Install the Splunk App for Infrastructure in a Splunk Cloud deployment
You must be a Splunk Cloud administrator to install and manage apps in your Splunk Cloud environment. To install an app on Splunk Cloud, contact your Splunk sales representative or Splunk Support. You will need Splunk Support to complete these tasks:
- Add the Splunk App for Infrastructure (SAI) to your Splunk Cloud environment.
- Add the Splunk Add-on for Infrastructure to your Splunk Cloud environment.
- Enable the HTTP Event Collector (HEC) in your Splunk Cloud environment.
When Splunk Support installs the app and add-on, and configures HEC for your cloud environment, configure your Splunk Cloud instance and hosts to send data to SAI.
You have to use the sc_admin user to make configuration changes.
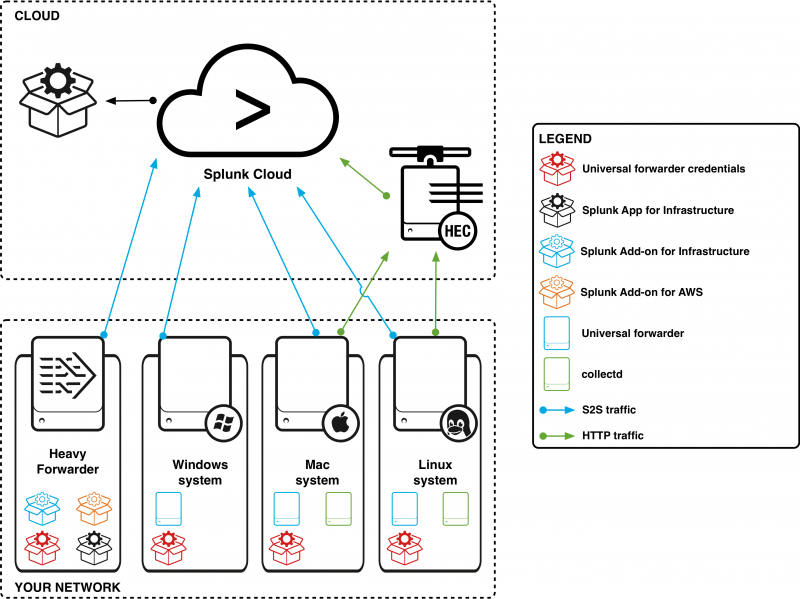
What the cloud deployment looks like
Install a universal forwarder for metrics and logs collection on Windows systems. Install a universal forwarder for logs collection and collectd for metrics collection for *nix systems. You have to install universal forwarder credentials on every system you install a universal forwarder on. Data the universal forwarder collects is sent to the indexing tier in the cloud environment.
You must install collectd on *nix systems for metrics collection. Collectd sends data to an HEC in the indexing tier in the cloud environment.
If you plan to send AWS data to SAI, you must deploy a heavy forwarder on a Windows or Linux system and install the Splunk Add-on for AWS, the Splunk Add-on for Infrastructure, and the universal forwarder credentials on it. To configure the heavy forwarder to send AWS data to SAI in the cloud environment, also install SAI on it.
This diagram describes a cloud environment that is ingesting data from a Windows system, a Mac system, a Linux system, and a heavy forwarder for AWS data collection.
Configure your cloud deployment for SAI
Follow these steps to set up your physical and cloud environment to start sending data to SAI.
1. Add the power role to sc_admin users
To fully configure and use SAI as an sc_admin user, ensure that all capabilities are assigned to each sc_admin user that has access to the cloud environment.
For more information about assigning the power capabilities to the sc_admin user, see sc_admin role permissions.
2. Configure the HTTP Event Collector (HEC)
To follow this step, Splunk Support must have already enabled HEC for your cloud instance.
If you plan to collect metrics data from a *nix system, you must create an HEC token. You don't have to set up HEC for Windows monitoring. When you create an HEC token, take note of the URI and port; you will need these things when configuring data collection on each system. For more information about creating an HEC token for Splunk Cloud, see Configure HTTP Event Collector on managed Splunk Cloud in the Splunk Enterprise Getting Data In manual.
After configuring an HEC token, you can start sending data to the HEC in your cloud environment. When you run the data collection script or manually configure data collection with SAI, you start sending data to the HEC. For more information about how sending data to an HEC works, see Send data to HTTP Event Collector on Splunk Cloud instances in the Splunk Enterprise Getting Data In manual.
Create the em_metrics source type and the HEC token:
- In Splunk Web, log in as an administrator.
- Go to Settings > Source types.
- Create a source type. For the Name, enter
em_metrics. For the App context, select theSplunk App for Infrastructure. - Go to Settings > Data inputs.
- In the Actions column for HTTP Event Collector, click Add new.
- For Select Source, do not check Enable indexer acknowledgement.
- For Input Settings, configure these settings:
- Source type: em_metrics
- App context: Splunk App for Infrastructure (splunk_ta_infrastructure)
- Index: em_metrics
- Generate the HEC Token to send data over the HEC to the Splunk Cloud instance.
- Confirm the token was created and take note of the Token Value. You need the Token Value when you start adding data.
To test the HEC configuration, make an HTTP PUT request to the HEC on the receiving port:
curl -k http-inputs-<STACKNAME>.splunkcloud.com:443/services/collector/event -H "Authorization: Splunk <HEC_TOKEN>" -d '{"event": "hello world"}'
{"text": "Success", "code": 0}
where:
<STACKNAME>is the the part of the hostname that identifies your cloud instance<HEC_TOKEN>is the HEC token value for your cloud instance
If you see the event in Splunk Web, you set up the HEC configuration correctly.
3. Install and configure the data collection agents on each applicable system
Do not run the easy install script or manually install data collection agents on a heavy forwarder that sends AWS data to SAI.
Use the easy install script to configure the data collection agents on each system that sends data to the cloud environment. For Windows systems, the easy install script installs and configures a universal forwarder. For *nix systems, the easy install script installs and configures a universal forwarder and collectd.
For information about the data collection script for each OS, see these topics in the Administer Splunk App for Infrastructure guide:
- Collect Windows metrics and logs with Splunk App for Infrastructure
- Collect Linux/Unix metrics and logs with Splunk App for Infrastructure
- Collect Mac OS X metrics and logs with Splunk App for Infrastructure
You can also manually set up the universal forwarder and collectd. For more information, see these topics in the Administer Splunk App for Infrastructure guide:
- Manually configure metrics and log collection for Windows on Splunk App for Infrastructure
- Manually configure log collection on a *nix entity for Splunk App for Infrastructure
- Manually configure metrics collection on a *nix entity for Splunk App for Infrastructure
When you are configuring data collection, use these port values so that your cloud stack receives data from your systems:
| Field | Value |
|---|---|
| Monitoring Machine | http-inputs-<cloud_hostname>.splunkcloud.com |
| HEC port | 443
|
| Receiver port | 9997
|
By default, you must be the root user to make changes to the universal forwarder directory.
After you run the script from the SAI user interface or manually set up data collection, remove outputs.conf:
- Default *nix location:
$SPLUNK_HOME/etc/apps/splunk_app_infra_uf_config/local/outputs.conf - Default Windows location:
$SPLUNK_HOME\etc\apps\SplunkUniversalForwarder\local\outputs.conf
4. Install universal forwarder credentials
Follow this step for each system that is not already sending data to your cloud environment. Otherwise, skip this step.
You must install the universal forwarder credentials file on each system that sends data to your cloud environment. The universal forwarder credentials file contains a custom certificate for your Splunk Cloud deployment. The universal forwarder credentials are different from the credentials that you use to log into Splunk Cloud.
If you have not already created a user for the universal forwarder, first create a user. To create a user, add credentials to a user-seed.conf file. For more information, see user-seed.conf in the Splunk Enterprise Admin Manual. If you modify a conf file, be sure to restart splunkd so your changes take effect.
By default, you must be the root user to make changes to the universal forwarder directory.
- Log in to your Splunk Cloud homepage.
- In the left sidebar, click Universal Forwarder.
- Click Download Universal Forwarder Credentials to download the
splunkclouduf.splfile. - From a command-line interface, go to the
$SPLUNK_HOME/bindirectory for your universal forwarder. - Run the following command:
where
./splunk install app <full_path_to_splunkclouduf.spl> -auth <username>:<password>
<username>:<password>are the login credentials for an existing account on the universal forwarder. - Restart the universal forwarder:
./splunk restart
5. Set up AWS data collection
When deploying a heavy forwarder to collect AWS data for SAI, you have to set up only forwarding on it. You do not have to set up receiving.
- If you plan to collect AWS data, install apps and add-ons things on a heavy forwarder:
- Splunk App for Infrastructure
- Splunk Add-on for Infrastructure
- Splunk Add-on for AWS version 4.5
- universal forwarder credentials
- Configure AWS data collection. For information, see Configure AWS data collection for Splunk App for Infrastructure.
For information about installing apps and add-ons, see Where to get more apps and add-ons in the Splunk Enterprise Admin Manual.
For information about deploying a heavy forwarder, see Deploy a heavy forwarder in the Splunk Enterprise Forwarding Data guide.
| Install the Splunk App for Infrastructure in a distributed deployment | Upgrade to a new version of Splunk App for Infrastructure |
This documentation applies to the following versions of Splunk® App for Infrastructure (EOL): 1.3.0, 1.3.1, 1.4.0, 1.4.1
 Download manual
Download manual
Feedback submitted, thanks!