View user information
Review information about a user's activities in your environment on the User Facts page:
- Select Users from the Home page, or select Explore > Users from the menu to access the Users Table.
- Select any individual user to view their User Facts page.
At the top of each user's view, you can:
- Review the Last Update date and time to see how recent the information for this user or account is.
- Add the user to a Watchlist to track the account more closely.
- Review Account to see the type of accounts associated with the user, such as Normal, Admin, or Machine.
Monitor a user with a Watchlist
You can use Watchlists to track specific users or accounts more closely. Review the activity of users or accounts on Watchlists on the Threats Dashboard, Anomalies Dashboard, and Users Dashboard.
See Investigate Splunk UBA entities using Watchlists for more information about watchlists.
Adding a user to a Watchlist does not change the behavior of the models generating anomalies or threats, but you can use Watchlists to create threats or anomalies based on the behavior of users or accounts added to Watchlists. See Monitor policy violations with custom threats to create a custom threat, or Take action on anomalies with anomaly action rules to create an anomaly rule.
Add a user to a Watchlist
To monitor a user more closely, add them to a Watchlist. Complete the following steps:
- From the UBA navigation menu, select Manage > Watchlists.
- Select New User Watchlist to create a custom watchlist, or User Watchlist to add the user to the default watchlist.
- Enter a Name for the new watchlist and optionally add a Description.
- Select OK to save.
Remove a user from a Watchlist
Stop monitoring a user and remove them from a watchlist.
- From the UBA navigation menu, select Manage > Watchlists.
- Click the name of the Watchlist the user is on to remove them.
User information
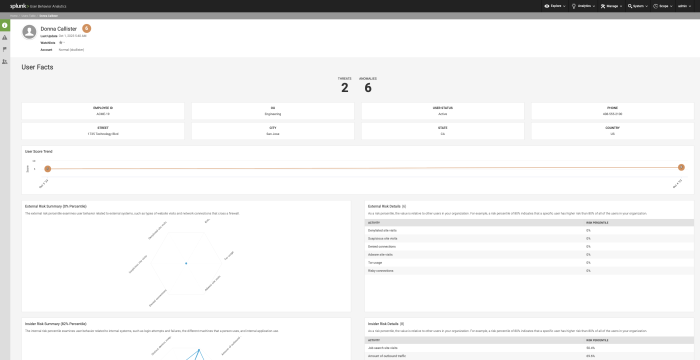
Review the User Facts page for a user to understand key aspects of a specific user. You can see User Facts by selecting a user's name from any view in Splunk UBA. For example, select Explore > Users and select the name of a user.
Key indicators
Get an overview of the user's activity with overall counts for various key indicators of user activity. If the count is zero, you cannot click through to view more details.
- Number of Threats associated with the user account. Select User Threats.
- Number of Anomalies associated with the user account. Select User Anomalies.
Learn more about user role information
Understand the role of the user in your environment with several panels that allow you to easily review basic user information.
- Employee ID number
- The user's Organizational Unit (OU) or department
- Contact information like a phone number or email address
- Login ID
- Location data like City, State, and Country
Review environment activity
See which threats, anomalies, devices, and domains associated with the user.
- See threats associated with the user and the risk scores for each threat. Click to view the User Threats page.
- See anomalies associated with the user and the risk scores for each anomaly. Click to view the User Anomalies page.
- See the devices involved with the user's anomalies. Both internal and external devices are listed by IP address, with the risk score associated with each one. Click to see Device Information for a listed device.
- See the domains involved with the user's anomalies. Click to see Domain Information for a listed domain.
Understand user score trend
The User Score Trend panel displays risk score changes over time.
Understand user risk scores
A user's risk score is determined primarily by the number of anomalies and threats associated with that user. A higher number of anomalies or threats of the same type will result in a higher user risk score.
Models and rules in Splunk UBA use varying algorithms to generate a user's risk score, meaning that not all anomaly types carry the same weight. For example, a user with five anomalies of a certain type may have a different risk score from another user with five anomalies of a different type.
Understand user risk percentiles
Risk percentiles on an individual user's page help you better understand the risk that the user poses to your organization in comparison to other users. Risk percentiles are generated based on a predefined set of activities and are completely separate from risk scores. Risk percentiles are not used in determining a user's risk score, nor are they based on any anomalies or threats.
For example, suppose a user has visited suspicious sites 5 times in the last 30 days, while no one else in his peer group of 100 users has visited any suspicious sites more than twice in the same time span. The user would be in the 100th risk percentile compared to his peers. However, visiting this suspicious site five times in one month is not enough to generate any anomalies, which means his activity has no bearing at all on his risk score. If the user did have a high risk score, the risk score would be based on other anomalies or threats generated against this user.
Splunk UBA tracks the following percentiles on the user page:
- External risk. See Understand user external risk percentile.
- Internal risk. See Understand user internal risk percentile.
Understand user external risk percentile
The external risk percentile examines user behavior related to external systems, such as types of website visits and network connections that cross a firewall. Review the External Risk Summary panel to quickly identify the elements contributing to a user's external risk percentile. Several elements of a user's activity contribute to their risk percentile. Use the External Risk Details panel to see more details contributing to the external risk percentile for the user.
- Denylisted site visits. Excluded sites are defined by the domain deny list.
- Suspicious site visits. Suspicious sites are defined by a list of suspicious IP addresses included with Splunk UBA.
- Denied connections. User activity resulting in connections denied by a firewall is based on aggregate events from firewall data in Splunk UBA.
- Adware site visits. Adware sites are defined by a list of adware sites included with Splunk UBA.
- Tor usage. Use of Tor is identified with the IntelTorIPList.
- Risky connections. User activity resulting in a risky connection is based on aggregate events from firewall data in Splunk UBA.
Understand user insider risk percentile
The insider risk percentile examines user behavior related to internal systems, such as login attempts and failures, the different machines that a person uses, and internal application use. Review the Insider Risk Summary panel to quickly identify the elements contributing to a user's insider risk percentile. Use the Insider Risk Details panel to understand the specific behaviors contributing to the user's insider risk percentile.
- Job search site visits. Job search site visits are identified by aggregate events from the data in Splunk UBA.
- Amount of outbound traffic. Outbound traffic amounts are based on aggregate events from firewall data in Splunk UBA.
- Failed logins. Login failures identified by the AD authentication system.
- Login attempts. Attempts to log on to a system, whether they were successful or failed. A high number of login attempts could indicate elevated risk of account takeover by an attacker.
- Distinct devices usage. The number of devices or machines that a person logs on to can indicate the level of risk they pose to the organization internally. A person who logs on to one or two devices regularly makes it easier to quarantine their account if compromised, but users that regularly log on to a high number of machines could increase the attack surface of an attacker who compromises their account.
- Denied access. The number of times that someone logs in to a device or application to which they do not have access. This can indicate someone attempting to maliciously access applications or data that they do not have authorization to use or view.
- Risky applications per usage. This percentile score is weighted by the number of times a person uses a risky application. If a person uses three risky applications several times a day, their risk percentile will be high compared with the rest of the organization if most people in the organization use one risky application once a month.
- Account lockouts. The number of times that a person's account is locked in the AD authentication system. A person whose account is locked out often can indicate login problems, attempts by an attacker to brute force their password, or other malicious issues.
Review user activity
Review the user's information transfer activity with the Data Transfer by Source Device and HTTP Transfer by Domain panels.
- See how much data is transferred and to which device IP addresses in the Data Transfer by Device panel. Click to view the Devices Table filtered on the selected device and user.
- See how much data is transferred and to which domain names in the HTTP Transfer by Domain panel. Click to view the Domains Table filtered on the selected domain and user.
Monitor the user's login activity on the Logins by Destination Device and Logins by Session Type panels.
- Review user login activity by server IP address on the Logins by Destination Device panel. Click to view the Logins Table filtered by the selected server IP address and user.
- Review user session logins on the Logins by Session Type panel. See how many sessions were VPN or other session types. Click to view the Logins Table filtered by the selected session type and user.
Understand typical user activity with the User Events Trend panel; consider spikes in this panel to spot spikes of user activity that could be suspicious.
Review the Device Attributions to see which devices are associated with this user account. Click a device to see the original event or events that tied this user or user account to a specific device in a particular time period.
User Anomalies
Open the anomalies view for a specific user:
- Select Users from the Home page, or select Explore > Users from the menu to access the Users Table.
- Select an individual user.
- Click the
 icon, or click Anomalies near the top of the User Facts section.
icon, or click Anomalies near the top of the User Facts section.
The user anomalies view allows you to see all anomalies associated with the selected user.
- The User Anomalies Timeline panel shows the types and risk levels of anomalies associated with a user over time. Click an anomaly to view the selected anomaly on the anomalies table.
- The User Anomalies Trend panel shows the number of anomalies associated with the user over time. Click the graph to view the selected anomaly on the anomalies table.
- The User Anomalies table shows all anomalies associated with the user. You can sort the table by anomaly type, event date, risk score, or anomaly summary. Download the anomalies associated with the user in a CSV file by clicking the Save as CSV icon. Click an anomaly to see the Anomaly Details.
User Threats
Open the threats view for a user:
- Select Users from the Home page, or select Explore > Users from the menu to access the Users Table.
- Select an individual user.
- Click the
 icon, or click Threats at the top of the User Facts section.
icon, or click Threats at the top of the User Facts section.
The user threats view allows you to see all threats associated with the selected user.
- The User Threats Timeline panel shows the threats associated with a user over time. Click to view the specific threat on the Threats Table.
- The User Threats table shows all threats associated with a user. Review the threat type, participants, start date, last update, and risk score. You can sort the table by column values, or save the table as a CSV by clicking the Save as CSV icon. Click a threat to view the Threat Details.
User Sessions
To view the sessions associated with a user:
- Select Users from the Home page, or select Explore > Users from the menu to access the Users Table.
- Select an individual user.
- Click the the
 icon.
icon. - Scroll down to see the Logins by Session Type panel.
This panel summarizes all sessions associated with the selected user. Click on View Details to see more information and to further filter the output.
User Accounts
View account information for an individual user:
- Select Users from the Home page, or select Explore > Users from the menu to access the Users Table.
- Select an individual user.
- Click the
 icon.
icon.
You can also view the accounts view for a user after clicking a name for more information from the Peer Groups page.
Review the account information associated with a user to determine if the user has multiple accounts, or whether they have any privileged accounts. If a user has multiple accounts, you can view the account type, Active Directory (AD) group memberships, and account status for each account.
For more information, see Review Peer Groups in Splunk UBA.
| Review current threats | Review current user activity |
This documentation applies to the following versions of Splunk® User Behavior Analytics: 5.2.0, 5.2.1, 5.3.0, 5.4.0, 5.4.1, 5.4.1.1, 5.4.2
 Download manual
Download manual
Feedback submitted, thanks!