Create a custom time series model by cloning an existing model
Cloning an existing model is the best way to get started when creating a custom model of your own. As you navigate your way through the Splunk UBA web interface, the fields are pre-populated using the parameters of the existing model. Edit only the fields you want to customize.
Perform the following steps to create a custom time series model by cloning an existing time series model:
- In Splunk UBA, select System > Models.
- Click Custom Models.
- Click New Custom Model.
- Select a model type.
- Review the cube and attributes.
- Select the tracking feature.
- Configure filters for the tracking features.
- Configure the model attributes.
- Configure the model parameters.
- Configure supporting evidence to be displayed on the Anomaly Details page.
- Configure the anomaly attributes.
- Configure the anomaly fields.
- Click OK.
Select a model type
Clone an existing time series model to create a new model of your own:
- Select the Time Series Model type.
- Click Clone from existing model and select a model from the drop-down list.
- Click Next.
Review the cube and attributes
The cube that is currently used by the model appears in the Cube field. The cloned cube uses the same cube as the original model. You can't change the cube in your cloned model.
Click Next when you are ready to proceed.
Select the tracking feature
Select the desired tracking feature:
- Select the tracking feature.
Field Description Tracking Feature The name of the attribute from the view that is being used by the model. You can only select one tracking feature in a time series model. Display Name The user-friendly version of the tracking feature. For example, if the tracking feature is numEventsyou might enter a display name such as Number of Events.Peer Group Select the name of the OU group, behavior group, or device group if you want users or devices to be compared to other members of the group. Select None to disable peer group comparisons. - Click Next.
Configure filters for the tracking features
Write a SQL expression to specify additional filtering for the selected tracking feature:
- Click Add filtering field to specify a SQL statement in the Filtering Field section. For example, if you are tracking the
loginServerTypefeature you can create a filter such as the following so that VPN servers are not tracked by the model:loginServerType != 'VPN'
If you configure multiple filters, a logical AND condition applies to all the filters. - Select the Exclude Last Day if you do not want data from the current day to be analyzed by the model. For example, you might want your model to perform baselining only on a full day's worth of data and not include any partial days.
- Click Next.
Configure the model attributes
The attributes that are currently in use by the model appear on this page. Edit the fields as desired for your own model:
- Enter a name for the model. This is the name that is be stored in the system, such as WindowsLogs_Cloned. The model name must not exceed 25 characters.
- Enter a display name for the model. For example, you might want the WindowsLogs_Cloned model to be displayed as Rare Microsoft Windows Events Model Clone.
- Enter a description.
- Enter a version number in the format
x.x. For example:1.1. - Select the Splunk UBA entity (User or Device) you want this model to track.
- Click Next.
Configure the model parameters
The parameters that are currently in use by the model appear on this page. Edit the parameters as desired for your own model:
- By default Splunk UBA data cubes store data for 30 days. Use the Lookback field to configure Splunk UBA to retain more than 30 days of data. By default, the lookback value is set to 100 months. The reason for setting the memory to such a large value is that if you want to change the lookback window after the model is already running, it is preferable to edit the cube to retain more data than to change the parameters in the model. Be sure that your system can handle the additional space requirements if you want your cubes to retain more data. If you configure a memory that is larger than the retention period of the data cube, the model only analyzes the amount of data that is in the cube.
- In the Time Frequency field, specify a daily or weekly window of time that the model uses to analyze your data.
Parameter Description Lookback Time Units You can select a daily or weekly sliding time window for the model to analyze your data. For example, click Daily and enter 7 in the Lookback Time Units for the model to produce a baseline using 7 days of data. If you configure both daily and weekly windows, an anomaly is raised in either of the following cases: - The daily value is anomalous compared to the daily baseline value.
- The weekly value is anomalous compared to the weekly baseline value.
You can specify multiple comma-separated values. For example, in the Daily Time Frequency section, specify3,5to have the model look back 3 and 5 days. An anomaly is raised if the daily value is anomalous compared to both the 3-day and 5-day baselines.Percentile Threshold The right-tail percentile which, if exceeded, is considered anomalous. For example, you can start with a value such as 0.05. If you determine that the anomaly is generating too much noise, you can reduce the value accordingly, for example, from 0.05 to 0.01. Absolute Threshold The threshold at which, if not exceeded, the value is not considered anomalous. The value you enter here depends on the values you want the model to track. For example, if you are tracking the number of anomalous logins per day, you can set this value to 8, but if you are tracking total bytes transferred out of the network, you can specify 35000000, or approximately 33 MB.
Setting this value can help you eliminate false positives. For example, suppose you have a device which mostly sends out a small amount of traffic for network heartbeats, such as 1 KB, and then one day there is an upload of 1 MB. This activity is definitely anomalous, but also not that interesting given the scope of many large networks. You can set the absolute threshold here to 20 MB so that the behavior in this example is not raised as an anomaly.Min Baseline Days The minimum number of days worth of data that must exist for this model to run. - Click Next.
Configure supporting evidence to be displayed on the Anomaly Details page
Configure the fields you want to be displayed as supporting evidence on the Anomaly Details page. The selected columns are used to show the breakdown of the tracking features on the Anomaly Details page.
The following image is an example of the breakdown panel on an Anomaly Details page, populated with example data :
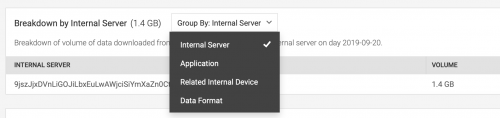
The Anomaly Details page includes the following fields:
| Field | Description |
|---|---|
| Column | The name of the attribute for which the breakdown is shown as supporting evidence. |
| Description | A description of the selected attribute. This is the text that is shown in the drop-down list in the Splunk UBA web interface. |
| ID Column | If the attribute is an entity, select the attribute which contains its ID. |
| Entity Type | If the attribute is an entity, select the entity type. Select None if the attribute is not an entity. |
| Scope | Specify whether the attribute is an internal user or internal device. |
| Search | Click Include in SPL to include this attribute in the event drilldown search. See Use event drilldown to review an anomaly's raw events. |
Configure the anomaly attributes
The anomaly attributes that are currently in use by the model appear on this page. Edit the attributes for the anomaly you want to be generated by this model:
- Specify a name and description for the anomaly.
- Select one or more categories you want to apply to the anomaly. Splunk UBA threat models use anomaly categories to generate specific types of threats. See Filter the anomaly table by anomaly category for a listing and descriptions of anomaly categories in Splunk UBA.
- Click Next.
To edit the scoring properties of the anomaly, modify the anomaly scoring rules. See Customize anomaly scoring rules.
Customize the anomaly fields
Customize each anomaly field name and description. These names and descriptions appear in Splunk UBA.
| Create a custom rare events model by cloning an existing model | New custom models in test mode |
This documentation applies to the following versions of Splunk® User Behavior Analytics: 5.0.0, 5.0.1, 5.0.2, 5.0.3, 5.0.4, 5.0.4.1, 5.0.5, 5.0.5.1, 5.1.0, 5.1.0.1, 5.2.0, 5.2.1, 5.3.0, 5.4.0, 5.4.1, 5.4.1.1, 5.4.2, 5.4.3
 Download manual
Download manual
Feedback submitted, thanks!