Configure PowerShell logging to see PowerShell anomalies in Splunk UBA
The Suspicious PowerShell Activity model produces anomalies based on suspicious activity identified in Microsoft PowerShell and Windows security event logs.
You must log PowerShell activity at a specific level and add those logs to Splunk UBA for the PowerShell Activity model to work.
By logging PowerShell activity and analyzing the commands with Splunk UBA, you can identify indicators of compromise corresponding to malicious activity by a user or malware. PowerShell provides access to Windows API calls that attackers can exploit to gain elevated access to the system, avoiding antivirus and other security controls in the process. PowerShell is also internally utilized by popular hacking tools.
PowerShell versions compatible with Splunk UBA
The PowerShell model works best with PowerShell 5.0 or the latest version of PowerShell 4.0.
Windows 10 and 11 do not require any software updates to support enhanced PowerShell logging.
Windows Server 2016/2019/2022 does not require any software updates to support enhanced PowerShell logging.
| PowerShell version | PowerShell requirements |
|---|---|
| 4.0 | Powershell version 4.0 requires the following to enable enhanced logging for Windows 7/8.1/2008/2012:
|
| 5.0 | Powershell version 5.0 requires the following to enable enhanced logging for Windows 7/8.1/2008/2012:
|
Additional details
Review these additional details to succeed with the PowerShell model:
- PowerShell supports the following types of logging:
- module logging
- script block logging
- transcription
- PowerShell events are written to the PowerShell operational log
Microsoft-Windows-PowerShell%4Operational.evtx.
Configure module logging for PowerShell
Complete these steps to enable module logging:
- In the Local Group Policy Editor GPO settings, select Computer Configuration > Administrative Templates > Windows Components > Windows PowerShell, and set Turn on Module Logging to enabled. The following image shows this path in an example system:
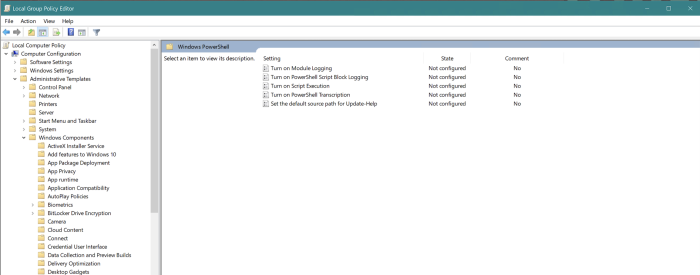
- In the Options pane, select the button to show Module Name.
- In the Module Names window, enter * to record all modules.
- Select OK in the Module Names window.
- Select OK in the Module Logging window.
Alternately you can set the following registry values:
HKLM\SOFTWARE\Wow6432Node\Policies\Microsoft\Windows\PowerShell\ModuleLogging → EnableModuleLogging = 1 HKLM\SOFTWARE\Wow6432Node\Policies\Microsoft\Windows\PowerShell\ModuleLogging \ModuleNames → * = *
Configure script block logging for PowerShell
To enable script block logging, go to the Windows PowerShell GPO settings and set Turn on PowerShell Script Block Logging to enabled.
Alternately, you can set the following registry value:
HKLM\SOFTWARE\Wow6432Node\Policies\Microsoft\Windows\PowerShell\ScriptBlockLogging → EnableScriptBlockLogging = 1
In addition, turn on command line process auditing. You can find instructions in the Microsoft documentation:
- Go to the Microsoft documentation website: https://docs.microsoft.com
- Search for command line process auditing.
- Configure command line process auditing so that the process creation audit event ID 4688 includes audit information for command line processes.
Configure transcription logging
To enable automatic transcription, or deep script block logging, enable the Turn on PowerShell Transcription feature in Group Policy through Windows Components > Administrative Templates > Windows PowerShell.
The configuration settings are stored under HKLM:\Software\Policies\Microsoft\Windows\PowerShell\Transcription.
You can find more information in the Microsoft documentation:
- Go to the Microsoft documentation website: https://docs.microsoft.com
- Search for script block logging.
Enable protected event logging
Splunk Enterprise does not support protected event logging. If your events are encrypted, decrypt them before ingesting to UBA. For details, see https://docs.microsoft.com/en-us/powershell/module/microsoft.powershell.core/about/about_logging_windows?view=powershell-7.2#enabling-script-block-logging
Verifying PowerShell logging
To verify that PowerShell logging is properly configured, look for the following PowerShell activity events in Splunk UBA:
- EventCode = 4103
- EventCode = 4104
- EventCode = 4688 and Process_Name contains PowerShell
- EventCode = 7045 and Process_Name contains PowerShell
| Send notable events from Splunk Enterprise Security to Splunk UBA | Configure the VirusTotal script to see VirusTotal anomalies in Splunk UBA |
This documentation applies to the following versions of Splunk® User Behavior Analytics: 5.0.0, 5.0.1, 5.0.2, 5.0.3, 5.0.4, 5.0.4.1, 5.0.5, 5.0.5.1, 5.1.0, 5.1.0.1
 Download manual
Download manual
Feedback submitted, thanks!