Define aggregation rules to view related data in a single location. Artifacts matching a defined rule are copied to a new container.
To view aggregation rules, follow these steps:
- From the main menu, select Administration.
- Select Product Settings > Aggregation.
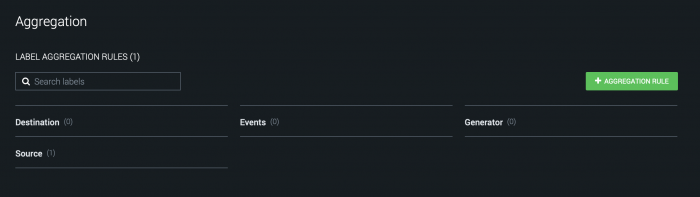
The Aggregation page shows a list of all container labels defined on your system. The number inside the parentheses next to each label is the number of rules defined for that label. Container labels can be created with an ingestion asset or by manually adding them on the Event Settings subtab. For example, in a production environment, you might pick a source label from an ingestion asset such as "Events" or "Email" and create a destination label such as "Aggregated Events" that makes it clear that containers with that label are aggregated.
Add a new aggregation rule
In this scenario, we want to aggregate artifacts with matching sourceAddress CEF fields. For events from numerous products, these fields are often the sender's IP address on a packet or connection that triggered an alert and represent an attacker's IP address. The name sourceAddress is not related to the source or destination label concept. It's a different kind of source. We want to give the rule a meaningful name using the "Source" and "Destination" labels in our example.
Follow this procedure to create an example aggregation rule:
- From the Aggregation page, click + Aggregation Rule.
- Specify sourceAddress - Email to Events as the name of the rule.
- Select email from the drop-down list in the Source Label field.
- Select events from the drop-down list in the Destination Label field.
- Select Exact from the Match field to aggregate on the exact contents of the CEF field. You can click on the plus (+) icon to add additional match rules.
- Select sourceaddress in the CEF field. You can start typing the field name to search through the list of available field names.
- If you have multiple tenants, select the right tenants from the Applies to field. The default is All tenants.
- Click Save.
On the Aggregation page, the 1 in parentheses next to email means there is one rule under the label email.
Edit an existing aggregation rule
After completing the previous example, perform the following steps to edit an existing aggregation rule in Splunk Phantom.
- Click on any existing rule. In this example, click email to view a summary of the aggregation rule.
- Click Edit to make changes to the rule.
- Click the trash can icon to remove the rule.
Click + Aggregation Rule to create a new rule. If you create a new rule from the email label rule page, the new rule will automatically populate the Source Label field with email.
By default, rules apply to all tenants. Only one rule per source label and tenant combination is allowed. "All Tenants" counts as a named tenant for this purpose. If you need to have another rule for the label "email", pick a specific tenant from the drop-down list, then create a second rule with source label "email".
Using multiple matches in an aggregation rule
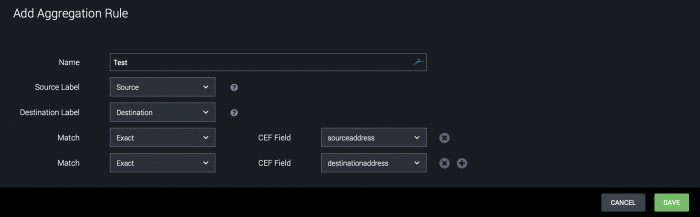
An aggregation rule can have multiple match lines. The following image shows an aggregation rule with an exact match on both sourceaddress and destinationaddress.
In this example, both the sourceaddress and destinationaddress must match for it to be aggregated into the same container.
If you treat sourceaddress as the attacker's IP address, and destinationaddress as the victim's IP address, then this means you have artifacts being aggregated in the same destination container for only the exact same attacker and victim. So with a victim IP address of 1.1.1.1, there is one destination container for attacker IP address 2.2.2.2 and victim IP address 1.1.1.1, and a different container for attacker IP address 3.3.3.3 and victim IP address 1.1.1.1.
CEF fields are matched even if there is no value. For example, if you have artifacts with a destinationaddress of 1.1.1.1 and no sourceaddress, they are still aggregated together into a destination container.
| Configure multiple tenants on your instance | Define tasks using workbooks |
This documentation applies to the following versions of Splunk® Phantom (Legacy): 4.8, 4.9, 4.10, 4.10.1, 4.10.2, 4.10.3, 4.10.4, 4.10.6, 4.10.7
 Download manual
Download manual
Feedback submitted, thanks!