Use filters to separate Splunk Phantom artifacts before further processing
Create conditions in a Filter block to separate a subset of artifacts or action results. Only the artifacts or action results matching the specified condition are passed along to downstream blocks for processing. This is useful when you want to remove items that aren't needed in the flow of the playbook, or you need to separate artifacts because they require different blocks for processing.
For example:
- If an IP address comes from North Korea or Turkey, you can block it.
- If an IP address comes from North America, you can perform an IP reputation lookup.
- If an IP address falls in the 192.168.10.* range, you can to grant access to the user.
Options in a filter aren't related to each other and you can perform multiple actions on an IP address. For example, both the second and third conditions in the example could be true, as an IP address in the 192.168.10.* range could both come from North America and be an internal user who was granted access. The filtered data set is given a named result in the format name="filter_1:condition_1" and passed to the next block for processing.
Create a Filter block in your playbook
To create a Filter block, perform the following tasks:
- Create a new block in the visual playbook editor (VPE).
- Select Filter from the list of block types.
- Click the Select Parameter field and select the parameter you want to filter on. Parameters are made available to the Filter block by upstream blocks.
- Click in the == field and select an operator for the filter.
- Click the Select Value field and select the value you want to match. See Example of creating a filter for an example of how these fields work together.
- (Optional) Click + to add parameters to this condition.
- (Optional) Click Add Condition to create another matching condition for the filter. You can have a maximum of five conditions per Filter block. Each condition has its own downstream path.
Settings
Follow these steps to configure the settings for a Filter block:
- Click Settings.
- Select Info or Advanced.
| Setting | Description |
|---|---|
| Info | Configure settings for this Filter block.
|
| Advanced setting | Description |
|---|---|
| Join Settings | You can configure Join settings when you have two blocks with callbacks both calling the same downstream block. Block types with callbacks are Action and Prompt. Configure Join settings from the downstream block. Click the required checkbox if the action in the upstream block must be completed before this downstream block is run. |
| Artifact Scope | Select a value from the drop-down menu. The setting determines which artifacts are processed when the playbook block runs.
|
| Case-insensitive | Check this box to make your filter ignore case. By default, filters are case-sensitive. |
Example of creating a filter
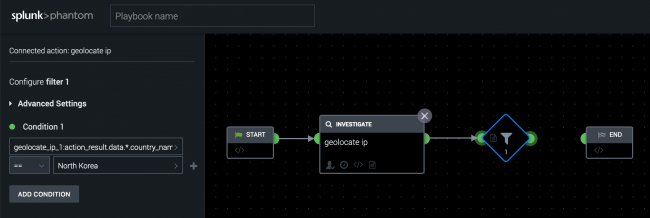
In the following example, you can create a filter to perform a geolocate ip action on a source IP address and block any IP addresses from North Korea. The following image shows the VPE in Splunk Phantom.
- Configure a
geolocate ipaction in the playbook editor. - Drag the half-circle icon on the
geolocate ipaction block in the editor. - Select Filter from the list of block types.
- Click the Select Parameter field and select geolocate_ip_1.
- Select geolocate_ip_1:action_result.data.*.country_name.
- Leave == as the operator, and type North Korea in the Select Value field.
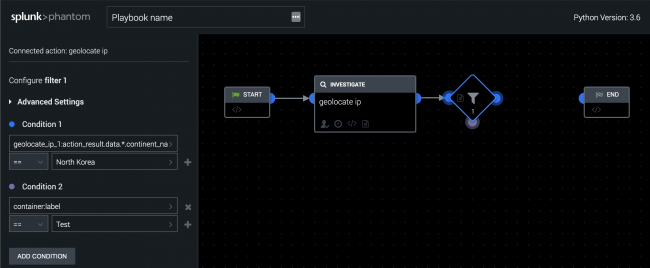
Example of creating a filter with multiple conditions
You can create multiple rows within a condition or multiple conditions. The following image shows an example of the VPE in Splunk Phantom.
- Click Add Condition to create a second set of filter conditions, which also adds a second output point on the Filter block.
- In the Select Parameter field, select container properties and choose label.
- Select == as the operator, and enter Test in the Select Value field.
Multiple conditions within a filter block are independent of each other. The results of Condition 1 don't play into the set of inputs for Condition 2. In this example, Condition 1 uses the result from the geolocate ip action, while Condition 2 uses a property of the container. Each condition has its own color to make it easier to identify the separate downstream actions. Blue marks the path of Condition 1 and purple marks the path of Condition 2.
Example of filter chaining
You can also chain multiple filter blocks together to obtain a more specific set of data.
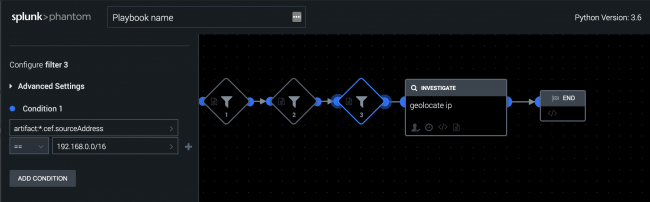
For example, to filter out RFC1918 addresses (10.x.x.x, 172.16.x.x-172.31.x.x, and 192.168.x.x) and perform a geolocate ip action on the remaining addresses, perform the following steps:
- From the Start block, create new filter block.
- In the Select Parameter field, select artifact:*.cef.sourceAddress.
- Enter 10.0.0.0/8 in the Select Value field.
- Create a second filter for the 172.16.0.0/12 IP addresses. This filter uses the filtered results from the previous block.
- Create a third filter for the 192.168.0.0/16 IP addresses. This filter uses the filtered results from the previous block.
- Create the
geolocate ipaction block on the remaining IP addresses.
If a filter block eliminates all variables while filtering, the downstream action can't run.
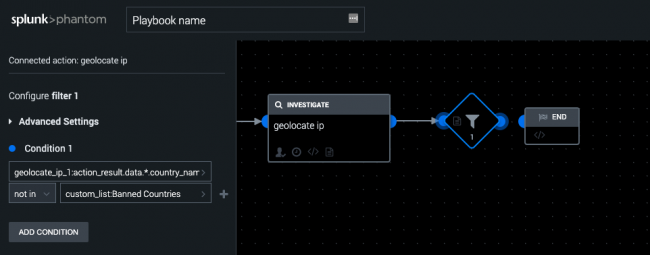
Example of using a custom list in a filter
You can use custom lists in your Filter blocks to simplify checking against a fixed set of items. For example, instead of checking the source country of an IP address to see if it is North Korea, you can define a list of countries in a custom list, then check the IP address against all of the countries in the list. You can maintain custom lists using the Splunk Phantom web interface, REST API, and playbook API. See Create custom lists for use in Splunk Phantom playbooks in Use Splunk Phantom. The following image shows the VPE in Splunk Phantom.
In this example, use a custom list named Banned Countries in a filter by performing the following tasks:
- Configure a
geolocate ipaction in the playbook editor. - Drag the half-circle icon on the
geolocate ipaction block in the editor. - Select Filter from the list of block types.
- Click the Select Parameter field and select geolocate_ip_1.
- Select geolocate_ip_1:action_result.data.*.country_name.
- Use "in" or "not in" as the operator.
- Click in the Select value field and select custom_list:Banned_Countries.
The country name of the source IP address is checked against the countries defined in the Banned Countries custom list.
| Add an Action block to a Splunk Phantom playbook | Use decisions to send Splunk Phantom artifacts to a specific downstream action |
This documentation applies to the following versions of Splunk® Phantom (Legacy): 4.10.4, 4.10.6, 4.10.7
 Download manual
Download manual
Feedback submitted, thanks!