Pull notable events from Splunk ES to Splunk UBA
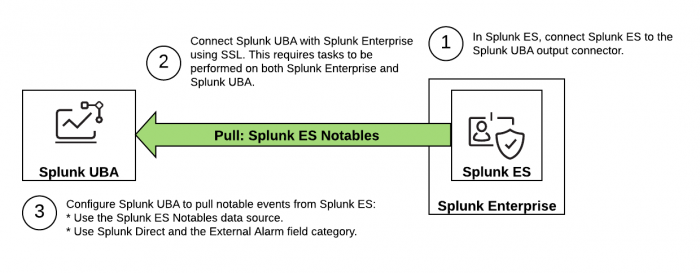
This image summarizes the steps you need to take to configure a Splunk ES Notables or Splunk Direct data source to pull notable events from Splunk Enterprise Security (ES) to Splunk User Behavior Analytics (UBA).
Perform the following tasks to set up the desired data source in Splunk UBA:
- In Splunk ES, Set up Splunk UBA to receive notable events from Splunk ES.
- In both Splunk Enterprise and Splunk UBA, Configure the Splunk platform to receive data from the Splunk UBA output connector.
- Set up Splunk UBA to pull notable events from Splunk ES. See Send notable events to Splunk UBA.
Set up Splunk UBA to receive notable events from Splunk ES
In Splunk ES, perform the following tasks so that Splunk UBA can receive notable events from Splunk ES:
Splunk Cloud Platform customers must contact Splunk Cloud Platform Support to perform the Splunk UBA setup.
- From the Splunk ES menu bar, select Configure > UBA Setup. You can also select Apps > Manage Apps and select Set up next to this add-on.
- In the Management Server field, type the host name and port number of the Splunk ES output connector on the Splunk UBA management server using port 10008. For example,
<server IP address>:10008. - In the Type field, select whether to use the TCP or UDP protocol to send the correlation search results to Splunk UBA.
Configure the Splunk platform to receive data from the Splunk UBA output connector
The connection between Splunk UBA and the Splunk platform uses TCP-SSL by default. Set up the Splunk platform to accept the encrypted connection so that the Splunk platform can receive data from the Splunk UBA output connector.
Splunk Cloud Platform customers must work with Splunk Cloud Platform Support to set up this connection.
The following procedure uses the Splunk default certificates and the global [SSL] stanza in the inputs.conf file. For better security, consider using your own certificates, or commercially signed certificates from a trusted certificate authority.
- See About securing Splunk Enterprise with SSL in the Splunk Enterprise Securing the Splunk Platform manual.
- See TCP: in the Splunk Enterprise Admin Manual for more information about configuring tcp-ssl using inputs.conf.
Perform the following steps on the Splunk Enterprise search head. In a search head clustering environment, perform the changes on the search head that will receive UBA threats and anomalies:
- Create a
localfolder under$SPLUNK_HOME/etc/apps/Splunk_TA_ueba. For example:cd /opt/splunk/etc/apps/Splunk_TA_ueba mkdir local cd local
- Create a file called inputs.conf and add the following stanza. The
sslPasswordholds the password for the server certificate. The value forsslPasswordmust match what is in thesslConfigstanza in the /etc/system/default/server.conf file:[tcp-ssl:10008] listenOnIPv6 = no index = ueba sourcetype = ueba serverCert = $SPLUNK_HOME/etc/auth/server.pem sslPassword = password
- Restart Splunk Enterprise.
- In Splunk Web, select System > Server controls.
- Click Restart Splunk.
- Verify that SSL is enabled for port 10008 in
$SPLUNK_HOME/var/log/splunk/splunkd.log. For example:11-07-2019 15:07:42.661 -0800 INFO TcpInputProc - Creating raw Acceptor for IPv4 port 10008 with SSL
- Copy the root CA certificate from
/opt/splunk/etc/auth/cacert.pemon the Splunk Enterprise instance to/home/caspidaon the Splunk UBA management server.
Perform the following tasks on the Splunk UBA management server:
- Log in to the Splunk UBA management server as the caspida user.
- Ensure that
$JAVA_HOMEis set correctly on your system. Run theCaspidaCommonEnv.shscript to set this environment variable:. /opt/caspida/bin/CaspidaCommonEnv.sh
- Import the rootCA certificate to the Java certificate store.
On RHEL or CentOS systems, use the following command:sudo keytool -import -alias "splunk es" -keystore $JAVA_HOME/lib/security/cacerts -file ~/cacert.pem
On other Linux systems, use the following command:
sudo keytool -import -alias "splunk es" -keystore $JAVA_HOME/jre/lib/security/cacerts -file ~/cacert.pem
- When prompted, type the keystore password and trust the certificate. The default keystore password is
changeit. - From the command line of the Splunk UBA management server, view the
/etc/caspida/local/conf/uba-site.propertiesfile to confirm the following parameter is set to "true" as shown:
connectors.output.splunkes.ssl=true - Restart Splunk UBA. Run the following commands on the Splunk UBA management server:
/opt/caspida/bin/Caspida stop-all /opt/caspida/bin/Caspida start-all
Send notable events to Splunk UBA
Use one of the following methods to send notable events from Splunk ES to Splunk UBA:
- Send notable events and risk events using the Splunk ES Notables data source
- Send notable events using Splunk Direct
Send notable events and risk events using the Splunk ES Notables data source
Use the Splunk ES Notables data source in Splunk UBA to integrate Splunk UBA with Splunk ES. Configure Splunk UBA to connect to the Splunk ES search head. The Splunk ES Notables data source automatically ingests notable events and risk events from Splunk ES and properly maps categories from Splunk ES Content Updates. If you have custom correlation searches in Splunk ES, make sure the category field is added correctly in the correlation search.
See Filter the anomaly table in Use Splunk User Behavior Analytics to view the list of anomaly categories. The category field must match one of the listed categories. The Splunk UBA external alarm model uses these events and category mappings to generate meaningful anomalies which can subsequently raise the appropriate threats.
Notable events that are closed in Splunk ES are not ingested by Splunk UBA.
- In Splunk UBA, select Manage > Data Sources.
- Click New Data Source.
- In the SIEM Connectors category, click Splunk ES Notables.
- On the Connection screen, provide connection and authentication details to connect to Splunk ES, then click Next. The user credentials must have permissions to access the notable events and risk indexes.
- On the Time Range screen, select Live and All Time, then click Next.
- On the Splunk Query screen, verify the SPL being used to retrieve the events and category mappings from Splunk ES, then click Next. If you need to modify the SPL, make sure
NOT (source="UEBA" OR source="UBA")is included in the final SPL to exclude Splunk UBA anomalies and threats. - On the Test Mode screen, click Test Mode to validate the data source before ingesting all events, then click Next. See Add data sources to Splunk UBA in test mode for more information about test mode.
- Click OK.
Send notable events using Splunk Direct
Use Splunk Direct to send notable events from Splunk ES to Splunk UBA by configuring an external alarm data source. Write a custom query to handle the necessary data enrichment such as mapping the alarm category or severity.
- In Splunk ES, confirm that you get the desired notable events from the following query. The query analyzes notable events on Splunk ES that are not generated from Splunk UBA data sources and performs the proper mappings for the External Alarm category on Splunk UBA.
You will need this query in the following steps.
`notable` | search NOT (source="*UEBA*" OR source="*UBA*") | eval action=IF(action="deferred" OR action="blocked","blocked","allowed") | eval tag="attack,network,communicate", app='Authentication.app', dest_zone='dest_pci_domain', src_host='src_nt_host', src_zone='src_pci_domain' | eval severity="Critical",evcls=coalesce(signature,savedsearch_name,search_name) | eval signature=IF(isnull(signature),evcls,signature) | eval alarmCategories=CASE( like(lower(evcls),"%application%") OR like(lower(evcls),"%vulnerability%"),"ProductAttack", like(lower(evcls),"%intrusion%"),"SystemAttack", like(lower(evcls),"%data%loss%") OR like(lower(evcls),"%dlp%") OR like(lower(evcls),"%dlp%") OR like(lower(evcls),"%exfil%"),"Exfiltration", like(lower(evcls),"%malware%") OR like(lower(evcls),"%virus%") OR like(lower(evcls),"%botnet%") OR like(lower(evcls),"%backdoor%") OR like(lower(evcls),"%trojan%"),"MalwarePersistence", like(lower(evcls),"%malware%_operations") OR like(lower(evcls),"%cnc%") OR like(lower(evcls),"%callback%"),"MalwareActivity", like(lower(evcls),"%spam%") OR like(lower(evcls),"%phish%"),"MalwareInstall",1=1,"PolicyViolation") | eval user=IF(isnull(user) AND like(dest,"%@%"),dest,user), dest_ip=coalesce(dest_ip,'values(dest)'),eventtype=evcls, user=IF(like(user,"%wireless%"),"",user), src_ip=IF(isnull(src_ip) AND NOT like(src,"%@%"), src,src_ip), dest_ip=IF( like(dest_ip,"%@%"),'',dest_ip) | makemv delim="," tag | makemv delim=" " dest_ip | mvexpand dest_ip | fields action,alarmCategories,app,category,dest_host,dest_ip,dest_nt_domain, dest_zone,duration,eventtype,file_name,file_path,severity,signature, sourcetype,src_host,src_ip,src_zone,tag,url,user - In Splunk UBA, select Manage > Data Sources.
- Click New Data Source.
- Under SIEM Connectors, select Splunk.
- Specify the connection details to Splunk ES. Select Splunk Direct as the connector type and specify the SSL management port for your Splunk ES instance.
- Select Live and All Time as the date range.
- In the Splunk Query field, specify the query that you verified at the beginning of this procedure.
- On the Data Format page, select External Alarm as the field category. Keep the default values in the Splunk Field column.
- Enter the query that you verified at the beginning of this procedure again.
- Make sure Test Mode is not selected, and then click OK.
| Send Splunk UBA anomalies and threats to Splunk ES as notable events | Send Splunk UBA audit events to Splunk ES |
This documentation applies to the following versions of Splunk® User Behavior Analytics: 5.0.0, 5.0.1, 5.0.2, 5.0.3, 5.0.4, 5.0.4.1, 5.0.5, 5.0.5.1
 Download manual
Download manual
Feedback submitted, thanks!