(Optional) Use Trellis view to visualize multiple aggregate functions
Sometimes it's useful to visualize more than one value shaded over the same map region. If you want to invoke multiple aggregate functions to create your choropleth statistics table, use the Trellis view to compare them side-by-side.
Prerequisites
- Locate and download USDM data
- Upload and configure your data
- Download a California counties shapefile
- Create a new geospatial lookup
- Generate a choropleth map
Steps
- When you're constructing the search that generates your choropleth statistics table, invoke multiple functions in the
statscommand. In this example, we compare average, maximum, and minimum drought scores:source="us_drought_monitor.csv" State = CA date_year=2018 | rex field=County "(?<County>.+) County" | eval droughtscore=D1 + D2*2 + D3*3 + D4*4 | stats avg(droughtscore) as "Average 2018 Drought Score" max(droughtscore) as "Max 2018 Drought Score" min(droughtscore) as "Min 2018 Drought Score" by County - Add the following to your search to use the
geomcommand in your SPL search to add the corresponding geospatial polygons to your table:| geom ca_county_lookup featureIdField=County - Run the search.
- In the Visualizations tab, notice that no shaded features appear because you have provided more than one aggregate value to map. Resolve this by selecting Trellis layout.
- Check the box labeled Use Trellis Layout.
- Under Split By, select Aggregations (3).
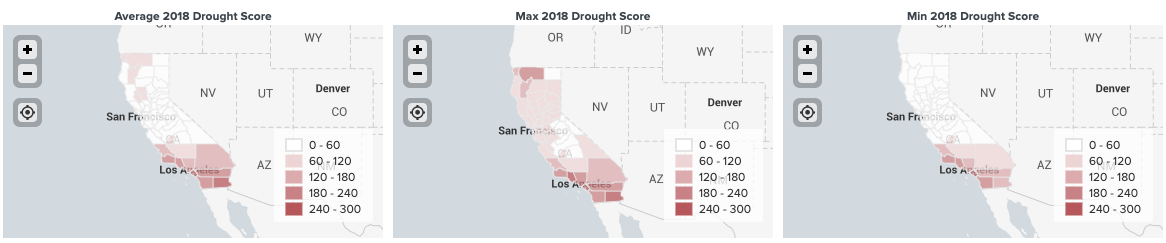
- Scroll and zoom to California in each map to compare the shading patterns of the three different values.
- Save the trellis map to your dashboard.
The Trellis map provides a visualization of three aggregate values side-by-side, to provide a fuller picture of drought conditions across California in 2018:
| Generate a choropleth map | Use trellis layout to split visualizations |
This documentation applies to the following versions of Splunk® Enterprise: 7.0.0, 7.0.1, 7.0.2, 7.0.3, 7.0.4, 7.0.5, 7.0.6, 7.0.7, 7.0.8, 7.0.9, 7.0.10, 7.0.11, 7.0.13, 7.1.0, 7.1.1, 7.1.2, 7.1.3, 7.1.4, 7.1.5, 7.1.6, 7.1.7, 7.1.8, 7.1.9, 7.1.10, 7.2.0, 7.2.1, 7.2.2, 7.2.3, 7.2.4, 7.2.5, 7.2.6, 7.2.7, 7.2.8, 7.2.9, 7.2.10, 7.3.0, 7.3.1, 7.3.2, 7.3.3, 7.3.4, 7.3.5, 7.3.6, 7.3.7, 7.3.8, 7.3.9, 8.0.0, 8.0.1, 8.0.2, 8.0.3, 8.0.4, 8.0.5, 8.0.6, 8.0.7, 8.0.8, 8.0.9, 8.0.10, 8.1.0, 8.1.1, 8.1.2, 8.1.3, 8.1.4, 8.1.5, 8.1.6, 8.1.7, 8.1.8, 8.1.9, 8.1.10, 8.1.11, 8.1.12, 8.1.13, 8.1.14, 8.2.0, 8.2.1, 8.2.2, 8.2.3, 8.2.4, 8.2.5, 8.2.6, 8.2.7, 8.2.8, 8.2.9, 8.2.10, 8.2.11, 8.2.12, 9.0.0, 9.0.1, 9.0.2, 9.0.3, 9.0.4, 9.0.5, 9.0.6, 9.0.7, 9.0.8, 9.0.9, 9.0.10, 9.1.0, 9.1.1, 9.1.2, 9.1.3, 9.1.4, 9.1.5, 9.1.6, 9.1.7, 9.1.8, 9.1.9, 9.2.0, 9.2.1, 9.2.2, 9.2.3, 9.2.4, 9.2.5, 9.2.6, 9.3.0, 9.3.1, 9.3.2, 9.3.3, 9.3.4, 9.4.0, 9.4.1, 9.4.2
 Download manual
Download manual
Feedback submitted, thanks!