Edit a default entity type in ITSI
Every entity type in (ITSI) comes with at least one default metrics filter and one default events filter that populates the Analysis Workspace with data. You can delete a custom entity type in ITSI, but you can't delete a default entity type. For a list of default entity types in ITSI, see Default entity types and their properties.
Prerequisites
| Requirement | Description |
|---|---|
| ITSI roles | You have to log in as a user with the itoa_admin or itoa_team_admin role. |
Edit a default entity type
Perform the following steps to edit a default entity type in ITSI:
- From the ITSI main menu, click Configuration > Entity Management.
- Click Entity Types.
- Click Edit on the entity type you want to edit.
- After you make your changes, click Save.
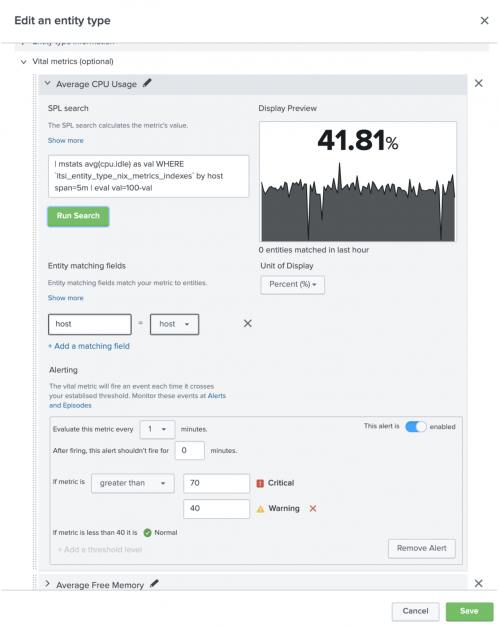
Configure vital metric alerts
You can configure alerts that generate notable events when vital metrics cross your established thresholds. Below displays the UI for the vital metric alert configuration:
Perform the following steps to configure vital metric alerts for default entity types:
- From the ITSI main menu, click Configuration > Entity Management.
- Go to the Entity Types tab.
- Click Edit on the entity type you want to edit.
- Expand the Vital Metrics (optional) section and select the vital metric that you want to create an alert for. The alert is applied to all entities categorized under the entity type that you create the alert for.
- In the Alerting section, click Add Alert. New alerts are enabled by default.
- In the alert window, set the alert schedule, a time to suppress the alert after it is fired, and alert thresholds for the vital metric.
- Set up trigger conditions for the thresholds. The Critical threshold is required. You can adjust this threshold value, but the threshold can't be deleted.
- (Optional) Click Add a threshold level to create a Warning threshold.
- For the If metric is field, select greater than or less than to set the threshold hierarchy. If you select greater than, the Critical threshold is a maximum threshold. If you select less than, the Critical threshold is a minimum threshold.
- (Optional) Use the Dimension is field to filter the alert by dimensions, such as, host, OS, etc. You can select multiple dimensions and multiple values of the same dimension. Multiple filter values of the same dimension are joined by OR. Filters of different dimensions are joined by AND. Wildcards, specified with an asterisk
*are supported. - Click Save.
- After configuring a vital metric alert, a new saved search is created in the local savedsearches.conf. For example, if you create a vital metric for Average CPU Usage for the *nix entity type, you'll see a searched called
[ITSI Vital Metric Alert - Average CPU Usage Alert for *nix entity type]. When you remove an alert, the saved search will be deleted.
Do more with ITSI
- You can monitor alerts on the Episode Review page. For more information, see Overview of Episode Review in ITSI.
- You can create notable event aggregation policies for your entity type alerts to group alerts into episodes. For more information, see Overview of aggregation policies in ITSI.
| Overview of entity types in ITSI | Create custom entity types in ITSI |
This documentation applies to the following versions of Splunk® IT Service Intelligence: 4.11.0, 4.11.1, 4.11.2, 4.11.3, 4.11.4, 4.11.5, 4.11.6, 4.12.0 Cloud only, 4.12.1 Cloud only, 4.12.2 Cloud only, 4.13.0, 4.13.1, 4.13.2, 4.13.3, 4.14.0 Cloud only, 4.14.1 Cloud only, 4.14.2 Cloud only, 4.15.0, 4.15.1, 4.15.2, 4.15.3, 4.16.0 Cloud only, 4.17.0, 4.17.1, 4.18.0, 4.18.1, 4.19.0, 4.19.1, 4.19.2, 4.19.3, 4.19.4, 4.20.0, 4.20.1
 Download manual
Download manual
Feedback submitted, thanks!