Asset management
Asset management allows events to be correlated with assets so that the location and priority of the asset can be determined.
What does asset management do?
Asset management provides additional information about the source and targets of events. This information can be used to correlate multiple events to a single host, identify the location of the host, determine whether the host is subject to regulatory compliance, etc. Specifically, asset management provides the following:
Prioritization
The same type of events on two different systems may not deserve the same level of attention; a medium severity event against a desktop machine is less urgent than the same issue against an externally facing web-server that processes credit card information. Asset management allows an urgency to be computed based on the priority of hosts and assign higher urgency to high priority assets.
Categorization
Asset management allows information about the assets to be added to events. For example, identity management can look up the source of an event and find the location of the asset, indicate whether the source is subject to PCI compliance or identify the owner.
Normalization
Asset management allows hosts to be normalized and determine whether two events relate to the same host. For example, two events may use different information to refer to the host; one event may use an IP address and another event may use a DNS name. Identity management can determine that both of the events are for the same host by recognizing that the IP address and DNS name are for the same host.
How assets work
Asset management provides fields in events to designate the asset involved.
This feature can identify events for assets, and identify assets for an event. It will try to use session information to help match events to an asset and a session to an asset.
What is an asset?
An asset represents a host or a range of hosts (such as a subnet). An asset may have multiple identification fields such as a DNS name, an IP address, and a MAC address. Asset management will consider each of these fields in order to match the asset with the respective events.
Additionally, assets include information that describes the location and business unit of the asset. Assets can also be put into categories that define the purpose of the asset or the functional area it is contained within.
How asset fields are used
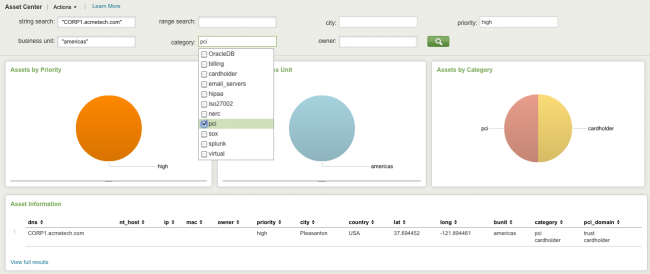
The Asset Search option allows you to search for assets from anywhere that an asset is found in a field context menu. These searches use the Asset and Identity Search tool to look for any match in an asset-related field.
Asset-related fields are:
dest src dest_ip src_ip dest_dns src_dns dest_mac src_mac dest_nt_host src_nt_host
For example, suppose there is an entry in the asset list with CORP1.acmetech.com in the DNS column. To simplify this example for readability and compactness, only a subset of the fields from the asset list is shown:
Example with sample fields : ip,mac,nt_host,dns,owner,priority,lat,long,bunit,category
Sample asset:
,,,CORP1.acmetech.com,dmaradona@acme.com,high,41.040855,28.986183,americas,
pci|cardholder
For any event where the host field has the value CORP1.acmetech.com, Splunk for Enterprise Security looks for CORP1.acmetech.com in the asset list at search time. When it finds a match, Splunk for Enterprise Security generates additional fields from the information in the asset list, including the following:
host_owner dmaradona@acme.com host_priority high host_lat 41.040855 host_long 28.986183 host_bunit americas host_category pci|cardholder
These fields are used in the following ways:
- If a notable event is created based on this host, for example, if the host has a high number of infections, then the following fields are used:
- a. The
priorityfield (high) is combined with the severity of the search to create the urgency for the notable event.
- b. If there is only one host for the notable event, the notable event is marked on the map in the Notable Events by Geography panel on the Security Posture dashboard using the
latandlongfields. However, if multiple hosts contribute to the notable event - for example, a high number of instances of the same infection on different hosts - no single location can be determined and the notable event is not marked on the map.
- The
bunitandcategoryfields are used for the filters on the domain and supporting dashboards. For example, our event would be included in a restricted view with this filter:
Note: Categories also rely on the category list. See "Category list" in the Installation and Configuration Manual for more information.
- For example, if there is a problem with the host and you wish to notify the asset owner, you can find the owner by looking at the asset list in Splunk for Enterprise Security (Identity > Asset Center) or using the Interactive Field Extractor.
How assets are identified
Splunk App for Enterprise Security automatically performs an asset lookup whenever there is a value in the host, orig_host, src, dest, or dvc field. For each one of these fields, the app creates new fields that contain the asset information. Because an event can have values for more than one of these fields, the name of the generated field is prepended with the name of the field that contains the asset; for example, the generated priority field for a src is called src_priority. This disambiguation does not affect menus, but can be useful to know in searches. When a search is run and an event includes data in one or more of the asset fields (host, orig_host, src, dest, dvc), Splunk for Enterprise Security looks up the asset in the asset list. The asset list includes four columns that can contain identifying information for the asset. The Splunk App for Enterprise Security attempts to identify the asset based on following order of precedence:
- ip: An IP address (e.g., 1.2.3.4) or a range of IP addresses (e.g., 192.168.15.9-192.169.15.27 or 2.0.0.0/8).
- mac: A Media Access Control (MAC) Address (e.g., 00:25:bc:42:f4:60) or range of MAC Addresses (e.g., 00:25:bc:42:f4:60-00:25:bc:42:f4:6F)
- dns: DNS name
- nt_host: Windows Machine Name (also known as the NetBIOS machine name)
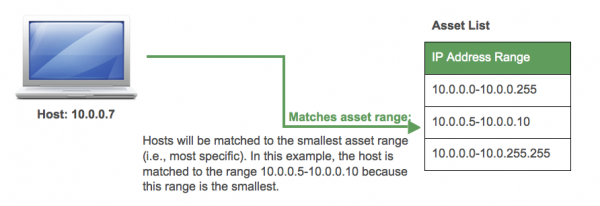
The asset lookup attempt stops as soon as it gets a match. For example, if the asset matches an IP, then asset lookup won't try matching on MAC addresses, DNS names, or machine names. Asset lookup only matches a single asset and does not combine data from all potential matching assets. For IP addresses and MAC addresses, asset lookups attempt to find the most specific address if multiple ranges match. For example, if two IP ranges match a given host, asset lookup uses the smaller (most specific) of the ranges (see below for an example). When a single IP address or MAC address is available, it is used, since it is an address range of one.
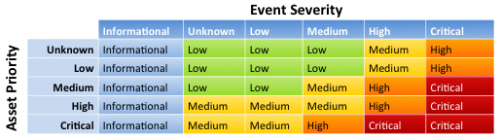
How the urgency of an event is assigned
The severity of the event and the priority are combined to generate the urgency of an event. The urgency allows events to be weighted according to the asset, thus causing events against higher priority assets to be treated with higher urgency. The urgency is calculated per the table below:
Asset management allows events to be correlated with assets so that the location and priority of the asset can be determined.
Important: Any correlation search that uses the calculated severity level will always show a reduced urgency if an asset is unknown, or if the assigned priority of an asset is unknown. To change the urgency calculation defaults in the Enterprise Security app, go to Configure > Data Enrichment > Lists/Lookups. Choose the Urgency Levels configuration. An editable, color coded table representing the urgency lookup file will be displayed. Review the assigned urgency in any row where the priority or severity is listed as "unknown." Edit the table and increase the urgency to a higher level as desired. Save the changes when the editing is complete.
Correlation searches and calculated severity
Correlation searches will not use the calculated severity described if the events being searched contain a severity value (that is, a field named "severity"). If this is not the desired behavior, remove the severity field in the search. When the field is removed, the calculated severity for the correlation search will be used.
Add the following to the correlation search:
fields - severity
To do this go to Configure > Correlation Searches and click on the search to open the Correlation Search editor.
Make this change to the Search field of the selected correlation search:
`authentication` | fields - severity
Click Save.
The "authentication" search now ignores the severity field.
Customizing Assets
To make immediate modifications to an existing list, go to Configure > Data Enrichment > Lists/Lookups, select the Assets lookup and change the values. The editor does not validate input.
Alternatively, the file may be installed to the following path: $SPLUNK_HOME/etc/apps/SA-IdentityManagement/lookups/assets.csv.
Important: Any CSV file must use Unix line endings.
It is recommended that you update the list periodically in order to ensure that Splunk for Enterprise Security has reasonably up-to-date information. Generally, it is recommended that the list be updated at least every quarter.
Automatic asset updates can be managed using a combination of scripted inputs and custom search commands (written in Python). The implementation details depend on the technology that contains the asset information and is beyond the scope of this document.
Splunk automatically loads the asset list at search time and does not need to be restarted. To learn more about the asset list, see "Asset fields" in the Splunk App for Enterprise Security Installation and Configuration Manual.
Changes to Assets and Identities
The Asset and Identity correlation system relies on static or dynamically created lookup files to provide the fundamental information about devices and users the environment. A new configuration page Identity Management is available to define and enable multiple Asset and Identity lists in the Splunk App for Enterprise Security and can be found under Configure > Identity Management . Use Identity Management to view, modify, or create Asset or Identity lists.
The contents of all lookups enabled in Identity Management are merged by a modular input that is scheduled to run every 5 minutes. The result is a new set of expanded, cross-referenced lookup files named assets_by_str.csv, assets_by_cidr.csv and identities_expanded.csv that are used for the Asset and Identity correlation system.
Enabling, disabling, or changing the configuration of an Asset or Identity lookup stanza in Identity Management will begin a merge at the next scheduled interval.
A link to the lookup source is available on the Identity Management page that allows users to edit information directly in Asset or Identity files. Changes made to a source asset or identity lookup file will be reflected in search results following the next scheduled merge.
Force a merge
To perform an immediate merge of updates to the Assets and Identities, the modular input can be run directly from the CLI. Calling the input script from the CLI requires the $SPLUNK_HOME environment variable to be set.
$SPLUNK_HOME/bin/splunk cmd splunkd print-modinput-config identity_manager | $SPLUNK_HOME/bin/python $SPLUNK_HOME/etc/apps/SA-IdentityManagement/bin/identity_manager.py --username=admin
Credentials are required. The user will be prompted to provide a password for the --username defined.
When the identity manager input is triggered, it will evaluate all enabled lookups and check for changes. If no changes have been made to any lookups since the last run, the identity manager input will not regenerate the merged lookup files.
Verify expansion process
To verify that the expansion process has completed, search the internal index to show the last time the merge occurred:
index=_internal source=*python_modular_input.log "Updated: target lookup table"
To find successive runs where no merging was required:
index=_internal source=*python_modular_input.log "Updated: target lookup table" OR "No merging required"
The most common reason for failure is incorrect formatting or invalid data in the assets.csv or identities.csv lookup files used as the source.
Guidelines for expansion
The following table provides a guideline for how long asset and identity expansion will take for assets.csv or identities.csv files of a certain size:
| Number of entries | Time to expand |
|---|---|
| < 10000 entries | less than 2 minutes |
| 10000 to 100000 entries | 2 to 3 minutes |
| 100000 to 500000 entries | 5 to 7 minutes |
The exact time required for the Asset and Identity table merge to complete will vary depending on the performance of the storage system.
| Asset and Identity correlation | Identity correlation |
This documentation applies to the following versions of Splunk® Enterprise Security: 3.1, 3.1.1, 3.2, 3.2.1, 3.2.2, 3.3.0, 3.3.1, 3.3.2, 3.3.3
 Download manual
Download manual
Feedback submitted, thanks!