Configure threat lists
The Splunk App for Enterprise Security includes third-party data sources that provide a list of hosts known to serve undesirable content.
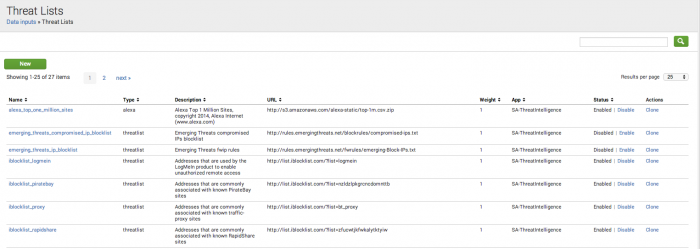
Review the threat lists
The Splunk App for Enterprise Security comes with pre-configured threat lists. Some threat lists are enabled by default.
- Browse to Configure > Data Enrichment > Threat Lists, and review the Description field in all enabled lists for their intended use-case.
- Enable or disable the lists that correspond to the security domain, data sources, and defined use-case for the Enterprise Security installation.
- Use the Threat List Settings editor to configure a proxy server for a threat list, to edit an existing threat list, or change threat list update information.
- Use the Threat List Audit dashboard to review the status of all threat lists.
Threat list settings
Use Threat Lists to configure the settings for your threat list. Browse to Configure > Data Enrichment > Threat Lists. Select the threat list name link to view the settings.
| Threat List Settings |
|
|---|---|
| Parsing Options |
|
| Download Options |
|
| Proxy Options: (Optional) |
|
Edit a threat list
Use the Threat List Settings editor to modify information about an existing threat list.
To edit a threat list:
1. Go to Configure > Data Enrichment > Threat Lists and click the name of the threat list you want to edit.
2. In the Threat List Settings editor, make changes to the fields describing the threat list.
3. Save any changes when you are done.
- To allow non-admin users to edit threat lists, see the topic on "Custom capabilities" in this manual.
Add a new threat list
Use the Threat List Settings editor to add a new threat list to your deployment.
To add a new threat list:
1. Go to Configure > Data Enrichment > Threat Lists.
2. Click New to open the Threat List Settings editor.
3. Enter the information about the threat list.
4. Save the changes when you are done.
Add a static threat list
A static threat list is a CSV file with the format of description, ip, description, domain, or description, url.
The description field is a free form textual description. It can be the same for all entries in a threat list or it can be unique for each entry.
| Configure lists and lookups | Configure correlation searches |
This documentation applies to the following versions of Splunk® Enterprise Security: 3.1, 3.1.1, 3.2, 3.2.1, 3.2.2
 Download manual
Download manual
Feedback submitted, thanks!