Close threats in Splunk UBA
Splunk UBA threats can be manually closed or automatically closed by Splunk UBA. Closed threats might affect other components in Splunk UBA.
Closed threats fall into one of two categories:
- Threats automatically closed by Splunk UBA are marked as Closed By System.
- Threats manually closed by a user are marked as Closed By User.
When are threats Closed By System?
Threats can be automatically closed by Splunk UBA under the following circumstances:
- Upon recomputation, when Splunk UBA runs the threat rules or models each night, it is determined that a threat is no longer valid. For example, this can happen if the entity and anomaly risk scores become lower, thus making the threat no longer valid. In such cases, Splunk UBA automatically closes the threat.
- A threat rule is deleted. When this happens, all of the corresponding threats generated by that rule are deleted by Splunk UBA.
When are threats Closed By User?
Sometimes, anomalies are created that generate a threat but upon further investigation, the threat does not represent a real threat in your environment. For example:
- A department-wide password expiration, rather than brute force attack attempts, led to abnormal numbers of login failures and threat creation.
- Atypical location behavior was observed for a user, such as a user who was working remotely for a week.
In such cases, you can manually close the threat as Not a Threat.
How does closing a threat affect other Splunk UBA components?
When a threat is closed, it is kept in the database and is not deleted from Splunk UBA. If the threat is also being managed in Splunk Enterprise Security (ES) as a notable event, the status of the threat is synchronized with Splunk ES. See How threats and notables are synchronized in the Send and Receive Data from the Splunk Platform manual.
Threats closed as Not a Threat do not get raised again in Splunk UBA, meaning that a threat involving identical entities and behaviors is not generated again after you close the threat, even if those entities and behaviors remain in Splunk UBA. However, closing a threat does not affect the models in any way, so different entities with the same behavior would generate a new threat. See the table for more information.
| TImeline | Description | Threat generated |
|---|---|---|
| May 1 | A new threat is generated involving user JohnA and the devices 10.4.5.6 and 100.4.5.6. | Lateral Movement, with the threat ID 001. |
| May 2 | Upon investigation, the threat generated on May 1 was a false positive, and is marked and closed as such in Splunk UBA. No devices are allowlisted when the threat is closed, meaning that threats involving the same devices can be raised again. See How to close a threat in Splunk UBA. | None. |
| May 3 | The same lateral movement behavior is seen with a different user JaneA and the devices 10.4.5.6 and 100.4.5.6. Because a different user is involved, a new threat is generated. | Lateral Movement, with the threat ID 002. |
| May 4 | Upon investigation, the threat generated on May 3 is also not a threat because the device 10.4.5.6 is a trusted multi-host device and should be allowlisted. The threat is closed by allowlisting the device 10.4.5.6. | None. |
| May 5 | Addtional lateral movement behavior is seen in the system with user JohnA and the devices 10.4.5.6 and 100.4.5.6. Because the entities and behavior involved are the same as the threat that was closed earlier, no new threat is raised. | None. |
| May 6 | Lateral movement behavior patterns are detected for user JohnB and the device 10.4.5.6. Because this device was allowlisted on May 4, no threat is generated by this activity. | None. |
| May 6 | Lateral movement behavior patterns are detected for user JaneB and the devices 10.4.5.6 and 100.4.5.6. Since the device 100.4.5.6 is not allowlisted and JaneB is a new entity, a threat is generated for this activity, even though device 10.4.5.6 is allowlisted. | Lateral Movement, with the threat ID 003. |
Closing a threat affects user and device scores when the entity scoring process is run, once per day. See /var/log/caspida/system/EntityScoreUpdateExecutor.log for the log.
The audit logs in Splunk UBA are updated when a threat is closed.
How to close a threat in Splunk UBA
Perform the following tasks to close a threat in Splunk UBA:
- Open the Threat Details for the threat.
- Select an Action of Not a Threat.
- Additional options vary depending on the specific threat. Any threat containing an external device or domain will have the following options. Select one to close the threat. If the threat does not contain any external devices or domains, skip this step.
Desired result Description After investigating, you want to close the threat as resolved or as a false positive. Selecting this option does not allowlist any devices or domains. Click The threat has been resolved or is false positive. You want to close the threat by allowlisting one or more external devices. - If the threat contains one external device, click The device <device_name> should be allowlisted to add the device to the device allowlist.
- If the threat contains multiple external devices, click One or more devices should be allowlisted, then select the devices you want to add to the device allowlist.
You want to close the threat by allowlisting one or more external domains. - If the threat contains one external domain, click The domain <domain_name> should be allowlisted to add the domain to the domain allowlist.
- If the threat contains multiple external domains, click One or more domains should be allowlisted, then select the domains you want to add to the domain allowlist.
- (Optional) Enter some comments about why you are closing this threat.
- Click OK.
How to delete multiple threats of a certain type based on the score
You can use the clean_threats.sh script to delete multiple threats. Perform the following steps:
- Determine the threat ID of the score you want to delete.
- Open any threat that you want to delete.
- Find the ID by copying the last portion of the URL to a Base64 decoder.
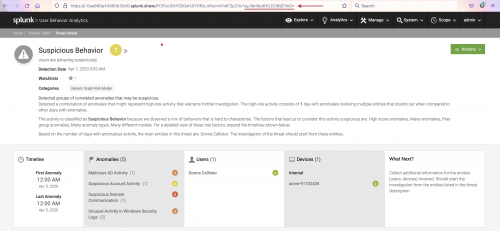
- In this example, pasting
eyJlbnRpdHlJZCI6IjE1In0=into the Base 64 decoder provides the following result:{"entityId":"15"}
The result format is formatted as{"entityId": <threat id number>}meaning 15 is the threat ID in this example.
- Determine the threat type for this specific ID. Replace
ThreatIDwith the value you determined in the previous step as shown in the following command:
psql -d caspidadb -c "select threattype from threats where id='<ThreatID>';" - Input the threat type into the clean-up script as follows. In this example, Suspicious Behaviour threats have a threat type of "Insider". The
-tstands for threat type, and the-sstands for the score:
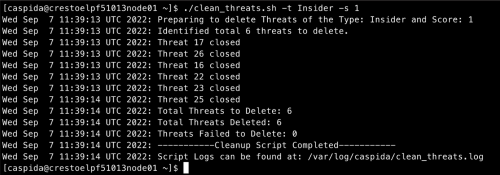
/opt/caspida/bin/clean_threats.sh -t Insider -s 1 - The script deletes the threats matching the provided threat type and score as shown in the following example:
| Delete anomalies in Splunk UBA | Investigate and monitor domains |
This documentation applies to the following versions of Splunk® User Behavior Analytics: 5.2.0, 5.2.1, 5.3.0, 5.4.0, 5.4.1, 5.4.2
 Download manual
Download manual
Feedback submitted, thanks!