Generate a single value
Learn how to write a query to generate a single value visualization.
Single value visualizations work best for queries that create a time series chart using the timechart command or aggregate data using the stats command.
Use timechart to generate a single value
This search and visualization use timechart to track daily errors for a Splunk deployment.
index=_internal source="*splunkd.log" log_level="error" | timechart count
To access sparklines and trend indicators, it is important that the search includes the timechart command. Using timechart means that time series data becomes available to sparkline and trend indicator processing.
If you use the stats command as part of a full timechart query, the visualization does not include a sparkline or trend indicator.
Use stats to generate a single value
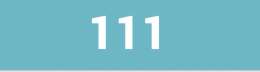
If you use the stats command to generate a single value, the visualization shows the aggregated value without a trend indicator or sparkline. As an example, this query and visualization use stats to tally all errors in a given week.
index = _internal source = "*splunkd.log" log_level = "error" | stats count
Queries and time ranges for single values
It is important to set up the single value query that best drives the visualization that you expect.
- Search for a single value to avoid unexpected results in the visualization. In the Dashboard Editor, you can select single value visualizations even if a search returns multiple values. In this case, the single value visualization uses the value in the first cell of the results table.
- The time range picker and the query command work together to generate the results for a single value visualization. A query using
statsresults in a visualization showing the aggregated total of results in the time range. A query usingtimechartgenerates a visualization showing the most recent result within that range.
For details about the stats command, see stats in the Search Reference.
For details about the timechart command, see timechart in the Search Reference.
Queries to generate a sparkline and trend indicator
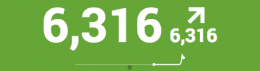
A sparkline appears by default below a single value generated with the timechart command. It shows increases and decreases in a metric over the time range you specify in a search.
This visualization shows results for a search over the past week's data. Using the time range picker to select Week to date means that the sparkline reflects the data changes over the last seven days.
This visualization shows results for the same search over the past day's data. Using the time range picker to select Today means that the sparkline shows data changes over the past twenty-four hours.
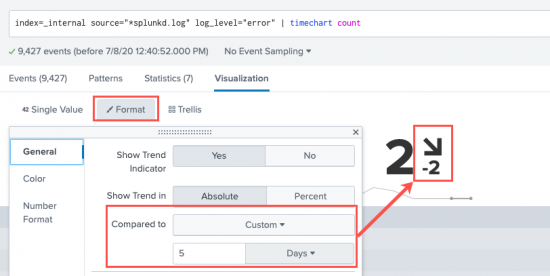
A trend indicator appears to the right of a single value generated with the timechart command. It shows recent data behavior over a customizable time range. The trend indicator is composed of a number and an arrow to represent what happened most recently in the data.
Depending on data behavior, the trend arrow can point up, down, or directly to the side to show no change. By default, the trend indicator value evaluates to the difference between the two most recent values in the results. You can change the trend time window in the Format menu's General settings panel or by adjusting the span parameter for timechart. if you use the Compared to field in the Format menu, it will override the span command you specified in the search string. For example:
index=_internal source="*splunkd.log" log_level="error" | timechart count
| Overview | Customize a single value |
This documentation applies to the following versions of Splunk® Enterprise: 7.0.0, 7.0.1, 7.0.2, 7.0.3, 7.0.4, 7.0.5, 7.0.6, 7.0.7, 7.0.8, 7.0.9, 7.0.10, 7.0.11, 7.0.13, 7.1.0, 7.1.1, 7.1.2, 7.1.3, 7.1.4, 7.1.5, 7.1.6, 7.1.7, 7.1.8, 7.1.9, 7.1.10, 7.2.0, 7.2.1, 7.2.2, 7.2.3, 7.2.4, 7.2.5, 7.2.6, 7.2.7, 7.2.8, 7.2.9, 7.2.10, 7.3.0, 7.3.1, 7.3.2, 7.3.3, 7.3.4, 7.3.5, 7.3.6, 7.3.7, 7.3.8, 7.3.9, 8.0.0, 8.0.1, 8.0.2, 8.0.3, 8.0.4, 8.0.5, 8.0.6, 8.0.7, 8.0.8, 8.0.9, 8.0.10, 8.1.0, 8.1.1, 8.1.2, 8.1.3, 8.1.4, 8.1.5, 8.1.6, 8.1.7, 8.1.8, 8.1.9, 8.1.10, 8.1.11, 8.1.12, 8.1.13, 8.1.14, 8.2.0, 8.2.1, 8.2.2, 8.2.3, 8.2.4, 8.2.5, 8.2.6, 8.2.7, 8.2.8, 8.2.9, 8.2.10, 8.2.11, 8.2.12, 9.0.0, 9.0.1, 9.0.2, 9.0.3, 9.0.4, 9.0.5, 9.0.6, 9.0.7, 9.0.8, 9.0.9, 9.0.10, 9.1.0, 9.1.1, 9.1.2, 9.1.3, 9.1.4, 9.1.5, 9.1.6, 9.1.7, 9.1.8, 9.1.9, 9.2.0, 9.2.1, 9.2.2, 9.2.3, 9.2.4, 9.2.5, 9.2.6, 9.3.0, 9.3.1, 9.3.2, 9.3.3, 9.3.4, 9.4.0, 9.4.1, 9.4.2

 Download manual
Download manual
Feedback submitted, thanks!