggered the risk event.
You can also search for specific contributing risk events that created the notables through the filter. - Correlate the risk events with dates and severity of the risk scores in the timeline visualization to identify threats.
You can zoom in and out to narrow down the time of occurrence since the timeline visualization plots of the contributing risk events using time on the x-axis and the risk score on the y-axis.
The timeline visualization also uses color codes on the icons that indicate the severity of the risk scores. The color coding of risk score icons is consistent across the Contributing Risk Events table and the timeline visualization of the risk events. A lighter color icon corresponds to a lower risk score.
You can view a maximum of 100 risk events on the Contributing Risk Events table and the timeline visualization. If you have more than 100 risk events, the event count displays as100+on the header and includes a link to the search page that displays the complete list of risk events. If the number of risk events is less than 100, the event count is displayed as is.
The risk score in the Contributing Risk Events table and the timeline visualization is the calculated risk score of all events. - Hover over the color coded icons in the timeline visualization to view more information on the risk event within a tooltip.
The following additional details about the risk event are displayed in the tooltip:
- Risk Score
- Event Name
- Description
- Time
- MITRE Tactic
- MITRE Technique
- Click a notable on the timeline to highlight the associated row in the Contributing Risk Events table.
- Identify the risk object type through the icons displayed in the header of the timeline visualization from the following icons:
- User
- System
- Network Artifacts
- Other
You might see a small discrepancy between the event count on the Incident Review page and the event count on the risk window because a new search is launched when you click the notable on the Incident Review page.
Use custom risk notables to identify threats
Use the timeline visualizations for custom risk notables to search the risk index and identify threats. You can use custom risk notables in addition to using default risk notables to identify threats that are specific to your security environment. Following are examples of the default risk notables that are packaged with Splunk Enterprise Security:
24 hour risk thresholdATT&CK Tactic Threshold Exceeded over previous 7 days
The risk timeline modal cannot be selected unless all required fields are present within the risk notable event and the contributing risk events.
To create a custom risk notable, define the following fields in your risk notable. The following fields are common to the risk index and risk data model:
| Field | Description |
|---|---|
risk_object
|
The risk event identifier |
risk_object_type
|
The risk event identifier type |
risk_score
|
A number that represents the risk level of a specific risk object. |
risk_event_count
|
The total number of risk events associated with the notable event. This value is calculated using the notable search. |
drilldown_earliest
|
The start time used to identify the contributing events for the risk notable. This value is automatically populated using the info_min_time in the notable framework.
|
drilldown_latest
|
The end time used to identify the contributing events for the risk notable. This value is automatically populated using the info_max_time in the notable framework.
|
drilldown_search
|
The search used to identify the contributing events for the risk notable. This SPL must return a calculated_risk_score field with a non-null value. The calculated_risk_score field is common to the Risk data model.
|
Example: How to create custom risk notables
Following is an example of creating a risk notable. You must follow this format to use the Risk Timeline visualization.
Say, you have the following events in the Risk data model:
| Risk object | Risk object type | Risk score |
|---|---|---|
| foo | user | 30 |
| bar | user | 50 |
| foo | user | 30 |
The underlying notable search must contain the following required fields:
risk_objectrisk_object_typerisk_scorerisk_event_countdrilldown_earliestdrilldown_latestdrilldown_search
Following is an example of the search for the risk notables with associated results:
Required fields that are not part of the Risk data model are calculated.
| tstats `summariesonly` sum(All_Risk.calculated_risk_score) as risk_score, count(All_Risk.calculated_risk_score) as risk_event_count from datamodel=Risk.All_Risk by All_Risk.risk_object, All_Risk.risk_object_type
Results:
| Risk object | Risk object type | Risk score | Risk event count |
|---|---|---|---|
| foo | user | 60 | 2 |
| bar | user | 50 | 1 |
Though search results add the drilldown fields automatically, you must specify a drilldown_search when you configure the risk notable on the Correlation Search editor. Additionally, the notable drilldown_search must contain the field calculated_risk_score.
Following is an example of the drilldown_search:
| from datamodel:"Risk.All_Risk" | search risk_object="$risk_object$" risk_object_type="$risk_object_type$"
As shown in this example, the calculated_risk_score already exists in the Risk data model and is calculated automatically.
For more information on accessing the Risk Timeline visualization to analyze risk event notables and identify threat, see Analyze risk event notables to identify threat.
| Overview of Incident Review in | Investigate a notable on Incident Review in Splunk Enterprise Security |
This documentation applies to the following versions of Splunk® Enterprise Security: 7.3.0, 7.3.1, 7.3.2, 7.3.3
 Download manual
Download manual
Feedback submitted, thanks!