More Network dashboards
These additional network dashboards can be found under Security domains > Network in the Splunk App for Enterprise Security.
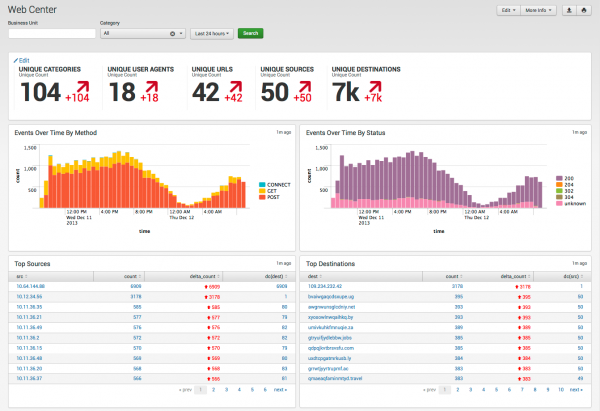
Web Center
The Web Center dashboard profiles web traffic events gathered from proxy servers and indexed by Splunk.
Note: Previous versions of the app included this information in the Proxy Center dashboard.
Relevant data sources
Relevant data sources for the Web Center dashboard include web and proxy data from devices that collect web and proxy data, along with data indexed in Splunk.
How to configure this dashboard
1. Index relevant data sources from a device, application, or system in Splunk.
2. Map the data to the Web data model. See the Common Information Model Add-on Manual for more information. The Common Information Model fields bunit and category are derived by automatic identity lookup, and do not need to be mapped directly.
3. Tag your data with "web" AND "proxy".
Dashboard description
Web Center dashboard data is derived from the Web data model and accelerated automatically.
To verify that web data is present, use this search:
| datamodel Web Web search
To verify that events are being accelerated by the data model correctly, use this search (be careful not to search across all time):
| tstats summariesonly=true count from datamodel=Web by user
For more information on distributed namespaces, see "Tscollect" and "Data Model" in the Splunk Search Reference Manual for more information about data models and namespaces.
Useful searches/Troubleshooting
| Troubleshooting Task | Search/Action | Expected Result |
|---|---|---|
| Verify that you have data from your network device(s) | sourcetype=<your_sourcetype_for_your_data> | Returns data from your network device(s). |
| Verify that proxy data is indexed in Splunk | tag=web tag=proxy or | datamodel Web Web search |
Returns all proxy data from your device(s) |
| Verify that proxy data is normalized to the Common Information Model properly | | datamodel Web Web search |table status action http_method http_content_type http_user_agent src dest | Returns a list of events and the specific web and proxy data fields populated from your device(s) |
Additional Information
For more information about using the Web Center dashboard, see "Web Center" in the Splunk App for Enterprise Security User Manual.
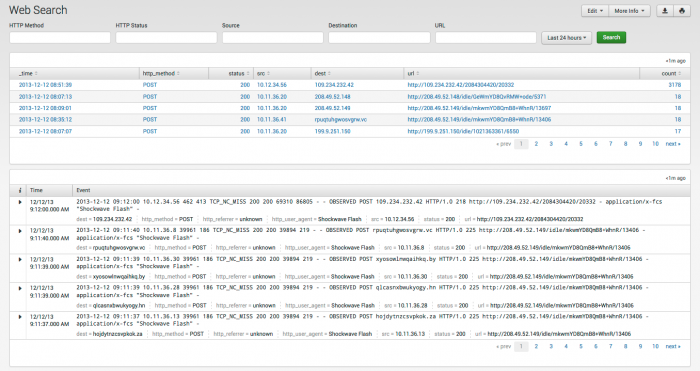
Web Search
Use the Web Search dashboard to search for web-related events and find detailed web log information, such as the list of sites visited by an individual or all of the individuals that visited a particular site.
Web Search is similar to the Splunk Search dashboard, but provides an additional selection bar filter your search for web and proxy events. Use the fields to filter results and narrow your search. Click an item to drill down to the raw data.
Relevant data sources
Relevant data sources for the Web Search dashboard include web and proxy data from devices that collect web and proxy data, along with data indexed in Splunk.
How to configure this dashboard
1. Index relevant data sources from a device, application, or system in Splunk.
2. Map the data to the Web data model. See the Common Information Model Add-on Manual for more information. The Common Information Model fields bunit and category are derived by automatic identity lookup, and do not need to be mapped directly.
3. Tag your data with "web" AND "proxy".
Dashboard description
Web Search dashboard data is derived from the Web data model and accelerated automatically.
To verify that web data is present, use this search:
| datamodel Web Web search
To verify that events are being accelerated by the data model correctly, use this search (be careful not to search across all time):
| tstats summariesonly=true count from datamodel=Web by user
For more information on distributed namespaces, see "Tscollect" and "Data Model" in the Splunk Search Reference Manual for more information about data models and namespaces.
Useful searches/Troubleshooting
| Troubleshooting Task | Search/Action | Expected Result |
|---|---|---|
| Verify that you have data from your network device(s) | sourcetype=<your_sourcetype_for_your_data> | Returns data from your network device(s). |
| Verify that web data is indexed in Splunk | tag=web tag=proxy or | datamodel Web Web search |
Returns all web and proxy data from your device(s) |
| Verify that web data is normalized to the Common Information Model properly | | datamodel Web Web search| table bytes_in bytes_out action status src dest http_content_type http_method http_referrer http_user_agent url user | Returns a list of events and the specific proxy data fields populated from your device(s) |
Additional Information
For more information about using the Web Search dashboard, see "Web Search" in the Splunk App for Enterprise Security User Manual.
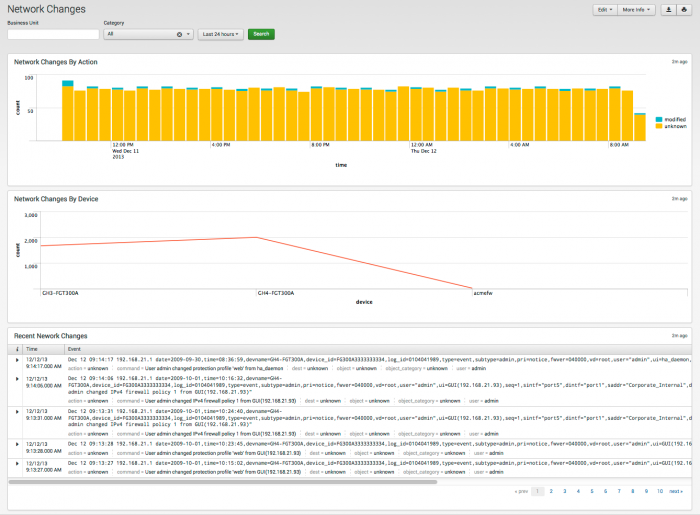
Network Changes
Use the Network Changes dashboard to track configuration changes to firewalls and other network devices in the environment.
Relevant data sources
Relevant data sources for the Network Changes dashboard include data from the Splunk change monitoring system, along with system log files and devices that detect network or endpoint changes in the environment.
How to configure this dashboard
1. Index relevant data sources from a device, application, or system in Splunk.
2. Map the data to the Change Analysis data model. See the Common Information Model Add-on Manual for more information. The Common Information Model fields bunit and category are derived by automatic identity lookup, and do not need to be mapped directly.
3. Tag your data with "network" AND "change".
Dashboard description
Network Changes dashboard data is derived from the Change_Analysis data model and accelerated automatically.
To verify that network change data is present, use this search:
| datamodel Change_Analysis Network_Changes search search
To verify that events are being accelerated by the data model correctly, use this search (be careful not to search across all time):
| tstats summariesonly=true count from datamodel=Change_Analysis by user
For more information on distributed namespaces, see "Tscollect" and "Data Model" in the Splunk Search Reference Manual for more information about data models and namespaces.
Useful searches/Troubleshooting
| Troubleshooting Task | Search/Action | Expected Result |
|---|---|---|
| Verify that you have data from your network device(s) | sourcetype=<your_sourcetype_for_your_data> | Returns data from your network device(s). |
| Verify that local network change data exists | tag=network tag=change or | Change_Analysis Network_Changes search |
Returns local network change data |
| Verify that network data is normalized to the Common Information Model properly | | Change_Analysis Network_Changes search |table dvc action user command | Returns a list of events and the network change data fields populated from your device(s) |
Additional Information
For more information about using the Network Changes dashboard, see "Network Changes" in the Splunk App for Enterprise Security User Manual.
| Endpoint dashboards | Identity dashboards |
This documentation applies to the following versions of Splunk® Enterprise Security: 3.1, 3.1.1, 3.2, 3.2.1, 3.2.2
 Download manual
Download manual
Feedback submitted, thanks!