x11
Description
The x11 command removes the seasonal pattern in your time-based data series so that you can see the real trend in your data. This command has a similar purpose to the trendline command, but it uses the more sophisticated and industry popular X11 method.
The seasonal component of your time series data can be either additive or multiplicative, defined as the two types of seasonality that you can calculate with x11: add() for additive and mult() for multiplicative. See About time-series forecasting in the Search Manual.
Syntax
x11 [<type>] [<period>] (<fieldname>) [AS <newfield>]
Required arguments
- <fieldname>
- Syntax: <field>
- Description: The name of the field to calculate the seasonal trend.
Optional arguments
- <type>
- Syntax: add() | mult()
- Description: Specify the type of x11 to compute, additive or multiplicative.
- Default: mult()
- <period>
- Syntax: <int>
- Description: The period of the data relative to the number of data points, expressed as an integer between 5 and 1000. If the period is 7, the command expects the data to be periodic every 7 data points. If you omit this parameter, Splunk software calculates the period automatically. The algorithm does not work if the period is less than 5 and will be too slow if the period is greater than 1000.
- <newfield>
- Syntax: <string>
- Description: Specify a field name for the output of the
x11command. - Default: None
Examples
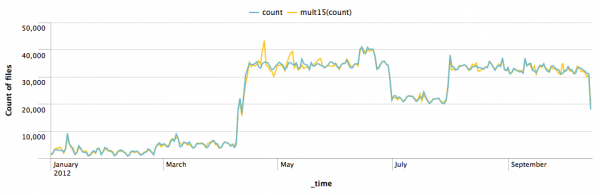
Example 1: In this example, the type is the default mult and the period is 15. The field name specified is count.
index=download | timechart span=1d count(file) as count | x11 mult15(count)
Because span=1d, every data point accounts for 1 day. As a result, the period in this example is 15 days.
You can change the syntax in this example to ... | x11 15(count) because the mult type is the default type.
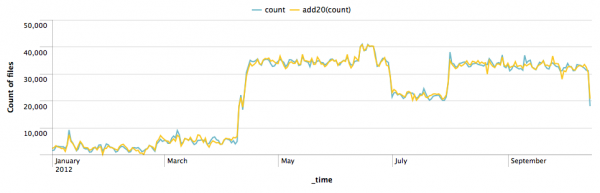
Example 2: In this example, the type is add and the period is 20. The field name specified is count.
index=download | timechart span=1d count(file) as count | x11 add20(count)
See also
| where | xmlkv |
This documentation applies to the following versions of Splunk® Enterprise: 7.0.0, 7.0.1, 7.0.2, 7.0.3, 7.0.4, 7.0.5, 7.0.6, 7.0.7, 7.0.8, 7.0.9, 7.0.10, 7.0.11, 7.0.13, 7.1.0, 7.1.1, 7.1.2, 7.1.3, 7.1.4, 7.1.5, 7.1.6, 7.1.7, 7.1.8, 7.1.9, 7.1.10, 7.2.0, 7.2.1, 7.2.2, 7.2.3, 7.2.4, 7.2.5, 7.2.6, 7.2.7, 7.2.8, 7.2.9, 7.2.10, 7.3.0, 7.3.1, 7.3.2, 7.3.3, 7.3.4, 7.3.5, 7.3.6, 7.3.7, 7.3.8, 7.3.9, 8.0.0, 8.0.1, 8.0.2, 8.0.3, 8.0.4, 8.0.5, 8.0.6, 8.0.7, 8.0.8, 8.0.9, 8.0.10, 8.1.0, 8.1.1, 8.1.2, 8.1.3, 8.1.4, 8.1.5, 8.1.6, 8.1.7, 8.1.8, 8.1.9, 8.1.10, 8.1.11, 8.1.12, 8.1.13, 8.1.14, 8.2.0, 8.2.1, 8.2.2, 8.2.3, 8.2.4, 8.2.5, 8.2.6, 8.2.7, 8.2.8, 8.2.9, 8.2.10, 8.2.11, 8.2.12, 9.0.0, 9.0.1, 9.0.2, 9.0.3, 9.0.4, 9.0.5, 9.0.6, 9.0.7, 9.0.8, 9.0.9, 9.0.10, 9.1.0, 9.1.1, 9.1.2, 9.1.3, 9.1.4, 9.1.5, 9.1.6, 9.1.7, 9.1.8, 9.1.9, 9.2.0, 9.2.1, 9.2.2, 9.2.3, 9.2.4, 9.2.5, 9.2.6, 9.3.0, 9.3.1, 9.3.2, 9.3.3, 9.3.4, 9.4.0, 9.4.1, 9.4.2
 Download manual
Download manual
Feedback submitted, thanks!