Drill down on event details
After running a search that returns events in the Events tab, click on parts of those events to run different kinds of secondary drilldown searches that use the event detail that you have selected.
In the Events tab you can run a drilldown search when you click on these parts of an event:
- Segment (can be a connected string of segments)
- Field value
- Tag
- Timestamp
Drilldown searches for field values, tags, and segments
The drilldown searches can perform the following actions for fields, tags, and event segments.
| Drilldown search action | Description | Result |
|---|---|---|
| Add to search | Add a focus on the selected event detail to the original search string and run it. Splunk software discards transforming commands from the search string, as well as anything that follows them. | A dataset similar to the one returned by the original search, filtered to include only events that have the selected field, tag, or segment(s). |
| Exclude from search | Add an exclusion of the selected event detail to the original search and run it. Splunk software discards transforming commands from the search string, as well as anything that follows them. | A dataset similar to the one from the original search, filtered to include only events that do not have the selected field, tag, or segment(s). |
| Remove from search | Run a new search that is identical to the original search, except that it no longer searches for the highlighted field value, tag, or segment. Splunk software discards transforming commands from the search string, as well as anything that follows them. | A new dataset that is not as restrictive as the dataset returned by the original search. It no longer excludes events without the highlighted field value, tag, or segment. |
| New search | Run a new search that focuses exclusively on the selected field, tag, or segment(s). | A new dataset that contains any event which includes the selected field, tag, or segment(s). |
.
All of these drilldown searches use the same time range as the original search.
For example, start with this search. It has a time range of Last 7 days.
sourcetype=access_combined status=4*
In the results for that first search, open an event and select the value 69.72.161.186 for the clientip field.
If you click Add to search, the following search is run over the past 7 days.
sourcetype=access_combined status=4* clientip="69.72.161.186"
If you click Exclude from search, the following search is run over the past 7 days.
sourcetype=access_combined status=4* clientip!="69.72.161.186"
If you click Remove from search after running a secondary search, the following search is run over the past 7 days.
sourcetype=access_combined status=4*
If you click New search, the following search is run over the past 7 days.
clientip="69.72.161.186"
Run a drilldown search based on a field value, tag, or event segment
Fields are extracted from events at index time and search time. See "About fields" in the Knowledge Manager Manual.
A segment is a searchable part of an event. See "About event segmentation" in the Getting Data In Manual to learn how segments are configured and created.
Tags are associated with field-value pairs. A tag can be associated with multiple field-value pairs. A field-value pair can be associated with multiple tags. See "About tags and aliases" in the Knowledge Manager Manual.
1. In the Search & Reporting app, run a search or report that returns an event listing in the Events tab.
- If your search includes transforming commands, set the Search Mode to Verbose.
2. Reset the event display if necessary for the item that you wish to perform a drilldown search on.
- If you want to run a drilldown search on a field value and your have your event display set to:
- Raw, open the event to select actual field values.
- List or Table, you can select values from selected fields or you can open the event to select other field values.
- If you want to run a drilldown search on an event segment, set the event display to List or Raw.
3. Find an event with the field value, tag, or segment that you want to use for a drilldown search.
- Only selected fields and their tags display in unopened events. Open events to find additional fields and tags.
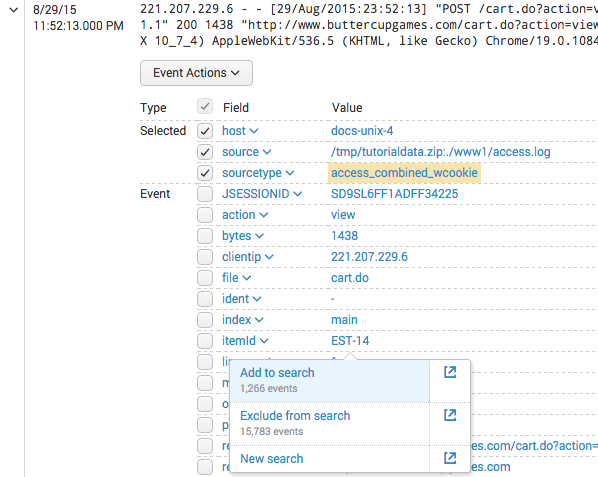
- Field values, tags, and segments that are explicitly included in the search string appear with yellow highlighting in the search results. In the example screen capture below, the original search included
sourcetype=access_*.
4. Click on the field value, tag, or segment.
- Select event segments and sets of connected segments before you click on them. Splunk software identifies your segment selection with yellow highlighting.
- After you click, a set of drilldown search options appears. The options are Add to search, Exclude from search, and New search. See the table at the top of this topic for explanations of these options.
- If you have selected a field value, and the value is among the top ten values found for its field, the Add to search and Exclude from search options display the number of events that they can return.
5. Click a drilldown search option.
- Run the secondary search in the current tab and replace your current search, or run the secondary search in a new tab and leave your current search results intact. To run the search in the current tab, click the option text. To open the search in a new tab, click the Open In New Tab icon
 for the option.
for the option.
- After running Add to search or New search, the matching value, tag, or segment in the events returned by the drill down search are highlighted. Highlighting does not happen when you run Exclude from search, because the events returned by that drilldown search do not contain the matching field value, tag, or segment.
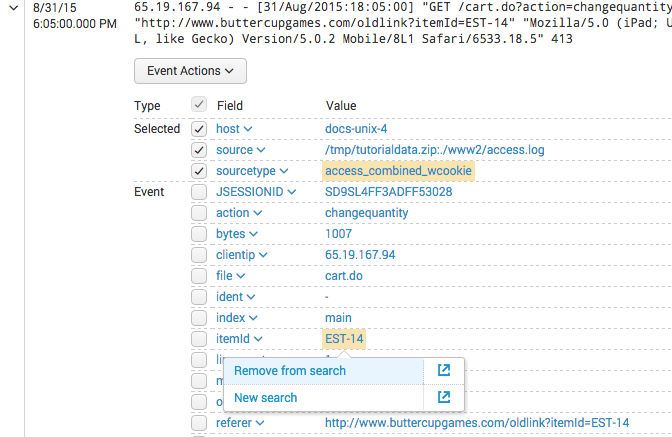
6. (Optional) After running the drilldown search, click on a highlighted field value, tag, or segment in an event returned by that search.
- Two secondary drilldown search options appear for the field value, tag, or segment: Remove from search and New search. See the table at the top of this topic for explanations of these options.
7. (Optional) Click on an option to run the search.
- You can run the search in the current tab or open it in a new tab, as described in Step 5.
Note: If you replace the results of your current search you can return to them by clicking the back button of your browser.
Drilldown searches for event timestamps
Event timestamp drilldown searches can help you find event correlations and perform root cause analysis.
Click on an event timestamp to run a secondary search that returns events which are chronologically close to that event.
When you open an event you can also click on the _time field to run this kind of drilldown search.
The controls for this search are called a _time accelerator. See "Use time to find nearby events" in this manual for details on how the _time accelerator is used.
| Use the timeline to investigate events | Identify event patterns with the Patterns tab |
This documentation applies to the following versions of Splunk® Enterprise: 7.0.0, 7.0.1, 7.0.2, 7.0.3, 7.0.4, 7.0.5, 7.0.6, 7.0.7, 7.0.8, 7.0.9, 7.0.10, 7.0.11, 7.0.13
 Download manual
Download manual
Feedback submitted, thanks!