Use risk based alerting instead of sequence templates to detect threats
Risk based alerting (RBA) provides more contextual information than sequence templates. Use RBA instead of sequence templates to detect sequences of threats from Splunk Enterprise Security version 8.x and higher.
Sequence templates are deprecated from Splunk Enterprise Security versions 8.0 and higher. However, sequence templates are available with read-only access in Splunk Enterprise Security version 8.1 and higher for manual transition.
Use SPL searches to get similar functionality as sequence templates and perform the following tasks:
- Detect a chain of behaviors by organizing events in a specific order
- Run multiple detections in a specific order
Detect a chain of behaviors and generate events in a specific order
The following is an example of an SPL search that helps to detect a chain of behaviors by ensuring events are in a specific order.
index=risk search_name="Search1" OR search_name="Search2"
| sort by user _time | dedup _time search_name user
| delta _time as gap
| autoregress search_name as prev_search
| autoregress user as prev_user
| where user = prev_user
| table _time gap src user search_name prev_search
| where search_name!=prev_search AND gap<600)
Following is a walkthrough of how you can build searches using SPL to detect a chain of behaviors in your security environment:
- The following SPL identifies two potential reconnaissance activities
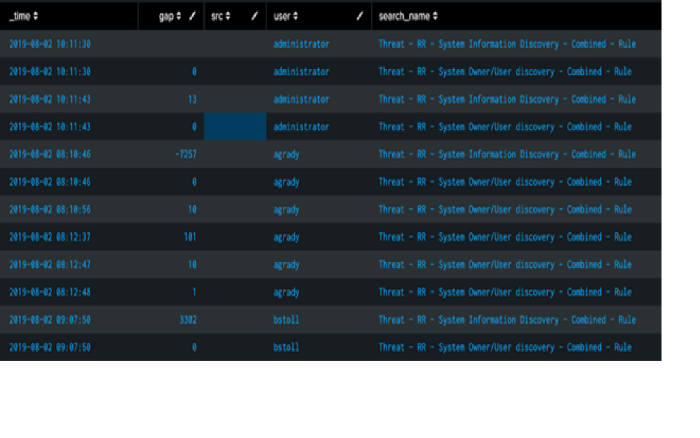
"Threat - RR - System Owner/User discovery - Combined - Rule"and"Threat - RR - System Information Discovery - Combined - Rule"that are trying to gain information from the environment.index=risk sourcetype=stash search_name IN ("Threat - RR - System Owner/User discovery - Combined - Rule","Threat - RR - System Information Discovery - Combined - Rule") | sort by user _time | dedup _time search_name user | delta _time as gap | table _time gap src user search_nameThe following screenshot displays the output of the SPL search sorted by user and time:
When a new user appears on the following row, a significant gap is displayed between the two events, such as -7257 or 3302.
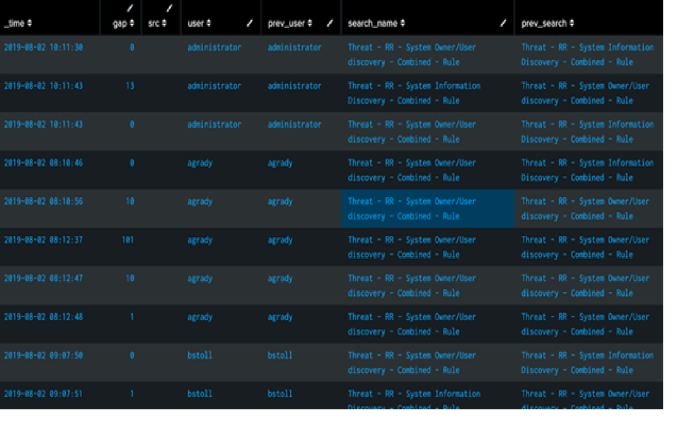
- The following SPL uses the autoregress command to take a value from a field in the previous row of events. The SPL also removes irrelevant events where the user does not match the previous user field with
|where user = prev_user.index=risk sourcetype=stash search_name IN ("Threat - RR - System Owner/User discovery - Combined - Rule","Threat - RR - System Information Discovery - Combined - Rule") | sort by user _time | dedup _time search_name user | delta _time as gap | autoregress search_name as prev_search | autoregress user as prev_user | where user = prev_user | table _time gap src user prev_user search_name prev_searchThe following screenshot displays the output when using the autoregress command where all irrelevant events are removed and the
prev_userfield is no longer required. - The following SPL uses the
prev_searchfield to identify when events occur in a sequence within a time range that is defined by thegapfield. This example uses 600 seconds or 10 minutes. Thesearch_name!=prev_searchensures that you see different events.index=risk search_name="Search1" OR search_name="Search2" | sort by user _time | dedup _time search_name user | delta _time as gap | autoregress search_name as prev_search | autoregress user as prev_user | where user = prev_user | table _time gap src user search_name prev_search | where search_name!=prev_search AND gap<600)The following screenshot displays the output of this SPL search:
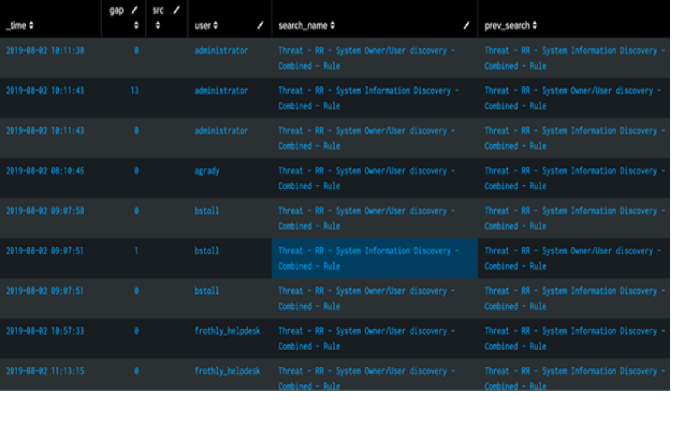
Run multiple searches in a specific order
Use additional autoregress commands and track the total gap to make sure different events are created in a sequence.
index=risk sourcetype=stash search_name IN ("Threat - RR - System Owner/User discovery - Combined - Rule","Threat - RR - System Information Discovery - Combined - Rule","Threat - RR - Permission Groups discovery - Combined - Rule")
| sort by user _time
| dedup _time search_name user
| delta _time as gap
| autoregress search_name as prev_search
| autoregress user as prev_user
| autoregress prev_search as pre_prev_search
| autoregress gap as prev_gap
| where user = prev_user
| table _time gap prev_gap src user search_name prev_search pre_prev_search
| eval total_gap = gap+prev_gap
| where search_name!=prev_search AND search_name!=pre_prev_search AND prev_search!=pre_prev_search AND total_gap<600
The following screenshot displays the output when you run the SPL search:
You can add as many searches as required to the base search and set up alerts when any of the searches fire in sequence. You can also ensure that sequenced events have specific "start" and "end" events by defining the searches in search_name and in pre_prev_search. You can add additional fields such as IP addresses, process names, and command lines to see more details for each individual event when a new search fires. You can use these sequenced searches as a direct alert or create a new risk event with a higher risk score than the risk detected by separate searches.
See also
| Review findings using the threat topology visualization in Splunk Enterprise Security | Create response plans in Splunk Enterprise Security |
This documentation applies to the following versions of Splunk® Enterprise Security: 8.0.0, 8.0.1, 8.0.2, 8.0.3, 8.0.31, 8.0.40

 Download manual
Download manual
Feedback submitted, thanks!