Dashboard overview
The Splunk App for Enterprise Security provides a range of dashboards that form a high-level overview of all security threats on your system.
Default dashboards
This section covers the dashboards that are visible by default as part of the Splunk App for Enterprise Security. You can modify which dashboards are displayed and the menus in which they appear.
By default, the Splunk App for Enterprise Security dashboards displayed are:
- Security Posture
- Incident Review
- Predictive Analytics
- Entity Investigator dashboards
- Advanced Threat
- Security Domain dashboards: Access, Endpoint, Network,Identity
- Audit
The Search dashboards contain Dashboards, Reports, Pivot, and Search.
For a complete list of available dashboards included with the Splunk App for Enterprise Security, see "Dashboards" in the Splunk App for Enterprise Security Installation and Configuration Manual.
Security Posture and Incident Review dashboards
Two dashboards provide a high-level view of your deployment. These dashboards use notable events, aggregated events that identify patterns or security issues that may require investigation. Notable events are generated by real-time or scheduled searches called correlation searches. Initially, you will not see any content in these dashboards; content will appear when the underlying correlation searches have completed.
- Security Posture: "Are things OK?" The primary Enterprise Security dashboard. This provides a high-level visual summary and trend indication of the notable events across all of your deployment in the past 24 hours. This dashboard is continuously updated by real-time searches.
- Incident Review: "What should we do now?" Shows the details of all notable events identified within your deployment. From this dashboard you can monitor notable event activity, filter events by criteria such as urgency or domain, or manage the status of the notable events.
Domain dashboards
The domain dashboards give visibility into the three primary domains of security: Access protection, Endpoint protection, and Network protection, and provide the following functionality:
- Access: Provides information about authentication attempts and access control related events (login, logout, access allowed, access failure, use of default accounts, and so on).
- Endpoint: Includes information about endpoints such as malware infections, system configuration, system state (CPU usage, open ports, uptime, and so on), patch status and history (which updates have been applied) and time synchronization information.
- Network: Includes information about network traffic provided from devices such as firewalls, routers, network-based intrusion detection systems, network vulnerability scanners, proxy servers, and hosts.
Each domain includes summary dashboards that give an overview of important security areas along with search dashboards that allow you to drill down into more detailed information. Dashboards are categorized as centers, profilers, or search dashboards.
- Centers (for example, "Malware Center", "Asset Center", and so on): Provide an overview of the security events for a given domain. These overview dashboards identify significant trends or show relevant issues that may require attention.
- Profilers (for example, "Patch / Update Profiler", "Vulnerability Profiler"): Provide information about a particular user or object. For example, the patch /update profiler provides information about which devices have been updated with a particular patch or software update.
- Analysis (for example, "Traffic Size Analysis", "HTTP User Agent Analysis"): Provide statistical information about data and events being monitored. Using a variety of custom filters, you can locate and identify anomalous events to investigate.
- Search dashboards (for example, "Proxy Search", "Vulnerability Search"): Search dashboards provide rapid access to domain-specific search tools, without requiring advanced knowledge of the Splunk search language.
Some Splunk App for Enterprise Security dashboard panels are populated by saved searches or time-independent searches.
This behavior applies these dashboard panels:
- Access Center > Notable Access Events (saved search)
- Malware Center > Key Malware Statistics (time-independent)
- Traffic Center > Port and Protocol Profiler (saved search)
For informational purposes, these panels ignore top-level filters.
Supporting dashboards
Additional Splunk App for Enterprise Security dashboards help monitor and investigate the security of the infrastructure. These dashboards provide the following functionality:
- Identity: Review identities associated with the network and their associated activities. Also review asset lists and see a summary of all network sessions. (To get optimal functionality from Enterprise Security, create or import an asset list and an identities list associated with the network. See the Enterprise Security Installation and Configuration Manual for more information.)
- Audit (for example, "Incident Review Audit", "Suppression Audit", "Forwarder Audit", "Index Audit", and so on): Provide information about Splunk's own operational data including: forwarder auditing, index auditing, search auditing, and data protection. Use this dashboard to track resource consumption, organizational activity, and analyst effectiveness. These are potentially critical components to a security organization.
Common dashboard features
The domain dashboards include a number of features that are common to many of the dashboards.
Note: Dashboard filters may not apply to all panels within a dashboard.
Dashboard filters
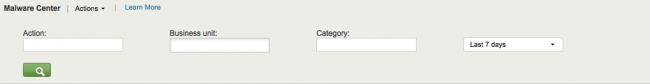
Many dashboards have a filter bar to restrict the view on the current dashboard to events that match the selected criteria. Selections apply to the current dashboard only; they do not affect other dashboards in Enterprise Security. The following is a typical filter bar.
To use the filter, make your selections and/or enter the desired text, then click the magnifying glass (![]() ) to run the search. For instance, many dashboards support selection of Business Unit or Category, which allows security managers and analysts to compare posture and patterns between different organizational units.
) to run the search. For instance, many dashboards support selection of Business Unit or Category, which allows security managers and analysts to compare posture and patterns between different organizational units.
| Filter | Description |
|---|---|
| Action | Filter based on the status of the action; choices depend on the context: When status is related to the action's source: |
| Business Unit | Filter based on the business unit of the host. Enter the text string to match the business unit. Use the asterisk (*) wildcard to match any number of characters. For example, a* matches america and asia. Match is case-insensitive; all text values must be lowercase.
Note: Business Unit is a free form field implemented using the Splunk for Enterprise Security asset list and identities list. To use this filter, the asset list must be configured for the deployment. See the Enterprise Security Installation and Configuration Manual for more information. |
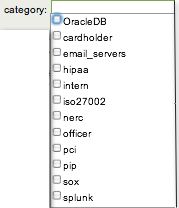
| Category | Filter based on the categories to which the host belongs. It is possible to filter on multiple categories by selecting each category to include.
|
| Time range picker | Filter by time range. Select the time range from the drop-down or click Custom time to specify a start and end time. |
Dashboard drill down
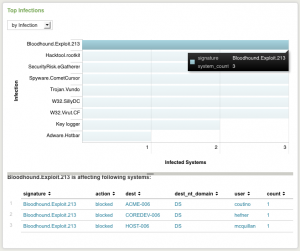
Use the alerts and charts on the Enterprise Security dashboards to drill down into the underlying events by clicking on a point or segment on a chart or a row in a table. Each domain also includes a custom search dashboard to help search for events related to that domain.
Enterprise Security uses the Splunk drill down feature to see the details behind the tables and charts in dashboards.
View full results
The View full results link at the bottom of a panel displays the Search dashboard. Use this to search for the underlying events that are aggregated on the panel.
To use this link:
1. Go to the panel displaying the events of interest.
2. Click View full results at the bottom of the panel.
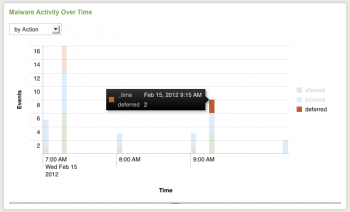
Drill-down from charts
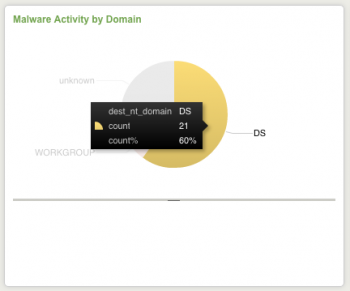
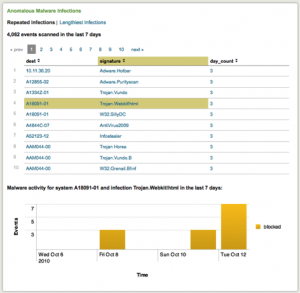
To use data drill-down on charts, click on a segment or point on a chart to view the related events - in this case, events that match the underlying search for the panel and also match the field value clicked. For example, for Malware Activity by Domain, click on a domain in the chart and a search window is displayed with a search for all malware activity in that domain.
To use data drill-down from a chart:
1. Navigate to the chart containing the events.
2. Click on a segment, bar, or point on the chart. Drill-down displays a domain-specific search dashboard, the general search dashboard, or shows a second panel underneath the first.
3. In some cases, drill-down displays a second panel underneath the first. In this case, it is possible to drill down further by clicking on a row and/or column as described in the next section.
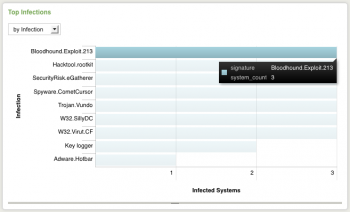
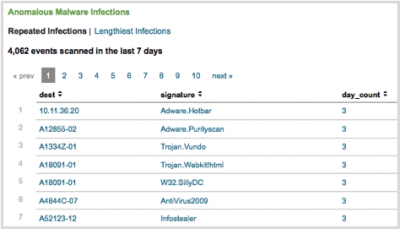
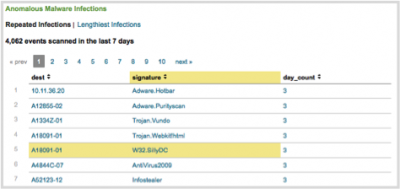
Drill-down from tables
Click on a segment or point on a table to view the related events:
1. Navigate to the table containing the events.
2. Click on a row in the table. Drill-down displays a domain-specific search dashboard, the general search dashboard, or shows a second panel underneath the first.
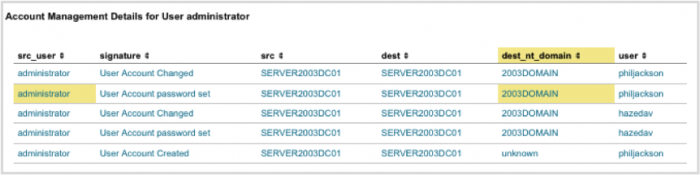
For some tables, drill-down can select two related items for the search. For example, in the following table, "Account Management Details for User Administrator", clicking administrator at the beginning of the row shows all events where the src_user is administrator. Clicking 2003DOMAIN in a row that begins with administrator shows all events where the src_user is administrator and the dest_nt_domain is 2003DOMAIN.
3. If drill-down displays a second table underneath the first, drill down further by clicking on a row and/or column.
4. In other cases, drill-down displays a chart showing the results for the selection.
| Access the Splunk App for Enterprise Security | Key indicators |
This documentation applies to the following versions of Splunk® Enterprise Security: 3.1, 3.1.1
 Download manual
Download manual
Feedback submitted, thanks!